Even with Slack, Teams, and every new communication tool out there, email remains the top attack vector for businesses. Why? Because it’s familiar, trusted, and easy to exploit.
One convincing message is all it takes and threats slip right past filters, AVs, and EDRs without making a sound.
Below are five real examples of attacks that went undetected by traditional tools but were fully exposed in ANY.RUN’s interactive sandbox.
Check them out to see how they work and how you can stop threats like these with far less effort.
1. Malware Attachments: The Threat That Looks Routine
For many SOCs, malware attachments remain one of the most frustrating blind spots. On the surface, these files look like everyday business documents, PDFs, invoices, shipping notes.
They often pass through because static analysis doesn’t catch what the file actually does.
Why SOCs miss it:
- Static scanners only check signatures, not behavior
- Trusted services (like SharePoint) hosting the payload increase false negatives
- No real user interaction means the full payload chain doesn’t execute in test environments
But with an interactive sandbox like ANY.RUN, SOC teams get exactly what’s been missing: complete visibility into the full execution chain, from the moment a file is opened to the final exfiltration attempt.
Unlike static scanners, the sandbox actively interacts with the file, clicks buttons, opens links, and triggers hidden payloads, exposing behaviors that would otherwise stay dormant.
Even files that appear clean on the surface reveal their true nature when watched in real time.
Real Case: A Dangerous PDF That Looks Legit
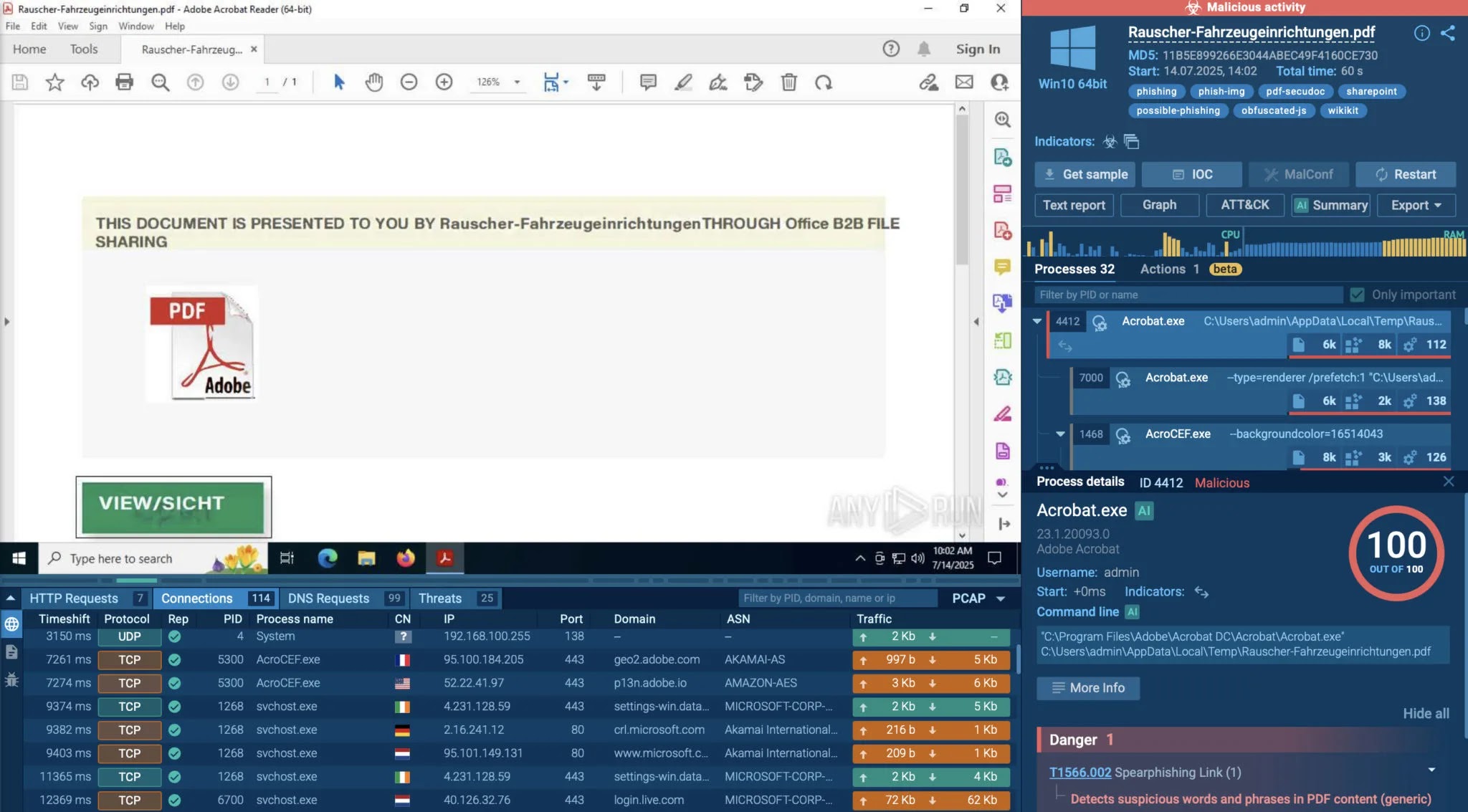
At first glance, Rauscher-Fahrzeugeinrichtungen.pdf looked like a routine business file. But when detonated in ANY.RUN’s sandbox, a much different picture emerged.
The moment the file was opened, it reached out to a phishing page hosted on SharePoint; a trusted Microsoft domain often used to bypass filters.
Inside, obfuscated JavaScript silently triggered further system activity, including the launch of Adobe Acrobat and Microsoft Edge.

Edge loaded a fake Microsoft login page, built to steal credentials. Meanwhile, background processes connected to external servers to exfiltrate data.

ANY.RUN flagged this as a social engineering attack, mapping it to MITRE T1566 (Phishing) and exposing the full execution chain, from open to credential theft attempt.
Without a sandbox, this file would’ve looked clean. With ANY.RUN, SOC teams get the visibility they need to detect, understand, and stop threats before they do damage.
Equip your SOC with ANY.RUN’s sandbox to detect evasive email threats in real time and cut response time with less manual effort -> Sign up now 2. Credential Theft: When One Click Opens The Door
Credential theft remains one of the most dangerous email threats for SOCs, especially when it’s paired with tools designed to bypass MFA.
These phishing campaigns often rely on well-crafted links that look legitimate and trigger behavior that’s nearly invisible to traditional defenses.
Most SOC tools scan for known indicators, but they rarely catch what happens after a link is clicked. That’s where interactive sandboxes make all the difference.
Real Case: Phishing with Tycoon 2FA

In this attack, a phishing email contained a link tied to Tycoon 2FA; a tool used to bypass MFA on Microsoft and Google accounts.
Once clicked, ANY.RUN’s sandbox observed multiple Edge processes launching; an early red flag. These processes began altering browser cache and user data and even started editing registry keys.

The victim was then redirected to a perfect replica of a Microsoft login page, hosted on a malicious domain. Any credentials entered here would go straight to the attacker.
The sandbox also flagged a potential Tor connection, likely used to exfiltrate the stolen data.
.webp)
Without a sandbox, this kind of phishing activity looks like a normal browsing session.
But with ANY.RUN, your SOC can see the full attack flow, identify suspicious patterns, detect MFA bypass attempts, and block them before credentials are lost.
3. Zero-Day Exploits: The Attacks That Don’t Wait
Zero-days are a nightmare for SOCs because they exploit flaws that don’t have a patch or signature yet. Traditional tools can’t catch what they don’t recognize and that’s exactly what makes these threats so dangerous.
One recent case involved CVE-2024-43451, a Windows vulnerability that leaks NTLMv2 hashes just by interacting with a malicious shortcut file.
No clicks needed, simply previewing the email was enough to launch the attack.
Real Case: Phishing with Zero-Day Exploit
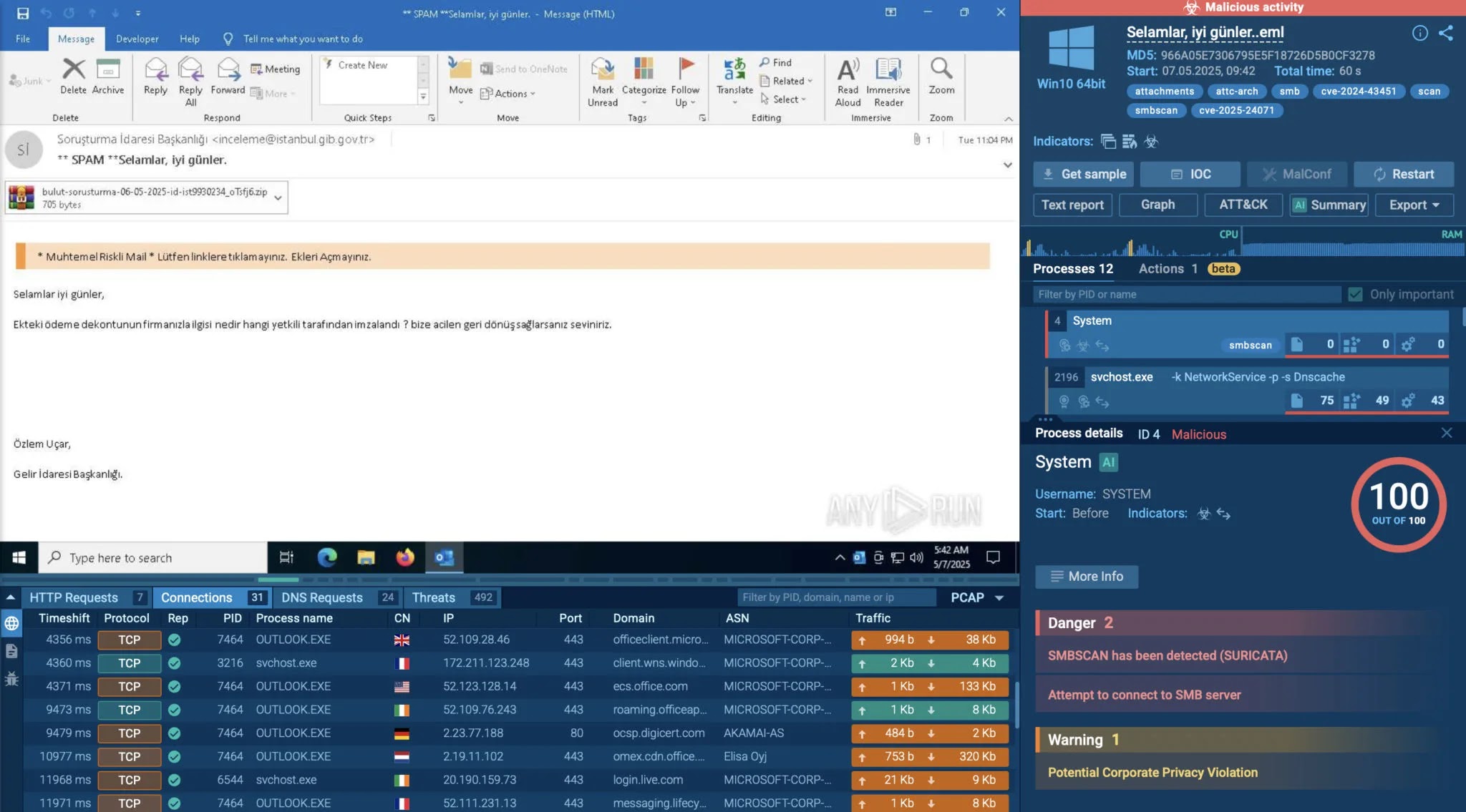
Inside the ANY.RUN sandbox, a malicious .eml file was opened. Without any user action, it triggered Edge, then WinRAR, and finally launched hidden commands that abused the vulnerability.

Finally, a silent SMB connection that exfiltrated the user’s NTLMv2 hash gave attackers a path to pass-the-hash lateral movement.

For SOCs, this is exactly why behavioral visibility matters. With ANY.RUN, it’s detected and mapped in under a minute, before attackers get in.
4. Quishing: The QR Code Trick Most Tools Miss
Quishing, phishing via QR codes, is a growing challenge for SOCs. These attacks embed malicious QR codes in emails or attachments, luring users to scan them with their phones.
Since mobile devices often sit outside corporate defenses, the attack bypasses filters, EDRs, and email gateways completely.
Real Case: Voicemail Phish via QR

In this ANY.RUN session, a phishing email claimed the user had a voicemail. The catch? They had to scan a QR code to hear it.
Inside the sandbox, ANY.RUN’s automated interactivity kicked in, scanning the code, decoding the URL, and exposing the phishing site in seconds, without any manual steps needed from the analyst.

For SOC teams, this means faster detection, less analyst time, and the ability to catch threats that bypass traditional email protections entirely.
5. CVE-2017-11882: Old Exploit, Ongoing Threat
Despite being years old, CVE-2017-11882 is still actively exploited, mainly through malicious .RTF or .DOC files delivered via phishing emails.
The vulnerability lives in the outdated Microsoft Equation Editor and enables remote code execution as soon as the document is opened.
For SOCs, these types of legacy exploits often go undetected because the payload looks like a standard Office file until it’s actively run.
Real Case: Exploit Triggered via Email Attachment

In this ANY.RUN session, the attack arrived via a .eml file containing an Office document.
When opened, it triggered the EQNEDT32.EXE process and began executing a chain of malicious actions; reading system configs, accessing certificates, dropping files, and reaching out to external servers.

ANY.RUN flagged the exploit instantly and mapped it to MITRE ATT&CK, giving the SOC team immediate clarity and saving time on manual investigation.

By detecting known exploits like this in real time, sandboxes help teams reduce MTTD and stop even outdated attack methods before they spread.
Make Your SOC Ready For Real-World Email Threats
The five email attacks are real cases captured in the wild, often bypassing traditional defenses and landing directly in employee inboxes.
For most SOCs, static scans, email filters, and EDRs aren’t enough to expose what’s really happening after the click. That’s why you need a solution like ANY.RUN’s interactive sandbox.
With ANY.RUN sandbox, your SOC gains:
- Deep behavioral visibility into attachments, links, and payloads
- Detection of evasive threats that bypass traditional tools
- Automation that reduces analyst workload and response time
- Enriched IOCs for faster investigation and SIEM integration
- Detailed, shareable reports to support response and compliance
Start your 14-day trial of ANY.RUN and bring real-world detection power into your SOC.
