The LockBit ransomware group has claimed to have stolen data belonging to nearly 60 companies after the alleged Cloud 51 ransomware attack.
While the exfiltrated data from the 60 companies targeted by LockBit has not been published, the hacker collective has threatened to post the data soon.
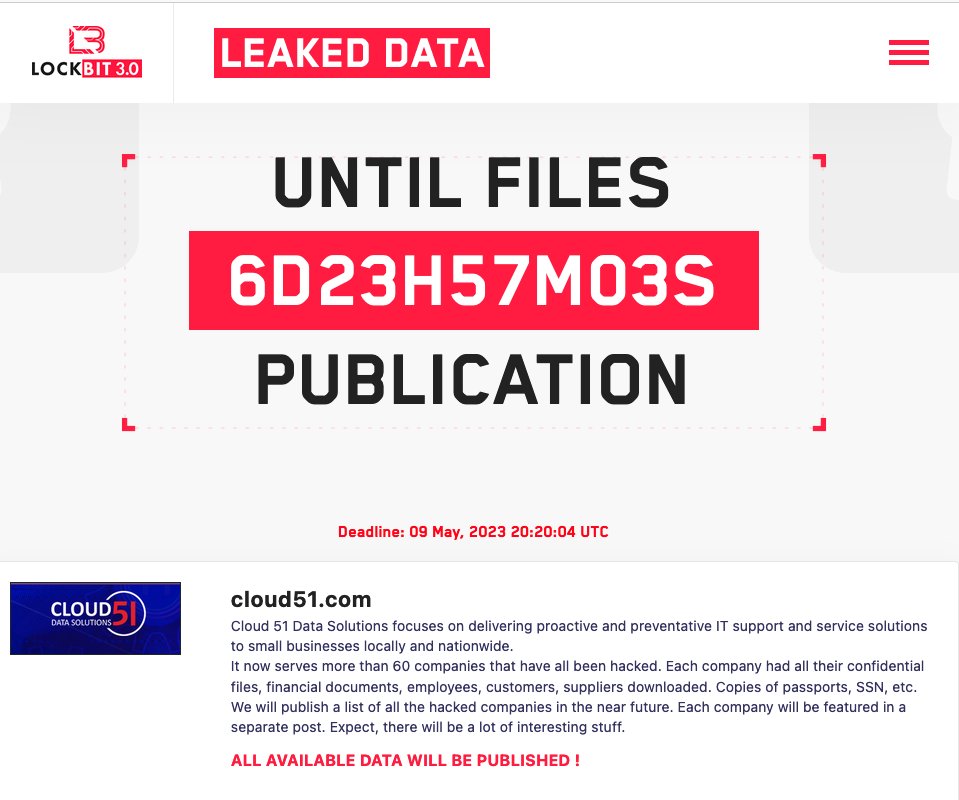
What the leak site message about the 60 companies targeted by LockBit read
The initial attack was made on a data solutions-providing firm, Cloud 51 that caters to companies including small and medium businesses.
Similar to the GoAnywhere MFT data breach, where Clop ransomware group accessed the databases of several clients and posted about each, LockBit has claimed to gain access to several of Cloud 51 clients.

The stolen files included financial documents, and employee and customer information. Access to supplier information, Social Security Numbers, and copies of passports was also retained from the 60 companies targeted by LockBit.
While the ransom demand remains undisclosed, the group has set May 9, 2023, at 20:20 UTC as the deadline to pay the amount.
The data breach post concluded with the lines, “Expect, there will be a lot of interesting stuff. All available data will be published.”
The Cyber Express reached out to Cloud 51 to confirm the ransomware attack. We are yet to get a reply from them. The website of Cloud 51 was accessible at the time of writing.
Modus Operandi of LockBit ransomware group
The LockBit ransomware formerly known as ABCD ransomware was identified in September 2019. The group mainly targets the United States of America, and European countries namely France, Germany, and the United Kingdom.
Asian nations including India, Indonesia, and China were also attacked by the group. The LockBit ransomware, which has had other versions of the malware in the past now follows a pattern of self-spreading.
Researchers find it a feature that is different from others that require manual effort in spying and spreading in the affected systems.
The ransomware is programmed to evade detection by hiding executable encrypting files in the. PNG image format. This is done to confuse the detection tools in the systems.
The three main stages of a LockBit attack follow a pattern of first gaining access by exploiting a vulnerability in the system.
Then, using the post-exploitation tool, the LockBit ransomware increases its privileges and disables security on the system.
Among the last few steps, it was observed that LockBit aims to create irreparable damage or slow any recovery mechanism followed by deploying the encryption payload.
After this stage, the ransomware can attack any network that it meets, and lock the files which can only be decrypted using a custom key owned by the group.
