Google’s Threat Intelligence Group (GTIG) says attackers exploited 75 zero-day vulnerabilities in the wild last year, over 50% of which were linked to spyware attacks.
These numbers are down from 97 zero-days in 2023 but up from 63 in 2022, which GTIG analysts attributed to year-to-year swings reflecting expected variation within an upward trajectory for attacks exploiting zero-days, which the company defines as vulnerabilities exploited in the wild before vendors release patches.
They noted that cyber-espionage threat actors—including government-backed groups and commercial surveillance vendors’ customers—were responsible for more than half of attributable zero-day attacks in 2024. Out of these, China-linked groups exploited five zero-days, commercial surveillance customers eight, while North Korean operators were linked to five zero-day exploits for the first time, used in attacks blending espionage and financial motives.
Last year, Google’s Threat Analysis Group (TAG) and Google subsidiary Mandiant saw 97 zero-days exploited in attacks, a surge of over 50 percent compared to the previous year’s 62 vulnerabilities, many also linked to spyware vendors and their clients.
While annual counts have fluctuated massively over the past four years, the average trend line shows a steady increase in zero-day exploitation. In 2024, end-user platforms and products (e.g., web browsers, mobile devices, and desktop operating systems) bore the brunt of this activity,
End-user platforms and products (e.g., web browsers, mobile devices, and desktop operating systems) made up 56 percent of the tracked zero-days. Exploits against browsers fell by roughly one-third, from 17 in 2023 to 11 in 2024, while mobile device zero-days dropped by nearly half, from 17 to nine.
Google Chrome remained the primary browser target, and desktop operating system exploits rose from 17 to 22, with Windows zero-days climbing to 22 last year, up from 16 in 2023 and 13 in 2022.
“As long as Windows remains a popular choice both in homes and professional settings, we expect that it will remain a popular target for both zero-day and n-day (i.e. a vulnerability exploited after its patch has been released) exploitation by threat actors,” GTIG said.
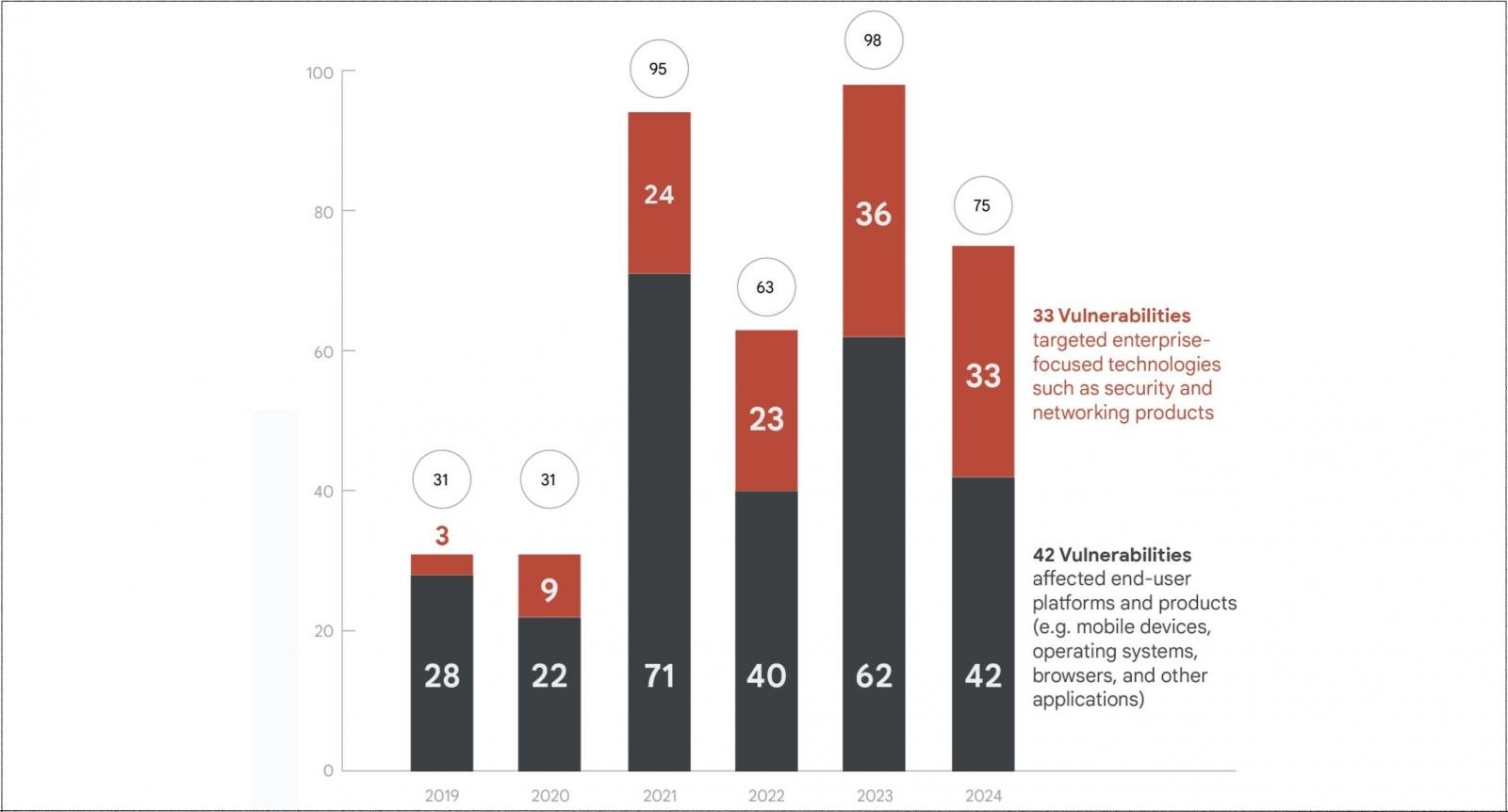
On the other hand, in 2024, attackers exploited 33 of the 75 zero-day flaws (44%) to target products used primarily in business environments, up from 37% in 2023.
Out of these, security and networking software and appliances accounted for 20 zero-days exploited in the wild, or more than 60% of enterprise-targeted zero-days. Attackers focus on them because breaching a single security appliance or network device can provide them with broad system access without requiring much more sophisticated multi-stage exploit chains.
As GTIG threat analysts found, notable enterprise zero-days exploited in 2024 included ones impacting Ivanti Cloud Services Appliance, Cisco Adaptive Security Appliance, Palo Alto Networks PAN-OS, and Ivanti Connect Secure VPN.
“Zero-day exploitation continues to grow at a slow but steady pace. However, we’ve also started seeing vendors’ work to mitigate zero-day exploitation start to pay off,” said Casey Charrier, Senior Analyst at Google Threat Intelligence Group.
“For instance, we have observed fewer instances of zero-day exploitation targeting products that have been historically popular, likely due to efforts and resources many large vendors have invested in order to prevent exploitation,”
“At the same time, we’re seeing zero-day exploitation shift towards the increased targeting of enterprise-focused products, which requires a wider and more diverse set of vendors to increase proactive security measures. The future of zero-day exploitation will ultimately be dictated by vendors’ decisions and ability to counter threat actors’ objectives and pursuits.”
