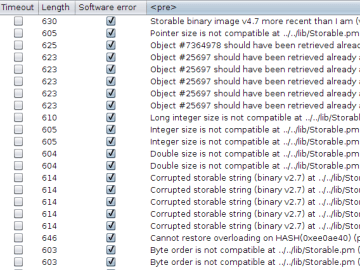
Deserialization in Perl v5.8 During a pentest, I found an application containing a form with a hidden parameter named “state”….
In February, attackers from the Russia-based BlackCat ransomware group hit a physician practice in Lackawanna County, Pennsylvania, that’s part of…
Businesses from all industries are aware of the benefits of cloud computing. Some organizations are just getting started with migration…
March has arrived and is roaring like a very confused lion, at least in the northern hemisphere. And much like…
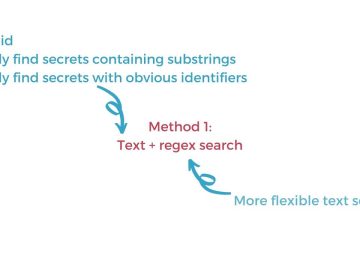
Scanning for hardcoded secrets in source code | Security Simplified Source link
ChatGPt is the recent development in commercial AI technology developed by OpenAI, it was launched in November 2022. Since its…
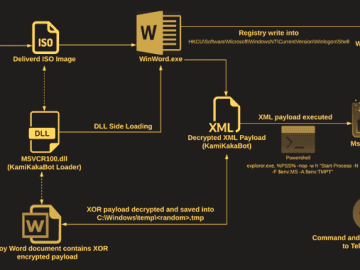
Mar 13, 2023Ravie LakshmananCyber Attack / Malware The Dark Pink advanced persistent threat (APT) actor has been linked to a…
Sustainability programmes often begin without digital technology. The baseline from a digital technology perspective includes spreadsheets and software that can…
The release of the first episode of Solo Leveling, the anime adaptation of the popular manhwa series, was eagerly being…
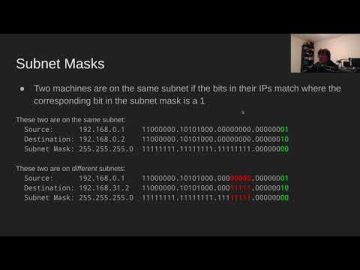
Clip: Subnets and Subnet Masks Source link
Mar 13, 2023Ravie LakshmananEnterprise Security / Privacy More than a dozen security flaws have been disclosed in E11, a smart…
Hey there, I hope you’ve been doing well! Bingo with Flair 97% of Bingo games in America happen in a…





![[tl;dr sec] #171 – AppSec and CloudSec Resilience, Audit Logs Wall of Shame, Compromised Cloud to Kubernetes Takeover [tl;dr sec] #171 - AppSec and CloudSec Resilience, Audit Logs Wall of Shame, Compromised Cloud to Kubernetes Takeover](https://image.cybernoz.com/wp-content/uploads/2023/03/tldr-sec-171-AppSec-and-CloudSec-Resilience-Audit-Logs-360x270.jpg)