No less than 330000 FortiGate firewalls are still unpatched and vulnerable to CVE-2023-27997, a critical security flaw affecting Fortinet devices that have come under active exploitation in the wild.
Cybersecurity firm Bishop Fox, in a report published last week, said that out of nearly 490,000 Fortinet SSL-VPN interfaces exposed on the internet, about 69 percent remain unpatched.
CVE-2023-27997 (CVSS score: 9.8), also called XORtigate, is a critical vulnerability impacting Fortinet FortiOS and FortiProxy SSL-VPN appliances that could allow a remote attacker to execute arbitrary code or commands via specifically crafted requests.
Patches were released by Fortinet last month in versions 6.0.17, 6.2.15, 6.4.13, 7.0.12, and 7.2.5, although the company acknowledged that the flaw may have been “exploited in a limited number of cases” in attacks targeting government, manufacturing, and critical infrastructure sectors.
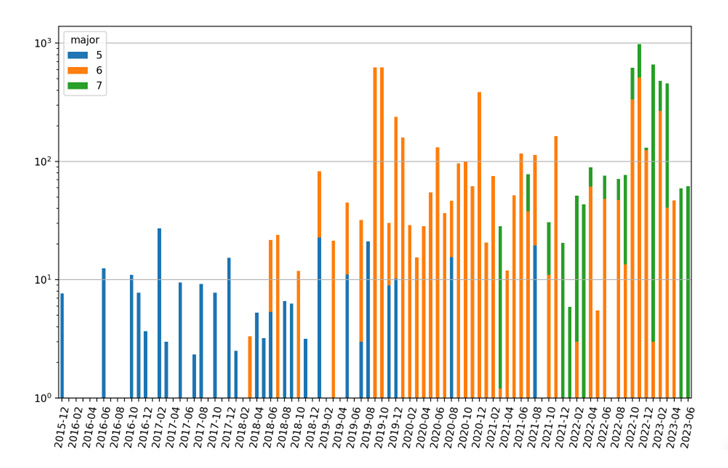
Bishop Fox’s analysis further found that 153,414 of the discovered appliances had been updated to a patched FortiOS version.
Another crucial discovery is that many of the publicly accessible Fortinet devices did not receive an update for the past eight years, with the installations running FortiOS versions 5 and 6.
Given that security flaws in Fortinet devices have been lucrative attack vectors, it’s imperative that users move quickly to update to the latest version as soon as possible.
