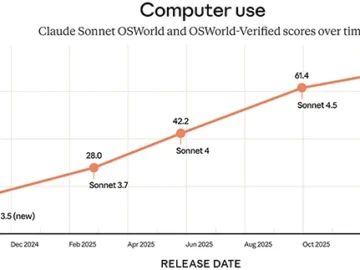
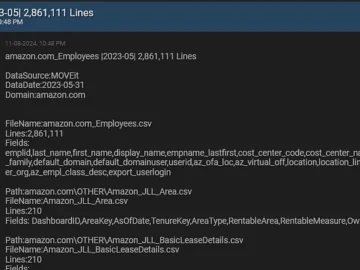
The explosion of Internet of Things (IoT) devices has brought about a wide range of security and privacy challenges, according to Bitdefender and NETGEAR.
The report is based on global telemetry of 3.8 million homes and 50 million IoT devices that generated 9.1 billion security events over the course of 12 months.
High vulnerabilities found in TVs, smart plugs, DVRs
With over 15 billion connected devices globally, from smart home appliances to industrial equipment, the attack surface has expanded dramatically. Vulnerabilities in IoT frameworks, like those found in the ThroughTek Kalay platform, expose millions of users to potential privacy breaches.
The average home now has 21 connected devices with home networks attacked over 10 times per day (up from 8 last year).
In 2023, the highest number of vulnerabilities were discovered in TV sets, smart plugs, and digital video recorders. Vulnerabilities in TVs are quite common, largely due to their extended lifespan and the tendency for manufacturers to discontinue support while the devices are still in use.
Smart Plugs and digital video recorders (DVRs) exhibit substantial vulnerability counts relative to their respective device populations. While smart plugs serve as convenient additions to smart home setups, their vulnerability count highlights potential security weaknesses in these seemingly innocuous devices.
Likewise, vulnerabilities in DVRs raise concerns about the security of video surveillance systems commonly employed in both residential and commercial settings. These findings emphasize the need for manufacturers to prioritize security in the design and production of such devices, as they play integral roles in modern connected environments.
Another Bitdefender study reveals that 78.3% of respondents use mobile devices for sensitive transactions. However, 44.5% do not use any mobile security solutions, leaving them susceptible to malware, phishing, and data breaches.
IoT security will be signed into law
To combat the risks associated with IoT (lack of) security, the US government has introduced the Cyber Trust Mark – a certification that helps consumers identify IoT devices that meet strict security standards, including strong credentials, regular updates, and data protection. This trust mark will help consumers choose IoT products that are built with security in mind, but the implementation is still a long way away. Until then, IoT security will remain an individual responsibility.
Certain industries or product categories adhere to better security standards and practices, resulting in lower vulnerability counts. For instance, devices categorized under “Home Automation” might have relatively fewer vulnerabilities compared to other categories due to standardized security protocols and certifications in the home automation industry.
The number of vulnerabilities also varies based on the practices of device manufacturers. Devices from manufacturers that prioritize security in their design, development, and patching processes may exhibit lower vulnerability counts compared to those from manufacturers that are less focused on security.
Across all device types, denial of service (DoS) attacks appear to be the most common type of vulnerability, with significant percentages observed for TV sets (36.7%), smart plugs (22.2%), DVRs (17.7%), routers (13.4%), and set-top boxes (6.9%). This shows that DoS vulnerabilities are widespread across various device categories and pose significant risks to their availability and functionality.
Memory corruption vulnerabilities, though less prevalent than overflow and denial of service, remain a notable concern, given their potential to exploit weaknesses in memory management systems and their contribution towards arbitrary code execution attacks. Mitigating memory corruption vulnerabilities requires thorough code review, input validation, and memory protection mechanisms to prevent exploitation.
99% of IoT exploitation attempts rely on previously known CVEs (emphasizing the importance of patching and running latest software). Only a fraction of attacks leverage weak passwords or plaintext authentication.