A sophisticated threat actor has been conducting a persistent phishing campaign against United States educational institutions since April 2025, leveraging the open-source Evilginx framework to bypass multi-factor authentication (MFA).
The campaign, which has targeted at least 18 universities to date, utilizes adversary-in-the-middle (AiTM) techniques to intercept login credentials and session cookies by mimicking legitimate single sign-on (SSO) portals.
The investigation began following a tip regarding recurring attacks on a specific student SSO portal.
Analysis confirmed the use of Evilginx (likely version 3.0), a widely adopted toolkit used by cybercriminals to proxy legitimate login flows in real time.
Unlike standard credential harvesting sites, Evilginx acts as a reverse proxy between the victim and the legitimate service.
This allows the attacker to capture the session token generated after a successful MFA challenge, granting them unauthorized access without needing the victim’s second factor again.
Evasion and Technical Methodology
The campaign demonstrates a high level of operational security designed to frustrate traditional detection methods.
The attackers employ “phishlets” configuration files that define how the proxy interacts with specific target sites to generate dynamic phishing URLs.
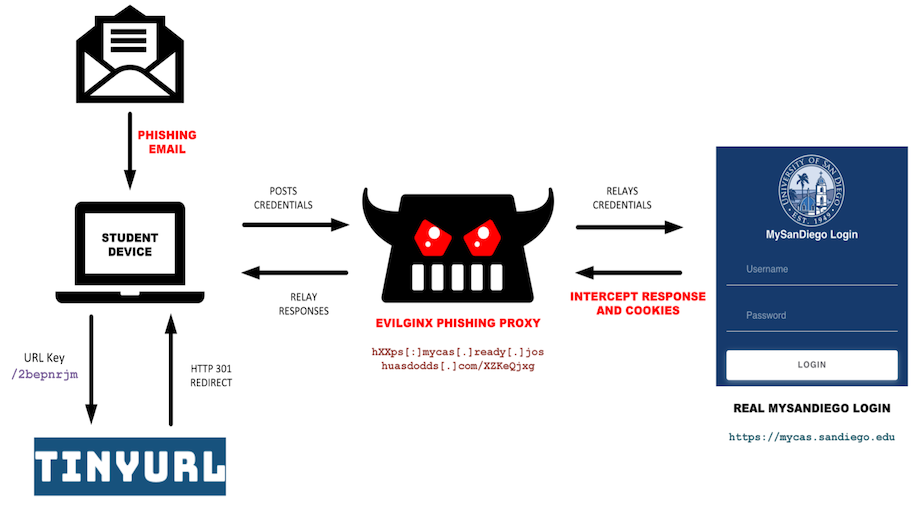
These URLs are delivered via personalized emails containing TinyURL short links. To minimize exposure, the phishing links are configured to expire within 24 hours.
Furthermore, the threat actor conceals their hosting location behind Cloudflare proxies and utilizes short-lived subdomains.
The URL structure consistently features a subdomain specifically crafted to impersonate the target university’s brand, followed by a URI consisting of eight random, case-insensitive alphabetic characters.
These tactics, combined with Evilginx’s inherent resistance to standard security scanners and front-end code inspection, make the attacks difficult to detect using conventional URL analysis or HTML signature matching.
Scope of Targets and Infrastructure
Despite the ephemeral nature of the phishing URLs, traces of the activity persisted in passive DNS records. Researchers identified a pattern where the attacker utilized subdomain labels matching legitimate service domains.
For example, one attack vector involved the subdomain shibbolethmainrit[.]fiuy[.]weddingsarahetemmanuel[.]com, which was designed to impersonate the Rochester Institute of Technology’s Shibboleth identity management login page (shibboleth.main.ad.rit.edu).
By analyzing these DNS patterns, researchers uncovered a total of 67 domains owned by the actor. The infrastructure was initially hosted on dedicated servers via GoDaddy and NameCheap before migrating to Cloudflare.
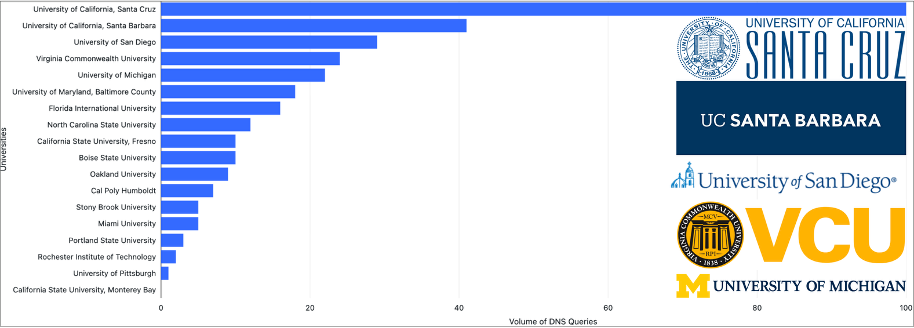
The campaign officially began on April 12, 2025, targeting the University of San Diego, with volume increasing significantly mid-year.
The most heavily targeted institutions include the University of California Santa Cruz, University of California Santa Barbara, University of San Diego, Virginia Commonwealth University, and the University of Michigan.
However, the reliance on domain names remains a critical choke point for attackers. While front-end inspection struggles against reverse-proxy attacks, the correlation of initial web server fingerprinting with extensive DNS query analysis successfully unveiled the malicious infrastructure.
New targets continued to appear as recently as November 16, 2025, with the addition of the University of Maryland, Baltimore County.
The low detection rates associated with this campaign highlight the evolving danger of tools like Evilginx Pro, which now incorporate advanced features like JA4 fingerprinting to filter bots and wildcard TLS certificates.
This case underscores that passive DNS monitoring remains one of the most effective methods for pre-emptively identifying and blocking AiTM infrastructure before it compromises organizational data.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
