Table Of Contents A deeper look into vulnerabilities, malware, ransomware, and insider threat As 2023 unfolds, Flashpoint continues to see…
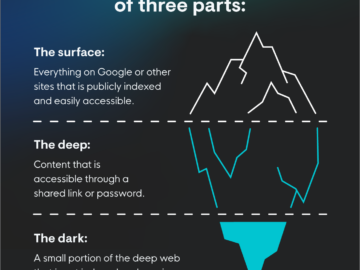
In today’s always-connected world, the line between dark and light is blurring. Well, actually, you’re still protected from finding out…
At Recorded Future, we’re constantly looking for ways to help security teams work more efficiently so they can focus their…
Picture this: it’s 4:59pm on a Friday, and you’re about to slam the work laptop shut for the weekend. You’ve…
Insurance Australia Group (IAG) has started working on ways to make its software engineering functions more AI driven, beginning with…
Flashpoint has long been known for its industry-leading data collection and finished intelligence. After two major acquisitions in 2022, we…
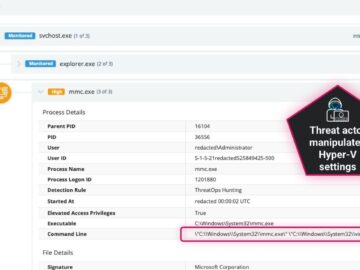
Hypervisors are the backbone of modern virtualized environments, but when compromised, they can become a force multiplier for attackers. A…
Russian state-sponsored hackers have been linked to an ongoing Signal and WhatsApp phishing campaign targeting government officials, military personnel, and…
A red teamer operating under the handle OtterHacker has publicly released M365Pwned, a pair of WinForms GUI tools designed to…
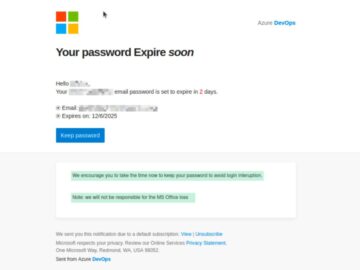
If you have been using Signal or WhatsApp for work, you might want to double-check your security settings. On Monday,…
Anthropic has filed a lawsuit to block the Pentagon from placing it on a national security blacklist, escalating the artificial…
Security awareness training (SAT) is supposed to make companies safer, but too often, it feels like just another box to…