A new wave of spamware targeting WhatsApp Web users has emerged, as the Socket Threat Research Team revealed the discovery of 131 malicious Chrome extensions actively flooding the Chrome Web Store.
These extensions are not conventional malware, but function as high-risk automation tools, systematically violating platform policies to facilitate large-scale spam campaigns, primarily targeting Brazilian users.
Reseller Model Creates Clone Flood
At the core of this operation lies a single WhatsApp Web automation tool, cloned and rebranded into 131 distinct extensions. Despite sporting unique names, logos, and marketing sites, all clones share the same codebase, design patterns, and backend infrastructure.
Branding variations mask the underlying reality: over 80 of these extensions sport the label “WL Extensão” or a near-identical variant, but all have been published by just two developer accounts linked to the Brazilian company DBX Tecnologia and its affiliate, Grupo OPT.
Key characteristics of the operation include:
- 131 rebranded clones of a single WhatsApp Web automation tool.
- All extensions share identical codebase and infrastructure.
- Published through only two developer accounts: [email protected] and [email protected].
- Extensions branded under WL Extensão and WLExtensao labels across 83 listings.
- Campaign has been running for at least nine months with regular updates through 2025.
This structure mimics a franchise business model. For a licensing fee, resellers receive a customizable build—logo, name, and interface tweaks included but the backend and core code remain unchanged and managed centrally.
DBX Tecnologia advertises the venture as a lucrative “white-label partnership,” promising recurring revenue streams and healthy margins for resellers.
The result is a multi-pronged operation, with resellers publishing near-identical tools and flooding the market through marketing sites, YouTube, LinkedIn, and other channels.
Bypassing Policies and Targeting Users
The purpose of these extensions is clear: automate bulk messaging via WhatsApp Web, including scheduling and template features that evade WhatsApp’s anti-spam algorithms.
The software injects code directly into the WhatsApp Web page, orchestrating unsolicited outreach in bulk, all while operating alongside legitimate WhatsApp scripts.
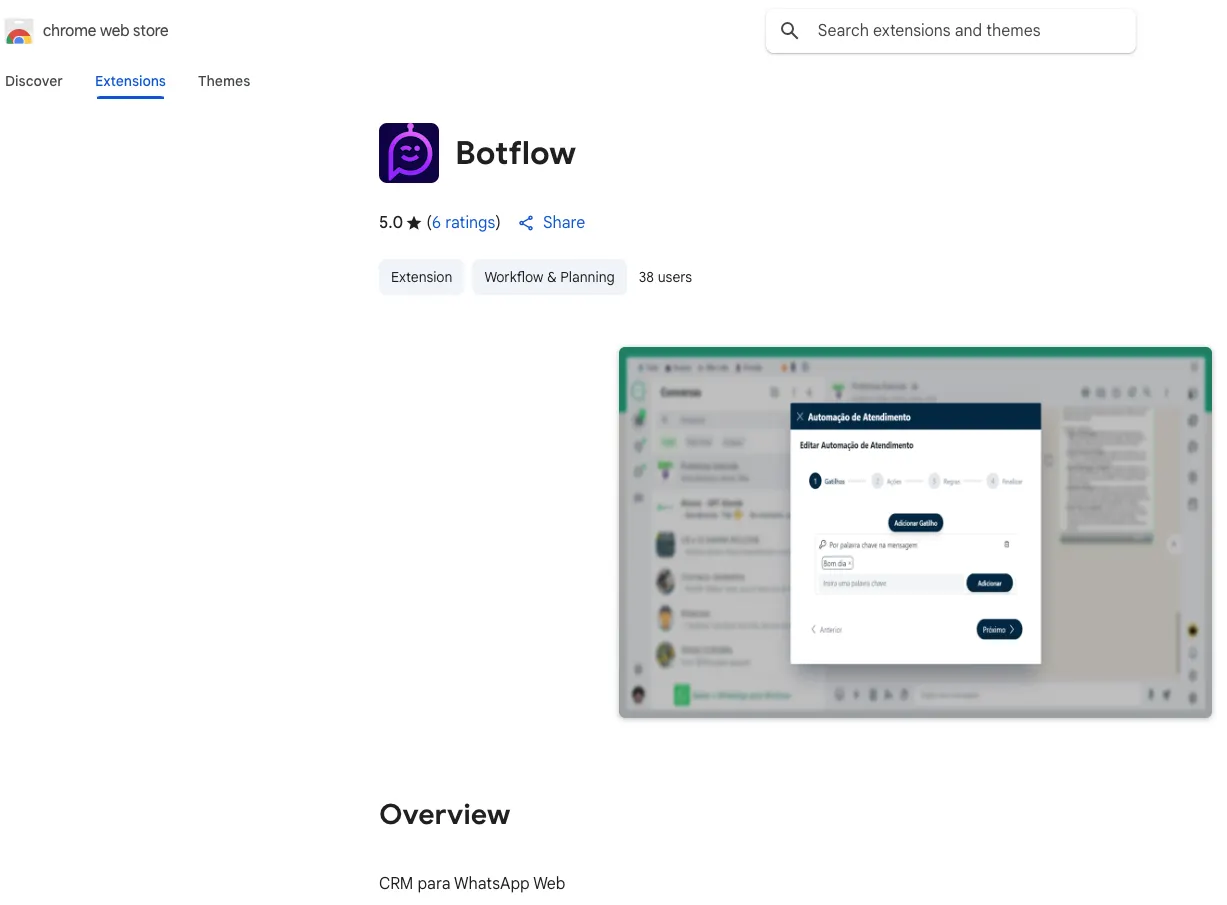
Promotion materials and tutorials highlight ways to tweak message intervals and delivery patterns specifically to bypass detection systems.
Policy violations and technical mechanisms:
- Code injection directly into WhatsApp Web pages alongside legitimate scripts.
- Automated bulk messaging and scheduling systems designed to bypass anti-spam controls.
- Violation of Chrome Web Store policies prohibiting duplicate extensions and spam.
- Circumvention of WhatsApp’s Business Messaging policy requiring explicit opt-in.
- Marketing materials falsely claim Chrome Web Store presence guarantees security audits.
Claims that Chrome Web Store presence guarantees rigorous code audits or privacy compliance are misleading.
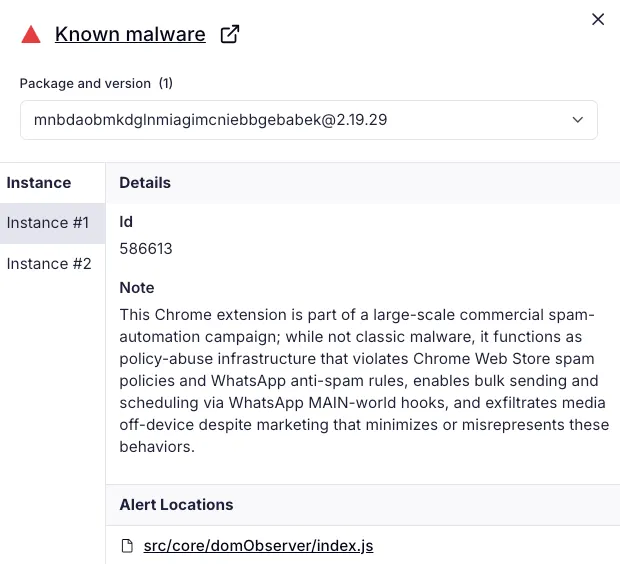

Actual abuse of the Chrome Web Store’s policies is central to the operation: Google explicitly forbids duplicate extensions, mass spam, and sending messages without user consent.
Meanwhile, WhatsApp’s Business Messaging policy demands explicit opt-in and rapid honoring of block requests — requirements systematically skirted by this campaign.
Wide Impact, Ongoing Threat
Together, these 131 extensions account for at least 20,905 active users. Socket’s AI security analysis flagged examples like “Organize-C” for direct policy violations. At time of publication, all extensions remain live, though takedown requests have been submitted.
For users and organizations, this campaign underscores the urgent need for security controls: limit Chrome extension installations to trusted sources, use inventory and permission analysis tools, and closely monitor for suspicious behaviors.
With bulk messaging spam on the rise, robust countermeasures are a must for anyone relying on WhatsApp for business or personal communication.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
