Astrix’s Security Research Group reported a 0-day flow in the Google Cloud Platform (GCP) related to an OAuth flow exploitation. This method was termed “Ghosttoken.”
Exploiting this flaw is done through a malicious application, which can lead threat actors to gain access to the victim’s Google account forever.
One of the most important and scary facts about this attack is that it remains in stealth and completely unremovable forever. Fortunately, Google released a patch for this vulnerability on April 7, 2023.
GhostToken: Exploration and Exploitation
Threat actors can use the GhostToken vulnerability to gain access to a victim’s Google account with the help of a malicious application.
Users can use Google’s application administration page to review the applications with access to their Google accounts and remove them if necessary.
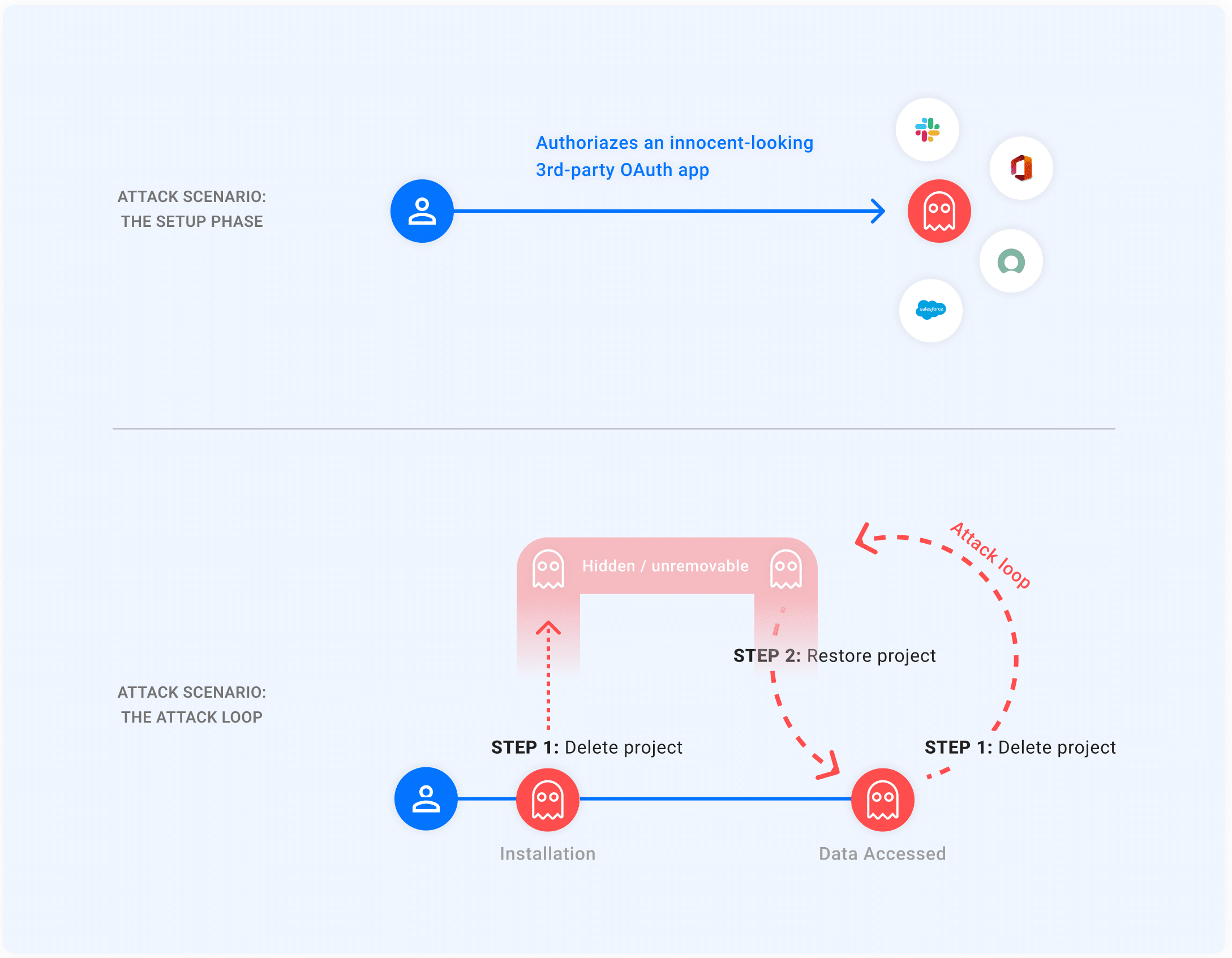
Once a user authorizes an application with the OAuth flow, the application receives a token from Google to access the user’s Google account.
However, in the case of GhostToken exploitation, once the victim authorizes the malicious application, the threat actor can hide it from the application management page, making it difficult for users to find and revoke access to the malicious application.
The victim will not have any other options but to create a new Google account.
Once the attacker gets their hands on the Google account, they can delete an email, send an email, conduct a phishing attack, delete the driver files, check calendar events, and access sensitive information.
Hiding from the Application Management Page
As per Google, if an application wants OAuth, the developers must create a GCP project to get a project identifier.
The developers also have the privilege to delete and restore the application whenever they want.
If an application in the GCP is deleted, it takes 30 days to completely delete the project, within which the application developer can restore it.
The application will not be visible on the Google Application Management Page during the deleted state.
Note: When restoring the application, it will have the same refresh token it had during creation, which can be used to restore the application completely.
Attackers use this security loophole to hide their applications from the application management page.
Mitigation
As per this vulnerability, it is hard for the user to find the malicious application since it is hidden from the application management page. However, the users can revoke access to the malicious application whenever the attacker restores it.
Unfortunately, it is a small timeframe and unpredictable when the attacker will restore the application.
Google’s Patch
As a fix, Google made the applications in the pending deletion state appear on the application management page, which the users can use to revoke the malicious application access.
Building Your Malware Defense Strategy – Download Free E-Book

Related Read:
