A sophisticated supply chain attack involving ten malicious npm packages that execute automatically upon installation and deploy a comprehensive credential theft operation.
The malware uses advanced obfuscation techniques, social engineering tactics, and cross-platform functionality to harvest sensitive authentication data from developers’ systems across Windows, Linux, and macOS environments.
Socket’s Threat Research Team has uncovered a malicious packages have remained active on the npm registry since July 4, 2025—over four months—accumulating more than 9,900 collective downloads before Socket petitioned npm for their removal.
The attack demonstrates a new level of sophistication in npm supply chain exploitation, combining automatic execution hooks, multi-layer obfuscation, and professional credential harvesting infrastructure.
The malicious packages leverage npm’s postinstall lifecycle hook to execute malicious code immediately when developers run npm install.
The threat actor configured the package.json file to trigger an install.js script automatically, which then detects the victim’s operating system and launches the malware in a hidden terminal window.
On Windows systems, the malware spawns a new command prompt; on Linux, it attempts to open gnome-terminal with fallback support for x-terminal-emulator; and on macOS, it uses AppleScript to launch Terminal.app.
By executing in separate terminal windows that immediately clear their content, the malware runs invisibly during the installation process, avoiding detection by developers who glance at their terminal output.
This execution method is particularly insidious because it requires no additional user interaction beyond the initial npm install command.
Developers installing a typosquatted package unknowingly trigger the malware without any obvious indication that malicious code has executed on their system.
Four Layers of Advanced Obfuscation
The malware implements four distinct obfuscation layers designed to defeat static analysis and reverse engineering attempts.
The outermost layer wraps the entire payload in a self-decoding eval wrapper that reconstructs and evaluates itself at runtime, preventing cursory inspection of the source code.
The second layer employs XOR encryption with a dynamically generated key based on hashing the decoder function itself, making automated decryption difficult without executing the code.
The payload string is then URL-encoded, adding another barrier to analysis tools that lack full JavaScript evaluation capabilities.
Finally, the decoded code uses switch-case state machines with hexadecimal and octal arithmetic to obscure program flow, making manual analysis extremely time-consuming.
This multi-layered approach represents a significant advancement in npm malware obfuscation, protecting the threat actor’s infrastructure and capabilities from security researchers attempting to understand the attack.
The credential theft operation unfolds across four distinct stages, each designed to evade detection while maximizing credential capture.
Stage one presents a fake CAPTCHA prompt to social engineer developers into believing they are interacting with legitimate bot protection.
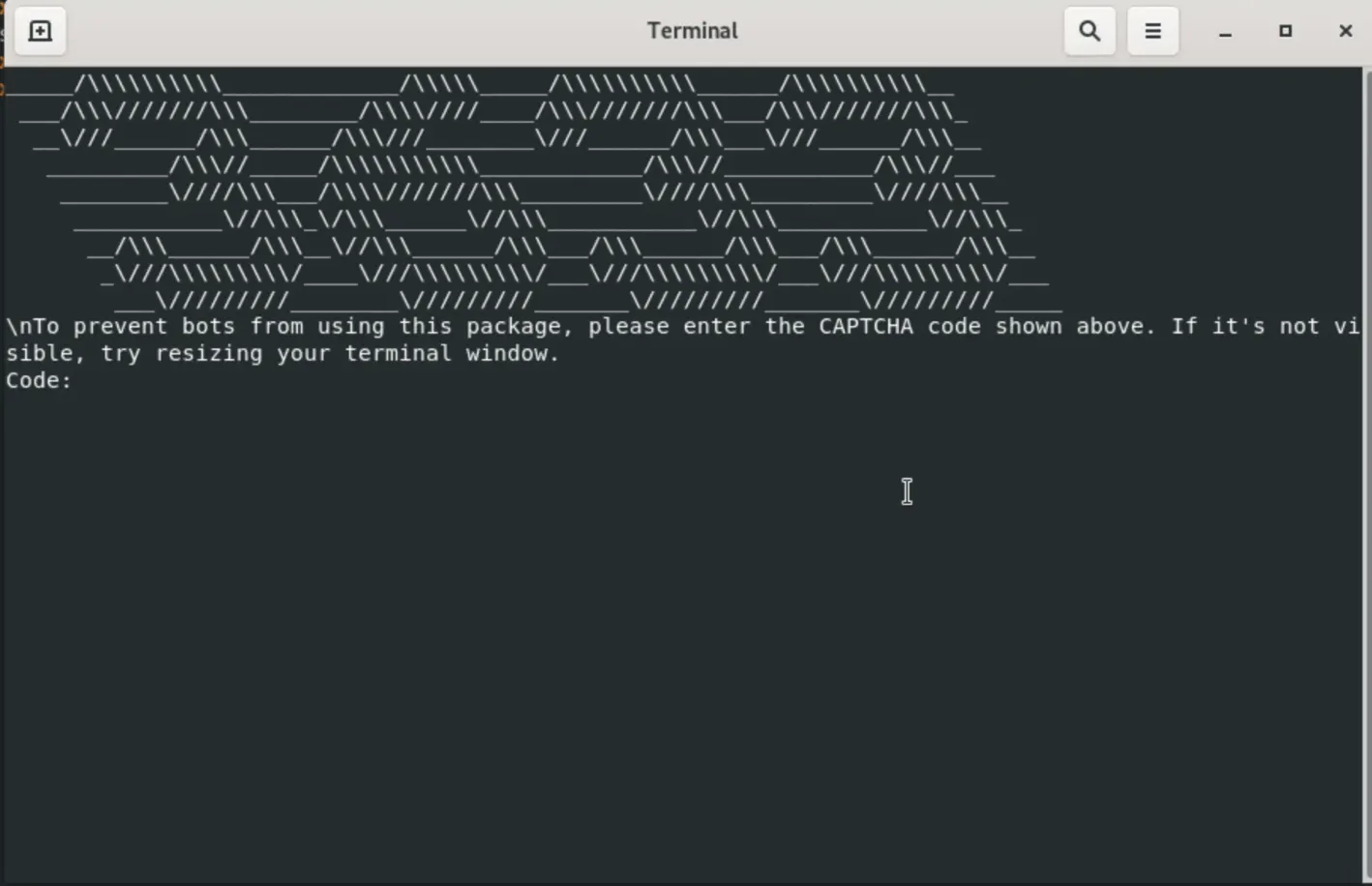
The malware simultaneously displays fake installation messages that mimic legitimate package dependencies, complete with realistic version numbers and contributor counts.
This deception makes the malware appear trustworthy and delays execution so the connection to npm install becomes less obvious.
In stage two, the malware sends the victim’s IP address to the threat actor’s server at 195.133.79.43/get_current_ip for fingerprinting and geolocation purposes.
This creates victim tracking records and allows the threat actor to verify that installations match their intended target profile.
![10 NPM Packages That Automatically Run on Install and Steal Credentials 3 Wireshark capture showing HTTP GET request to 195[.]133[.]79[.]43/get_current_ip.](https://cdn.sanity.io/images/cgdhsj6q/production/ae16a4bd4ba89f4212343c1fd379797b3927bd70-2000x1162.png?w=1600&q=95&fit=max&auto=format)
![10 NPM Packages That Automatically Run on Install and Steal Credentials 4 Wireshark capture showing HTTP GET request to 195[.]133[.]79[.]43/get_current_ip.](https://cdn.sanity.io/images/cgdhsj6q/production/ae16a4bd4ba89f4212343c1fd379797b3927bd70-2000x1162.png?w=1600&q=95&fit=max&auto=format)
Once the victim enters text into the fake CAPTCHA, stage three begins with the automatic download and execution of the data_extracter binary, a 24MB PyInstaller-packaged Python application tailored to the victim’s operating system.
Stage four involves comprehensive credential harvesting across multiple storage mechanisms.
The binary systematically scans file systems for credential stores, extracts data from system keyrings across all major operating systems, harvests browser session cookies and saved passwords, collects OAuth and JWT authentication tokens, and locates SSH private keys and configuration files containing API credentials.
The stolen data is compressed into ZIP archives and exfiltrated back to the attacker’s command-and-control infrastructure.
Cross-Platform Credential Harvesting
The data_extracter binary implements sophisticated credential extraction capabilities across Windows, Linux, and macOS platforms.
On Linux systems, it accesses credentials stored in SecretService D-Bus API, GNOME Keyring, and KWallet. macOS targets are exploited through Keychain Services API, while Windows systems have their Credential Manager harvested through CredRead and CredWrite APIs. This multi-platform approach ensures that developers on any operating system have their credentials compromised.
The malware specifically targets high-value credential stores including system keyrings used by email clients, cloud storage sync tools, VPN applications, and password managers.
Browser data extraction focuses on session cookies that bypass multi-factor authentication, saved passwords from browser password managers, and cookie jar data for session hijacking.
The binary includes specialized libraries for extracting modern authentication tokens, including OAuth tokens, JWT tokens, and LaunchPad credentials used for Ubuntu SSO and API access.
Organizations must immediately audit their dependencies for the ten malicious packages and assume any system where these packages were installed is fully compromised.
Teams should reset all credentials stored in system keyrings and password managers, revoke authentication tokens for all services, enable multi-factor authentication if not already deployed, and rotate SSH keys while reviewing authorized keys on all systems.
Access logs should be audited for unusual activity on connected services, and organizations must check for potential lateral movement from compromised systems to production infrastructure.
Security teams should review browser history for potential credential theft, establish monitoring for unauthorized access to repositories and cloud services, audit VPN and firewall logs for connections to the attacker’s infrastructure, and identify any additional persistence mechanisms that may have been installed.
Implementing Socket’s supply chain defense tools—including GitHub app integration for dependency scanning, CLI inspection during installation, browser extensions for download warnings, and enterprise firewall protection—substantially reduces the risk of similar supply chain attacks compromising development environments.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
