The MOVEit vulnerability victims hit by ransomware attacks can breathe a sigh of relief. Publishing their details have come to a halt after the US agencies put a 10 million reward against Cl0p ransomware group.
In a joint effort, the Cybersecurity & Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have issued an advisory, offering the million-dollar reward to anyone offering actionable intelligence on the Cl0p ransomware group.
The official US State Department program, Rewards for Justice, took to Twitter to announce a substantial $10 million reward against Cl0p for individuals possessing any valuable information pertaining to the activities of the ransomware group.

CISA and FBI offer $10 million reward against Cl0p
Following the MOVEit cyber attack, the Cl0p ransomware group had begun publicly naming victims of security breaches.

However, it was noted that after the FBI and allied US law enforcement agencies announced the $10 million reward against the Cl0p ransomware group, the hackers have temporarily halted their illicit activities.
“Do you have info linking Cl0p ransomware gang or any other malicious cyber actors targeting U.S. critical infrastructure to a foreign government?,” the tweet by Rewards for Justice read.
The $10 million reward against Cl0p would be given to anyone who offered a tip against the ransomware group or its activities.

The above image on the official Twitter account of RFJ_USA stated an amount of $10 million for any information about the Cl0p ransomware group.
The information could be sent to the US legal bodies via Signal, Telegram, WhatsApp, or its Tor-based tip line – he5dybnt7sr6cm32xt77pazmtm65flqy6irivtflruqfc5ep7eiodiad.onion
MOVEit cyber attack and Cl0p ransomware group
Soon after the Cl0p ransomware group gained access to MOVEIt Transfer and through it, the Zellis payroll service platform, the group allegedly started exfiltrating tons of system data.
First, the group exploited a vulnerability later named CVE-2023-34362. This was discovered on May 31 by Progress’s MOVEit.
Starting with the first week of June, Cl0p began claiming cyber attacks on the clients who used MOVEIt or Zellis. Some of the companies included British clients like BBC, British Airways, Irelands Aer Lingus, and the Canadian government website Nova Scotia.
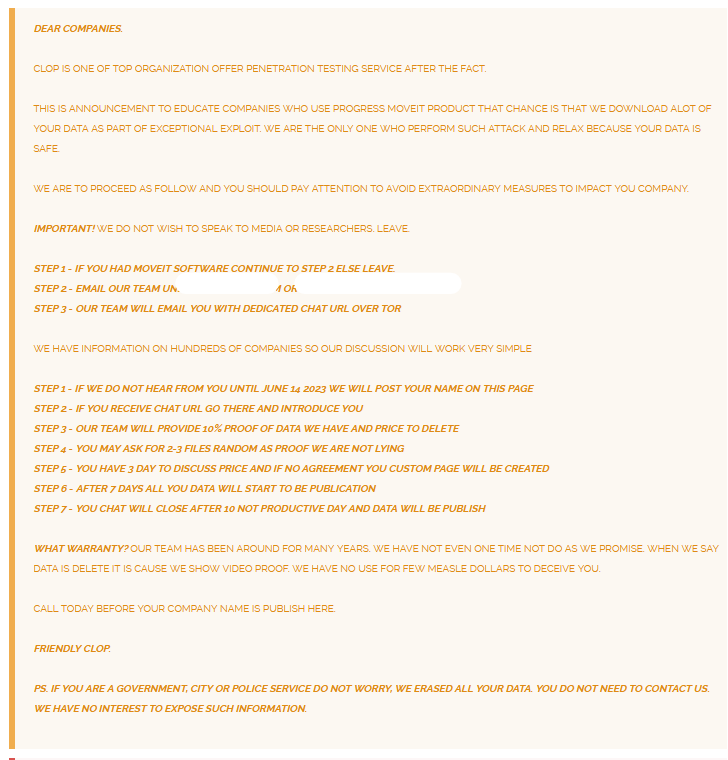
Initially, the ransomware group put a deadline of 12 June which they later changed to 14 June following which they threatened to leak the exfiltrated data.
The group also ‘assured’ government, city, and police officials that their data has been permanently erased and they need not worry about their data getting exposed.
In the following updates, the hackers from the Cl0p gang named the Johns Hopkins University, the University of Georgia, a fossil fuel business Shell, and an investment company Putnam Investments to their victim list.
Several other companies were added to the list of hacked companies from where the group claimed to have exfiltrated data. The group named several government websites with the U.S. Energy Department being sent two ransom notices, according to a Reuters report.
MOVEit vulnerability update: Leak site halts naming victims
The leak site of Cl0p stopped naming companies targeted via the MOVEit cyber attack, shortly after the FBI and CISA announced a $10 million reward against Cl0p for anyone who sent a tip on its activities.
The hackers have exploited companies across sectors including government, healthcare, and education, among others.

Among the last few victims of the ransomware attack were Minnesota Department of Education, Uk’s telco regulator Ofcom, and Tesco Bank.
According to a tweet by the Threat Analyst Brett Callow, by 16 June, 63 victims were named by Cl0p with reference to the MOVEit vulnerability exploitation.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.




