A newly discovered clipboard hijacking operation dubbed ‘MassJacker’ uses at least 778,531 cryptocurrency wallet addresses to steal digital assets from compromised computers.
According to CyberArk, who discovered the MassJacker campaign, roughly 423 wallets linked to the operation contained $95,300 at the time of the analysis, but historical data suggests more significant transactions.
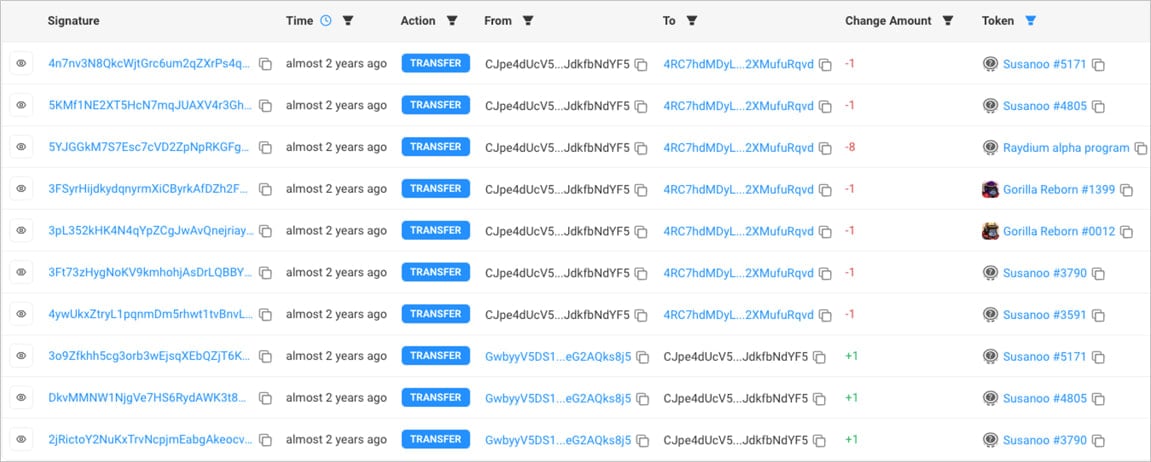
Also, there’s a single Solana wallet that the threat actors appear to use as a central money-receiving hub, which has amassed over $300,000 in transactions so far.
CyberArk suspects that the entire MassJacker operation is associated with a specific threat group, as file names downloaded from command and control servers and encryption keys used to decrypt the files were the same throughout the entire campaign.
However, the operation could still be following a malware-as-a-service model, where a central administrator sells access to various cybercriminals.
Source: CyberArk
CyberArk calls MassJacker a cryptojacking operation, though this term is more often associated with unauthorized cryptocurrency mining leveraging the victim’s processing/hardware resources.
In reality, MassJacker relies on clipboard hijacking malware (clippers), which is a type of malware that monitors Windows clipboard for copied cryptocurrency wallet addresses and replaces them with one under the attacker’s control.
By doing so, victims unknowingly send money to the attackers, though they meant to send it to someone else.
Clippers are simple but very effective tools that are particularly hard to detect due to their limited functionality and operational scope.
Technical details
MassJacker is distributed via pesktop[.]com, a site that hosts pirated software and malware.
Software installers downloaded from this site execute a cmd script that triggers a PowerShell script, which fetches an Amadey bot and two loader files (PackerE and PackerD1).
Amadey launches PackerE, which, in turn, decrypts and loads PackerD1 into memory.
PackerD1 features five embedded resources that enhance its evasion and anti-analysis performance, including Just-In-Time (JIT) hooking, metadata token mapping to obfuscate function calls, and a custom virtual machine for command interpretation instead of running regular .NET code.
PackerD1 decrypts and injects PackerD2, which eventually decompresses and extracts the final payload, MassJacker, and injects it into the legitimate Windows process ‘InstalUtil.exe.’
.jpg)
Source: CyberArk
MassJacker monitors the clipboard for cryptocurrency wallet addresses using regex patterns, and if a match is found, it replaces it with an attacker-controlled wallet address from an encrypted list.
CyberArk calls the cybersecurity research community to look closer into large cryptojacking operations like MassJacker, as despite the perceived low financial damages, they could reveal valuable identification information on many threat actors.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.



