In a recent cyber attack, the 8BASE ransomware group has once again struck, this time targeting COVESA, the prominent network of Ford dealerships with nine centers spanning the provinces of Barcelona and Girona in Spain.
The threat actors have claimed responsibility for a COVESA data breach within the company network, further expanding their list of victims.
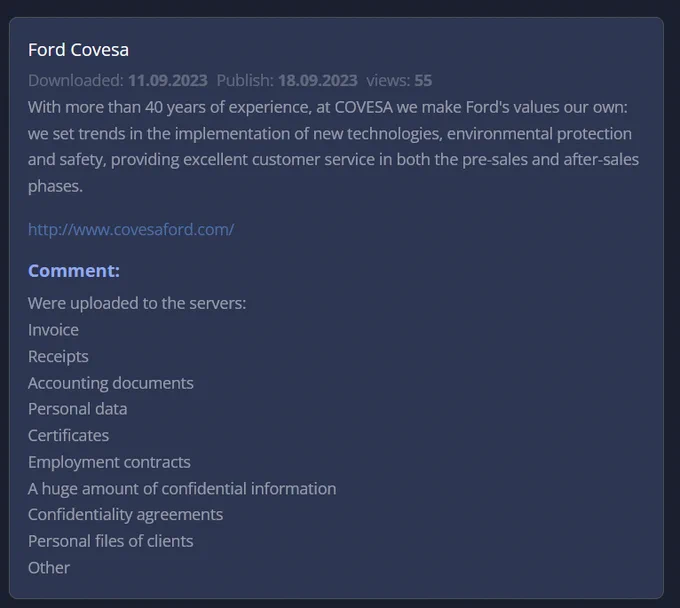
Moreover, the hacker collective asserted that they have gained access to sensitive information, including but not limited to invoices, receipts, accounting records, personal data, certificates, and employment contracts.
These claims have been announced by the ransomware group on their dark web channel and subsequently uploaded onto their servers, effectively putting pressure on COVESA.
However, the COVESA data breach and the potential ramifications for affected parties remain unverified.
COVESA data breach authenticity vs. claims
While The Cyber Express has attempted to obtain clarification from COVESA, it’s worth noting that the 8BASE ransomware group has a history of claiming cyberattacks on significant corporations. Therefore, their assertions regarding the COVESA data breach cannot be dismissed outright.
COVESA, on the other hand, carries over four decades of experience at the forefront of implementing cutting-edge technologies while prioritizing environmental protection and safety.
The company comprises a network of nine Ford Official Dealerships situated across the Barcelona and Girona provinces.
With its extensive history, operational approach, and the recognition it has garnered, COVESA is among the prominent automotive group not only in Catalonia but also in the broader country.
Previously, COVESA (formerly GENIVI Alliance) faced a DLT vulnerability within the GENIVI Alliance system. This vulnerability was identified in 2021 with a CVSS v3 score of 9.8.
It was deemed exploitable remotely with low attack complexity, potentially leading to remote code execution or application crashes.
COVESA recommended upgrading to the latest version of the affected product to mitigate potential vulnerabilities.
Additionally, CISA advises users to take defensive measures, such as minimizing network exposure and using secure remote access methods like Virtual Private Networks (VPNs).
8Base ransomware group’s latest cyber attack claims
Apart from this COVESA data breach, the 8Base ransomware group has gained notoriety for its indiscriminate targeting of various companies and organizations.
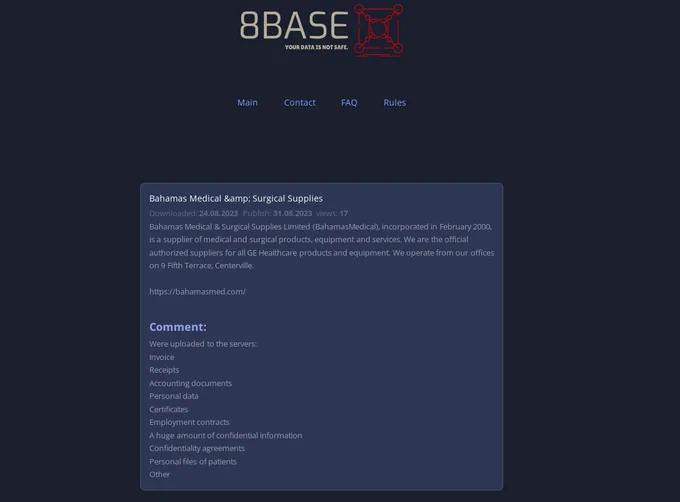
One prominent incident involved an attack on the Bahamas Medical & Surgical Supplies.
The Cyber Express recently covered the attack, revealing that the threat actors set a deadline of August 31, 2023, for potentially releasing compromised data.
Recent insights from VMware shed light on the group’s activities.
Operating since March 2022, 8Base has become one of the most prolific ransomware gangs, trailing only behind the LockBit 3 gang in terms of victims affected.
In June 2023, VMware’s analysis revealed that 8Base targeted nearly 80 victims within the past 30 days.
The sectors predominantly targeted by 8Base encompass business services, finance, manufacturing, and IT. One of the group’s signature tactics involves a “name-and-shame” approach, utilizing double-extortion methods.
This entails the threat of publishing encrypted files unless the demanded ransom is paid. The aim is to inflict reputational damage by exposing sensitive information that could tarnish the victim’s brand or standing.
Despite the surge in 8Base’s ransomware campaigns, crucial details about the group, including its identity, operational techniques, and motivations, remain largely elusive, according to VMware.
Nevertheless, an analysis of the group’s leak site, public communications, and stylistic choices suggests a resemblance to RansomHouse, a group known for procuring already compromised data or collaborating with data leak platforms for extortion.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
