One of the top IT research and advisory companies, 451 Research, recently authored a new “pathfinder report” advising decision-makers on the value of bug bounties and the importance of a compliant vulnerability disclosure process.
Download the Report
The report details how companies can optimize a hacker-powered security program, from “everyone’s first step” of creating a public vulnerability disclosure policy (VDP) to how to run a bug bounty program. The report is well worth the 20-page read. It is a good resource to bring execs up to speed on how VDPs and bounty programs operate.
For those execs who don’t have the bandwidth to get past a TL;DR synopsis, we’re cutting to the chase and focusing here on 451 Research’s seven-step “roadmap”. (Feel free to paste this into an email to your exec and take credit for finding it.)
Seven Steps to Hacker-Powered Security Success
Hacker-powered security is no longer just for cutting-edge tech firms, although the amazing results they’ve seen have pushed this concept into the fabric of IT security teams across the spectrum. In 2016, Facebook saw a 38% increase over 2014 in the discovery of high-impact bugs thanks to their program, while Google’s Bughunter University noted a 50% increase in reward payouts in 2016 over 2015.
Now, organizations from the U.S. Department of Defense to Starbucks, General Motors to Snapchat, and Intel to Lufthansa are using hacker-powered security methods to better protect their products, data, and customers.
So how does an organization get started down this path of hacker-powered security? Here’s how!
1. Create a vulnerability disclosure policy (VDP) and make it easy to find.
It’s shocking — yes, shocking — to realize that 94 percent of the Forbes Global 2000 do not have known vulnerability disclosure policies (based on HackerOne’s own research). Read another way, if you’re reading this, you probably don’t have a VDP. That’s bad.
Even before you begin to consider and debate the value of bug bounties, 451 Research says “a VDP should be considered table stakes for any company with a public footprint.” Simple logic says you should make it easy for people to let you know when they encounter an issue, and a VDP can be as simple as an email address or contact form — solutions that are essentially free to implement.
Beyond that, it’s as easy as defining what types of issues and which systems are covered, what level of response to expect, and general “rules of engagement.” Some industry groups have even published templates to make policy creation even easier.
2. Ensure that staff managing corporate communications understand how to recognize and handle a disclosure.
Getting your corporate communications machine involved early is crucial to a successful VDP. As 451 Research puts it, “there aren’t many security-related incidents that can’t be improved by effective and transparent communication.” And, they go on to explain how a past breach at social media orchestration service Buffer turned the event into “a marketing win, attracting new customers and drawing an outpouring of support and understanding from existing customers.”
“Transparency and responsiveness can go a long way in winning over customers and the general public,” according to 451 Research. Of course, the opposite is also true. A hacker found 40 zero-day vulnerabilities in Samsung’s Tizen operating system and, over several months, only received automated email responses to his reports. “Only after being contacted by a journalist for comment did Samsung spring to action and get in touch with the researcher.”
Here’s another tip: don’t wait for an embarrassing (or worse) security event to engage with your communications team or create good communications protocols. Do it now so you won’t have to figure it out when you really need it.
3. Document and practice vulnerability handling.
So once a vulnerability is reported, what do you do? How you triage the report, communicate with the public and affected parties, and resolve the issue should all be defined and practiced regularly. There are even ISO standards (27147 and 30111) to help you define your disclosure
process and vulnerability handling process.
Basically, it’s just defining how the process works and writing it down. According to 451 Research’s finding, “having a clear, common set of rules and expectations that is easy to locate is critical.”
4. Select your Bug Bounty Platform partner.
Using an external bug bounty platform provider will help “reduce the burden of triage and response to reported bugs and give companies the necessary tools to automate many of the steps in vulnerability disclosure and handling,” according to 451 Research. As with any solution, they recommend organizations consider several key elements when choosing a provider:
Disclosure assistance and community support.
Access to the pool of available talent.
Features native to the management platform.
Integration with existing workflows.
Capabilities for automation and orchestration.
In the report, 451 Research goes deeply into the nuances of each point, including an additional overview of important metrics to evaluate bug bounty success. According to their findings, important bug bounty metrics include mean time to first vulnerability discovered, mean response time, total reports submitted, percentage of duplicate reports and total payout.
5 & 6. Start with a conservative private bounty program. Then launch a public bounty.
Yeah, those are two steps jammed into one, but once you get your feet wet with a private program, the evolution to a public program is much easier.
With a private program, you’re inviting a small number of hackers and giving them exclusive (and guided) access to your systems. You get more control, get to iron out the kinks in your internal processes, and as 451 Research suggests, you “have the luxury of finding and fixing the most serious flaws before production release, and with no one the wiser.”
A public bounty, on the other hand, adds not only more and more diverse hackers, it provides positive marketing and communications benefits. “(A public program) conveys a certain confidence and determination to improve quality and security that will likely attract customers.”
7. Refine and expand your hacker-powered program as needed.
An “ancient developer proverb” was quoted by 451 Research: Before bug bounty, chop wood, carry water. After bug bounty, chop wood, carry water.
A bug bounty program isn’t a one-and-done program. It’s a process that’s “most valuable when used as a permanent, perpetual addition to the software development lifecycle.” An ongoing bug bounty program returns more value as hackers get to know your team, products, code, processes, preferences, and other nuances.
But the overall goal — of your entire security machine, of which bug bounties are simply a component — should revolve around reducing the number of bugs that ever make it to a bug bounty program. “An improvement in this metric likely indicates an improvement in the quality of software overall. Fewer bugs to fix means less risk and a reduced cost of doing business.” See Figure 3 from the report below:
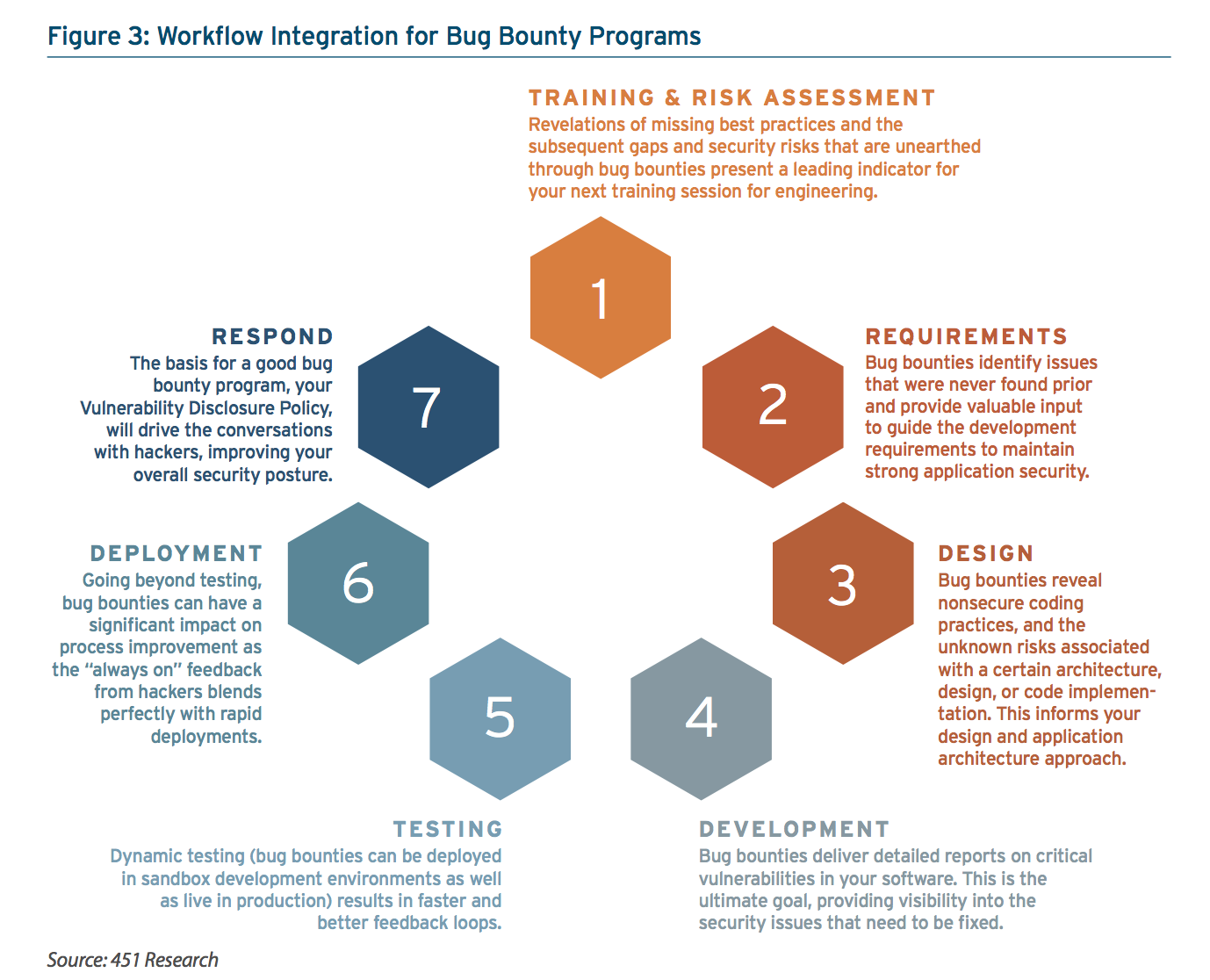
As you think of expanding your bug bounty program beyond just websites and webapps, consider AT&T’s program as inspiration. Their bounty program “covers nearly everything publicly accessible that AT&T owns or sells: DVRs, smartphones, websites, mobile apps – all are valid targets for the bug bounty.”
Other sectors, such as new and relatively unsecured Internet of Things devices, are seeing more, and more public (see: Mirai), security issues. Also, consumer products (see: CloudPets) “with their lower price points and margins, tend to skip even the most basic due diligence before hitting shelves.”
Conclusion
The 451 Report, “Bug Bounties and the Path to Secure Software,” was commissioned by HackerOne to bring a third-party’s perspective into how hackers can help discover and mitigate vulnerabilities before malicious individuals exploit them.
Consider the 451 Report your primer and “buyer’s guide” if you will to get started with hacker-powered security. HackerOne is the number one vulnerability coordination and bug bounty platform and we have helped hundreds of organizations with every phase of their crowd-sourced security journey: from implementing a VDP, diving in with a time-bound Challenge, or launching your public or private bug bounty program. HackerOne is the obvious choice to integrate hacker-powered security into your current security apparatus. Just shoot us a note to chat – we’re friendly people and we’re here to help!
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.
