In the latest PLAY cyber attack, six organizations have been victimized. The affected entities span across different regions, including the United States, the United Kingdom, and Norway.
The targeted organizations include Roof Management, Security Instrument Corp, Filtration Control Ltd, Cinépolis Cinemas, CHARMANT Group, and Stavanger Municipality.
The claims were shared via PLAY ransomware group’s data leak channel, where it claimed to have targeted these organizations.
The real intent or motivations behind these PLAY cyber attacks have not been a shared threat actor — leaving more doubts about their campaign.
PLAY cyber attack: 6 new victims added to leak site
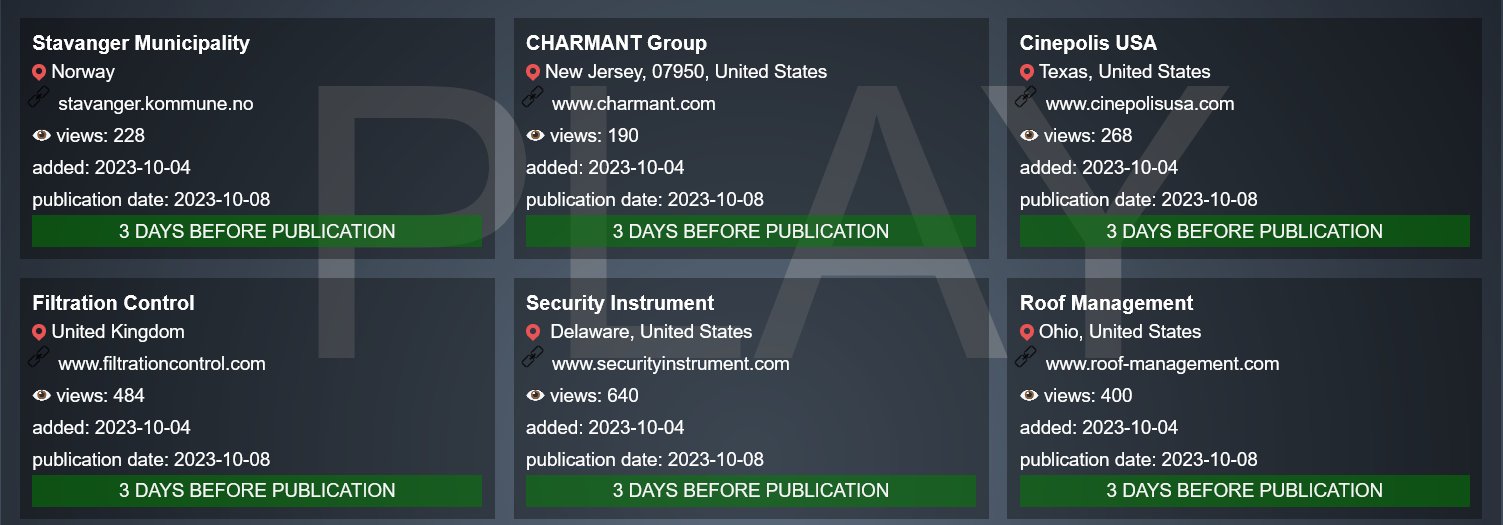
Upon learning about this PLAY cyber attack, The Cyber Express promptly contacted the affected organizations to gather further information on the PLAY ransomware group and their claims of the attack.
However, at the time of writing, no official statements or responses have been received, leaving the claims unverified.
The threat actor in question, the PLAY ransomware group, is a notorious threat actor that has been targeting small and medium-scale businesses for a long time.
The PLAY Ransomware group employs a variety of techniques to infiltrate an organization’s network, including the exploitation of known vulnerabilities like CVE-2018-13379 and CVE-2020-12812.
They also leverage exposed RDP servers and valid accounts to gain initial access. Once inside, they utilize “lolbins,” a common tool among ransomware groups.
How does the PLAY ransomware group infiltrate the organizations?
To distribute executables within the internal network, they employ Group Policy Objects, scheduled tasks, PsExec, or Wmic.
Once they establish full access, they encrypt files, appending them with the “.play” extension. Additionally, the group practices double extortion, threatening to expose sensitive data.
The PLAY ransomware group has recently expanded its arsenal, incorporating new tools and exploits such as ProxyNotShell, OWASSRF, and a Microsoft Exchange Server Remote Code Execution.
Among these, Grixba, a custom network scanner and infostealer, along with the open-source VSS management tool AlphaVSS, are noteworthy additions.
It has been reported that there is a potential link between PLAY ransomware and other ransomware families, specifically Hive and Nokoyawa. Shared tactics and tools indicate a high likelihood of affiliation among these groups.
Furthermore, parallels have been drawn between PLAY and Quantum ransomware, an offshoot of the Conti ransomware group. Both groups share some infrastructure, with Cobalt Strike beacons bearing the watermark “206546002” being a key indicator.
Despite the absence of current spam campaigns using the Emotet trojan, select cases have been identified where Emotet was employed to deploy Cobalt Strike beacons, bearing the same distinctive watermark as those found in PLAY’s ransomware attacks.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
