A new report from cybersecurity researchers at ESET has uncovered a massive botnet comprised of over 400,000 compromised Linux servers being used for cryptocurrency theft and other illicit financial gain.
The botnet, operated by the threat group behind the Ebury malware, has been active since at least 2009 but has evolved significantly over the past decade.
Ebury’s Insidious Spread
The Ebury gang employs a variety of techniques to propagate the malware and expand their botnet:
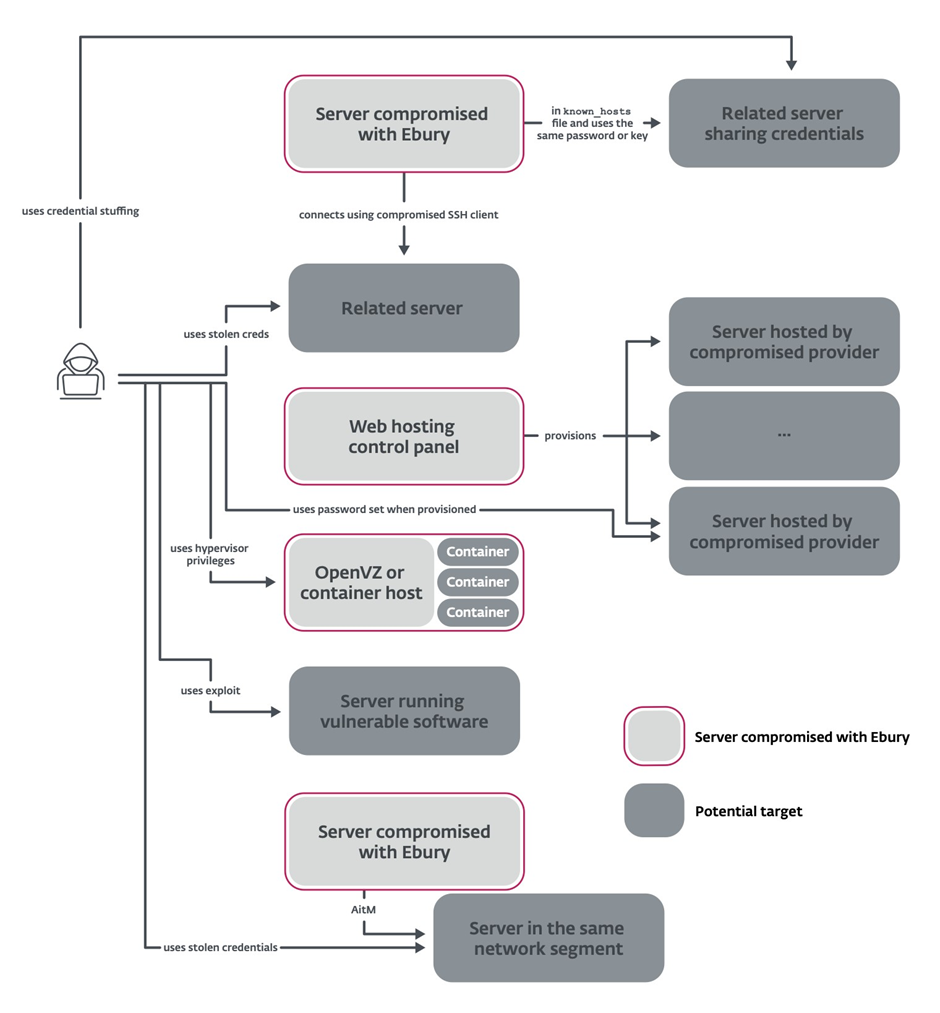
- Compromised Hosting Providers: Leveraging access to hosting companies’ infrastructure to install Ebury on all hosted servers
- ARP Spoofing Attacks: Intercepting and redirecting SSH traffic inside data centers to capture credentials
- Over 200 Bitcoin/Ethereum Nodes Targeted: Automatically stealing crypto wallets when victims log in
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
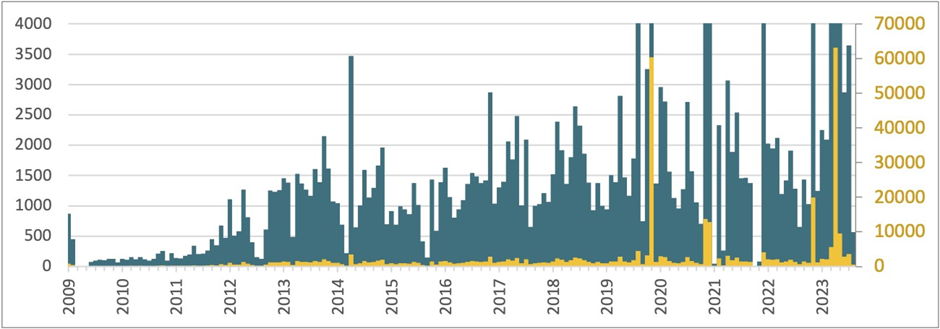
As illustrated below, the botnet has seen explosive growth, with over 100,000 servers still infected as of late 2023.
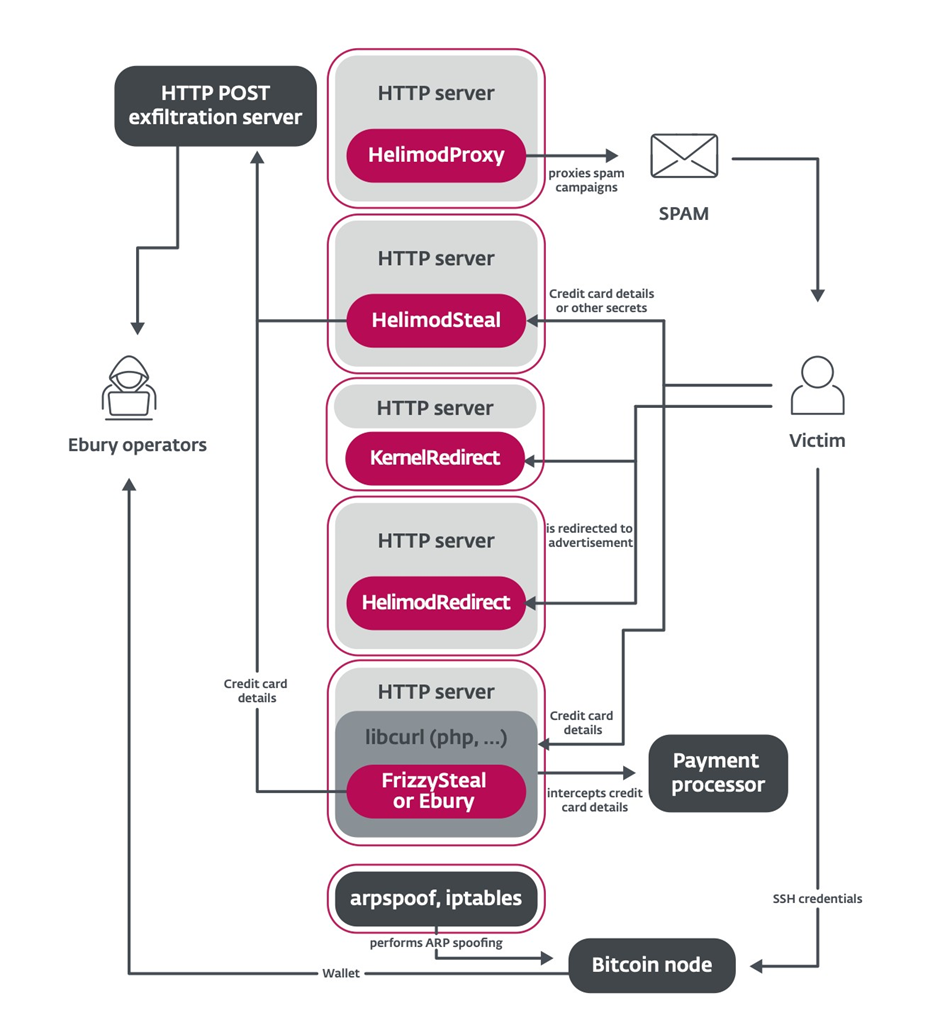
Evolving Malware Arsenal
In addition to traditional spam and traffic redirection, ESET’s report reveals new malware families used to monetize the botnet through:
- Stealing financial data from transactional websites
- Cryptojacking to mine cryptocurrency on infected systems
The Ebury family of malware has also been made better.
The latest big version update, 1.8, came out in late 2023.
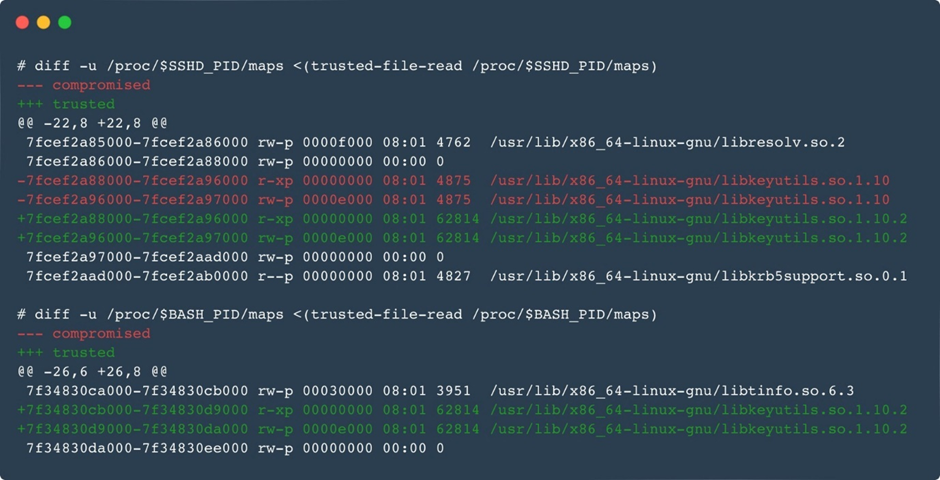
Many changes have been made, including new ways to hide information, a new domain generation algorithm (DGA), and better userland rootkits that Ebury uses to hide from system admins.
When the mode is on, the process, file, port, and even the mapped memory are hidden.
ESET has released indicators of compromise and a detection script to help organizations identify if they have been impacted.
The full report provides in-depth technical analysis for security teams.
As this potent botnet continues expanding, maintaining patched systems and robust credential policies is critical to preventing compromise. The cybersecurity community must also remain vigilant against the evolving Ebury threat.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free
