A Vulnerability Scanner Tools is one of the essential tools in IT departments Since vulnerabilities pop up every day and thus leaving a loophole for the organization.
The Vulnerability scanning tools help in detecting security loopholes in the application, operating systems, hardware, and network systems.
Hackers are actively looking for these loopholes to use them to their advantage. Vulnerabilities inside a network need to be identified and fixed immediately to leave your attackers at bay.
Vulnerability scanners are one right way to do this, with their continuous and automated scanning procedures they can scan the network for potential loopholes.

It is on your internet or any device, they would help the IT departments identify the vulnerability and fix it both manually and automatically.
Vulnerability scanning tools
In the latter case, a penetration tester will show the scan disguised as a hacker without him having trusted access to the corporate network.
What are the Three types of Vulnerability Scanners?
This type of scan will help organizations identify the loopholes which will allow hackers to penetrate the system without trusted permissions.
Following are the types of vulnerability scanners
- Discovery Scanning
- Full Scanning
- Compliance Scanning
What is an example of a Vulnerability Scanner?
The best Web vulnerability scanner in the market should allow you to perform both authenticated and unauthenticated types of scans to nullify network vulnerabilities among other related vulnerability scanners online
In this article, we’ll take a look at the top 10 best vulnerability scanning tools available in the market.
- OpenVAS Vulnerability Scanner
- Tripwire IP360
- Nessus vulnerability scanner
- Comodo HackerProof
- Nexpose community
- Vulnerability Manager Plus
- Nikto
- Wireshark
- Aircrack-ng
- Retina network security scanner
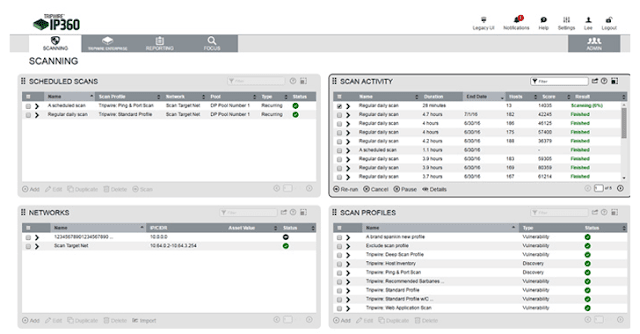
Tripwire IP360 is one of the leading Vulnerability Assessment Scanning Tools in the market, allowing users to identify everything on their network, including on-premises, cloud, and container assets.
Tripwire will allow IT departments to access their assets using an agent and agent fewer scans.
Scanning Options
It also works in integration with vulnerability management and risk management, allowing IT administrators and security professionals to have a holistic approach to security management.
| Pros | Cons |
| Easy-to-Understand Reports with a Vulnerability score | System Performance may be affected |
| Very Clear Dashboard | Pricing suits only Enterprises |
| Database to store reports |
OpenVAS vulnerability scanner is the best vulnerability scanner tool that will allow IT departments to scan servers and network devices, thanks to its comprehensive nature.
These scanners will look for an IP address and check for any open service by scanning through the open ports, misconfiguration, and vulnerabilities in the existing facilities.
Once the scan is complete, an automated report is generated and sent as an e-mail for further study and rectification.
Scanning Options
OpenVAS can also be operated from an external server, giving you the hacker’s perspective, thus identifying the exposed ports or services and dealing with them in time.
If you are already having an in-house incident response or detection system, then OpenVAS will help you improvise your network monitoring using Network Pentesting Tools and alerts as a whole.
| Pros | Cons |
| Open Source Tool, free to use | Skilled Security analysts are only able to Extract the full potential of the platform |
| CVEs added in regular intervals | |
| Having a Large Community of Users |
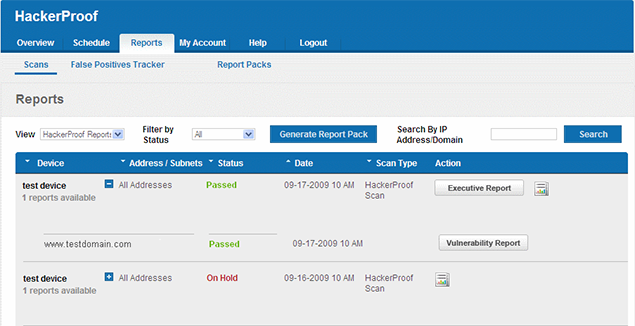
Comodo HackerProof is another leading best vulnerability scanner with robust features that would allow IT departments to scan their vulnerabilities on a daily basis.
PCI scanning options, Prevention for drive-by attacks, and site inspector technology that helps in next-generation website scanning.
Apart from these perks, Comodo also provides an indicator for the users to feel secure while they interact with you.
This will reduce shopping cart abandonment, improve conversions, and generate revenue in a large ratio. Not to forget their unique site inspector technology that acts as the best counter for drive-by attacks.
| Pros | Cons |
| Web-based scanner | Limited scan availabilities |
| PCI Approved vendor |
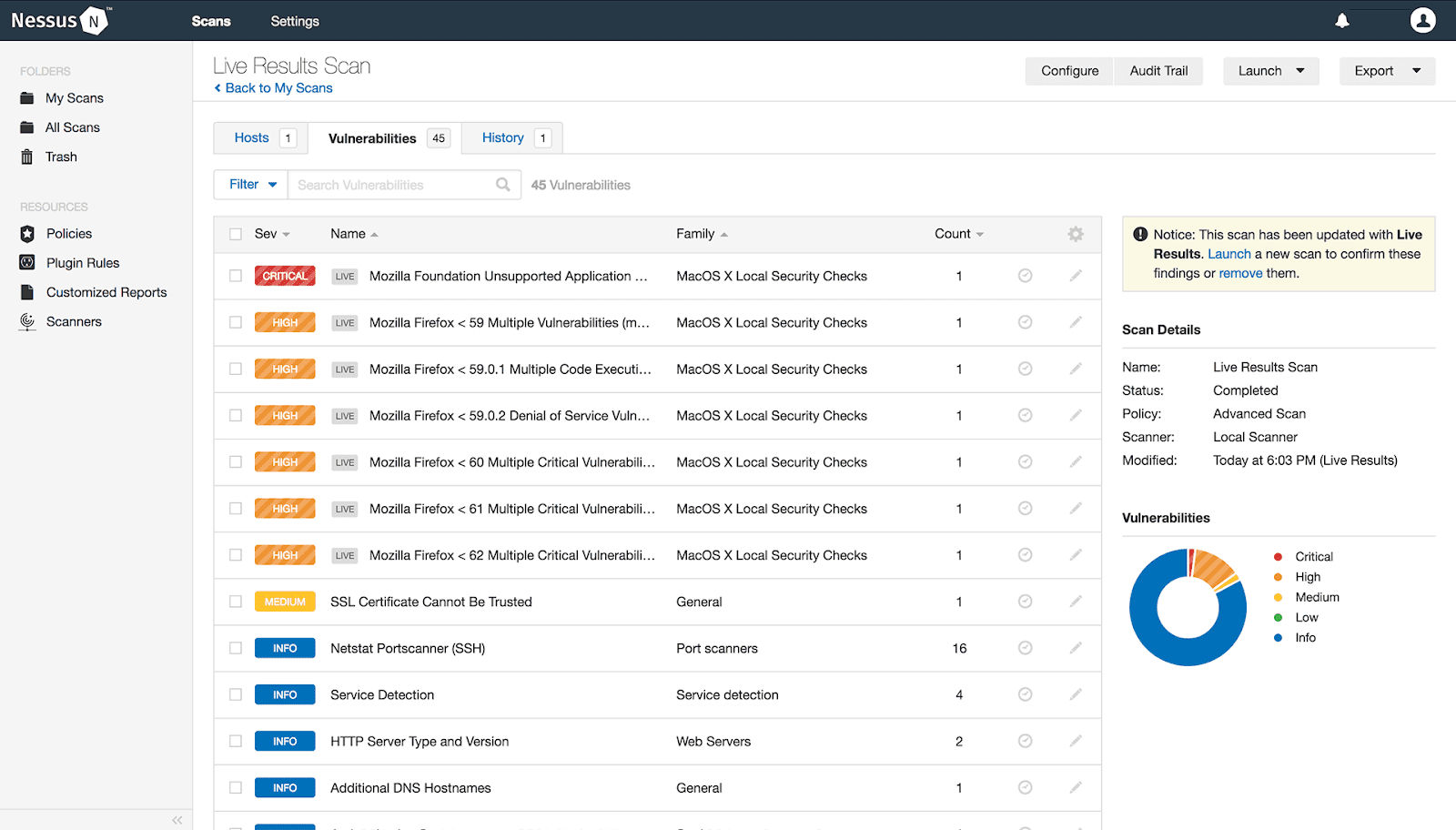
Nessus Professional from Tenable work for security professionals, taking care of patching, software issues, malware, adware removal tool, and misconfigurations over a wide range of operating systems and applications.
Nessus brings in a proactive security procedure by identifying the vulnerabilities in time before hackers use them for penetrating a network and also takes care of remote code execution flaws.
It cares about most of the network devices, including virtual, physical, and cloud infrastructure.
Scanning Options
Tenable has also been mentioned as the Gartner Peer Insights Choice for vulnerability assessment by March 2020.
| Pros | Cons |
| Best Penetration scanner | No Graphical Reports |
| Customization of scanners, with lots of plugins | Pricing is a Point of Concern |
| Credential Scanning for Deeper Analysis |
Vulnerability Manager Plus is a new solution to this market, developed by ManageEngine. With its recent launch into the market and the feature it covers, this could be the expected Ethical Hacking Tool for organizations.

It provides attacker-based analytics allowing network admins to check the existing vulnerabilities from a hacker’s perspective.
| Cons | Pros |
| Efficient Vulnerability Management | Pricing Plans are Expensive |
| Feature-rich freemium edition |
Apart from that, automatic scans, impact assessment, software risk assessment, security misconfigurations, patching, zero-day vulnerability mitigations scanner,

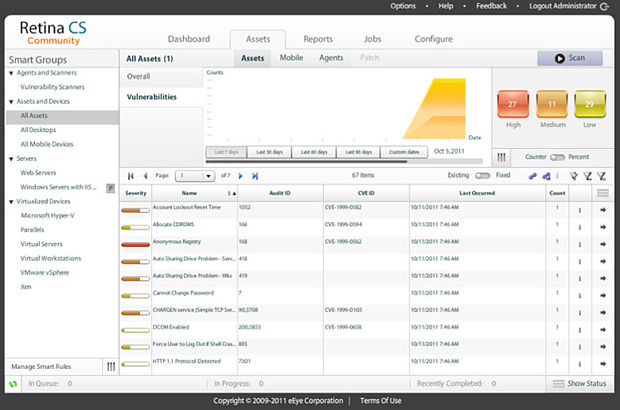
Nexpose community is a vulnerability scanning tool developed by Rapid7, it is an open-source solution that covers most of your network checks.
The versatility of this solution is an advantage for IT admins, it can be incorporated into a Metasploit framework, capable of detecting and scanning devices the moment any new device access the network.
Also monitors the vulnerability exposures to the real world, and above all, it identifies the threat’s capabilities to develop fixes accordingly.
Moreover, also vulnerability scanner tools pose a risk score for the threats, ranging anywhere between 1-1000, thus giving an idea for security pros to fix the right vulnerability before it is exploited. Nexpose currently offers a one-year free trial.
| Pros | Cons |
| Customizable Dashboards | Some users found difficult-to-understand reports |
| Easy to Deploy and scan | Crowded UI |
Nikto is another vulnerability scanner tools free to use online like the Nexpose community.
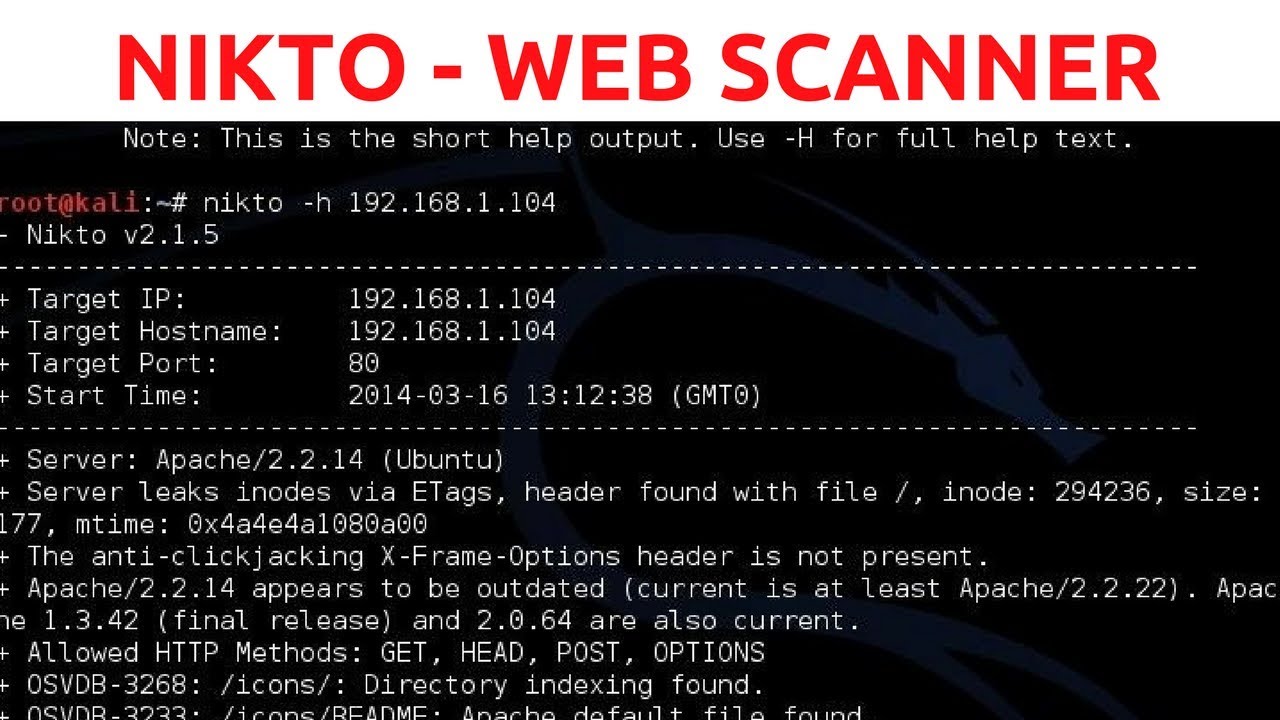
Nikto helps in understanding the server functions, checking up on their versions, performing a test on the web servers to identify threats and malware presence, and scanning different protocols like HTTPS, httpd, HTTP, and more.
Also helps in scanning multiple ports of a server in a short time. Nikto is preferred for its efficiency and server-hardening capabilities.
| Pros | Cons |
| Outdated Server Components Scanning | No GUI interface |
| Enumerates Sub-domain | Update years before |
If you aren’t looking for a robust solution to take care of the entire vulnerability management for your enterprise, then Nikto should be your pick.
Its features include patching, compliance, configuration, and reporting.
Takes care of databases, workstations, server analysis, and web applications, with complete support for VCenter integrations and app scanning virtual environments.
It takes care of multiple platforms offering a complete cross-platform vulnerability assessment tools list and security.
Please give a try on this vulnerability scanner and let us know which worked the best for you. If you have already tried them, share your thoughts about them in the comments section.
| Pros | Cons |
| Full network Discovery | Not suits Large Environment |
| Clear Interface | Consume huge resources |
Wireshark is considered to be one of the most powerful network protocol analyzers in the market. It runs successfully on Linux, macOS, and Windows devices.

It is used by many government agencies, businesses, healthcare, and other industries to analyze their network very keenly. Once Wireshark identifies the threat, it takes things offline to examine them.
Other highlights of Wireshark include a standard three-pane packet browser, network data that can be surfed using a GUI, powerful display filters, VoIP analysis, decryption support for protocols like Kerberos, WEP, SSL/TLS, and more.
You can learn Complete Training of Wireshark Tutorials to enhance your skills in network scanning.
| Pros | Cons |
| Great Filtering Capabilities | Noisy Interface |
| Good for Troubleshooting | Most times require Admin Privileges |
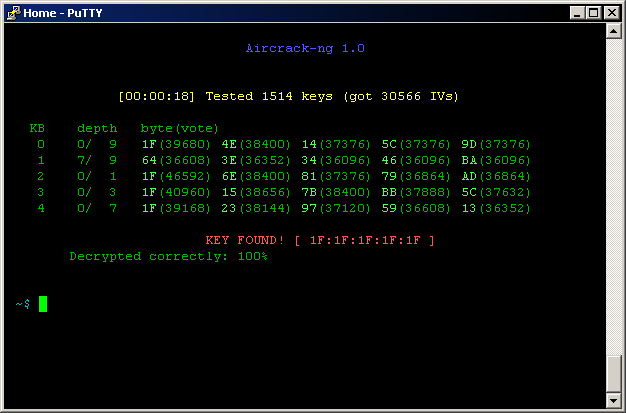
Aircrack-ng will help IT departments to take care of WiFi network security.
It is used in network audits and offers WiFi security and control, also works as one of the best wifi hacking apps whelps with drivers and cards, and replay attacks.
Takes care of the lost keys by capturing the data packets. Supporting OS includes NetBSD, Windows, OS X, Linux, and Solaris.
| Pros | Cons |
| Wireless network analyzer and attacker | Will not support WEP2 Protocols |
| Capture Packets and Extraction | Unable to do pentesting on non-wireless networks |
Conclusion
The Vulnerability scanner tools help in detecting and patching the vulnerabilities in a proactive way.
With automated scanning options, you can generate weekly vulnerability analysis reports and compare the results to gain more insight.
Above mentioned vulnerability scanning tools are tested by our expert and listed here based on their performance.