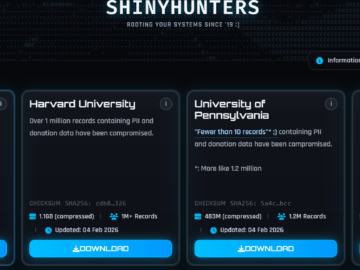
U.S. CISA adds a flaw in BeyondTrust RS and PRA to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 14,…
Fintech firm Figure disclosed data breach after employee phishing attack Pierluigi Paganini February 14, 2026 Fintech firm Figure confirmed a…
U.S. CISA adds a flaw in BeyondTrust RS and PRA to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 14,…
The widespread protests in Iran have exposed both Tehran’s brutal tactics in the streets, where state authorities have killed thousands…
Suspected Russian hackers deploy CANFAIL malware against Ukraine Pierluigi Paganini February 14, 2026 A new alleged Russia-linked APT group targeted…
Clickfix Attack DNS Hijacking spread malware A new evolution in the ClickFix social engineering campaign, which now employs a custom…
Authorities in Mexico’s Guadalupe, Nuevo León, this week unveiled four robot dogs that will be part of the security devices…
Threat Actors Exploit Claude Artifacts Google Ads A sophisticated malware campaign targeting macOS users through Google-sponsored search results and legitimate…
OpenSea 0-day Exploit Chain A threat actor is reportedly selling a purported critical severity zero-day exploit chain targeting OpenSea for…
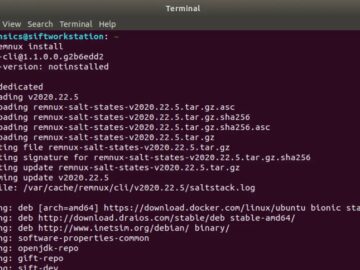
The landscape of malware analysis has taken a significant leap forward with the official release of REMnux v8. This popular…
CISA Warns Microsoft Configuration Manager SQL Injection Vulnerability CISA has issued an urgent alert about a critical SQL injection vulnerability…
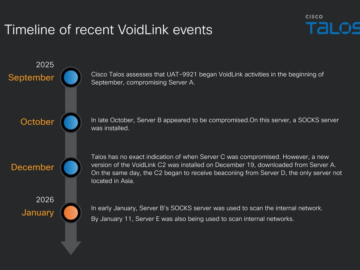
New threat actor UAT-9921 deploys VoidLink against enterprise sectors Pierluigi Paganini February 13, 2026 A new threat actor, UAT-9921, uses…