In a concerning turn of events, 23andMe, the renowned genomics company, is grappling with yet another potential data breach, leaving millions of user profiles at risk. This marks the second 23andMe cyberattack in less than a month.
Reports suggest that a hacker operating under the pseudonym “Golem” has allegedly leaked over 4 million genetic profiles. Primarily targeting users in Great Britain, Golem’s scope also extends to the wealthiest individuals in the U.S. and Western Europe.
23andMe Cyberattack: The Identities of Threat Actors Still Unknown
Katie Watson, Vice President of Communications at 23andMe, confirmed the company’s awareness of the situation. She stated, “We are currently reviewing the data to determine if it is legitimate,” adding that their investigation is ongoing, reported MobileSyrup.
This recent security lapse is not the first for the 23andMe cyberattack. Previously, the personal information of more than 1.3 million Ashkenazi Jewish and Chinese users was compromised.
The company initially dismissed claims, attributing the leaked data to previously compromised credentials rather than a direct breach of their systems.
The 23andMe cyberattack includes users’ names, genders, birth years, ancestral heritage results, maternal and paternal genetic markers, profile and account numbers, and information related to health data opt-ins.
The Initial 23andMe Cyberattack
The first Initial 23andMe cyberattack, disclosed on October 6, resulted from a credential stuffing attack, specifically targeting users of Ashkenazi Jewish heritage.
This raised significant concerns within the affected community. According to 23andMe, the incident involved the unauthorized compilation of certain customer profile information, shared through the DNA Relatives feature.
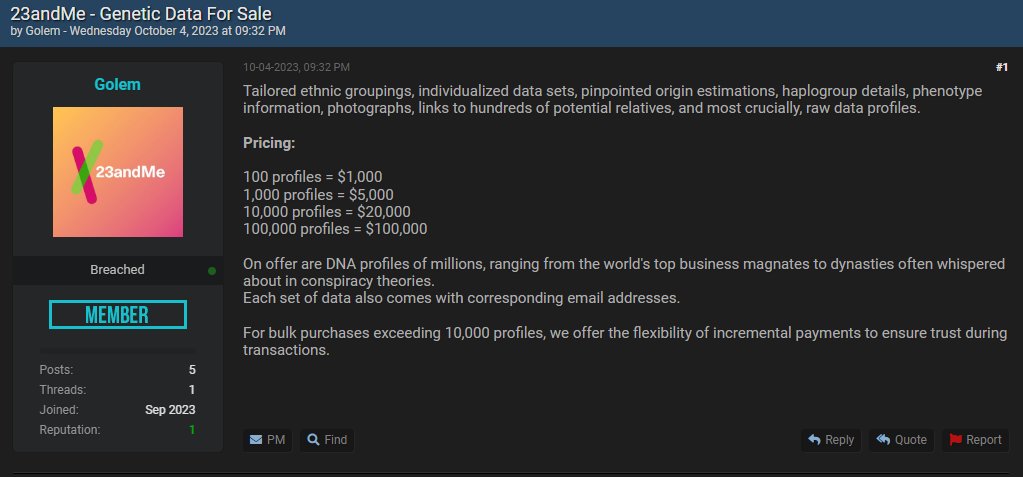
The Cyber Express previously reported about threat actors using “data packs” for the release of data. These data packs contained highly sensitive information about the company, including documents related to individual datasets, haplogroup details, phenotype information, photographs, and more.
In light of these breaches, 23andMe has issued recommendations to enhance user security. These include using strong, unique passwords, resetting current credentials, and implementing multi-factor authentication.
As the company continues to investigate and rectify these breaches, users are urged to take proactive steps to safeguard their information.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
