In a recent surge of cyber threats, threat actors have been exploiting Reddit to distribute two potent malware variants: AMOS (Atomic Stealer) and Lumma Stealer.
These malware types are specifically designed to target cryptocurrency traders by offering cracked versions of popular trading software, such as TradingView.
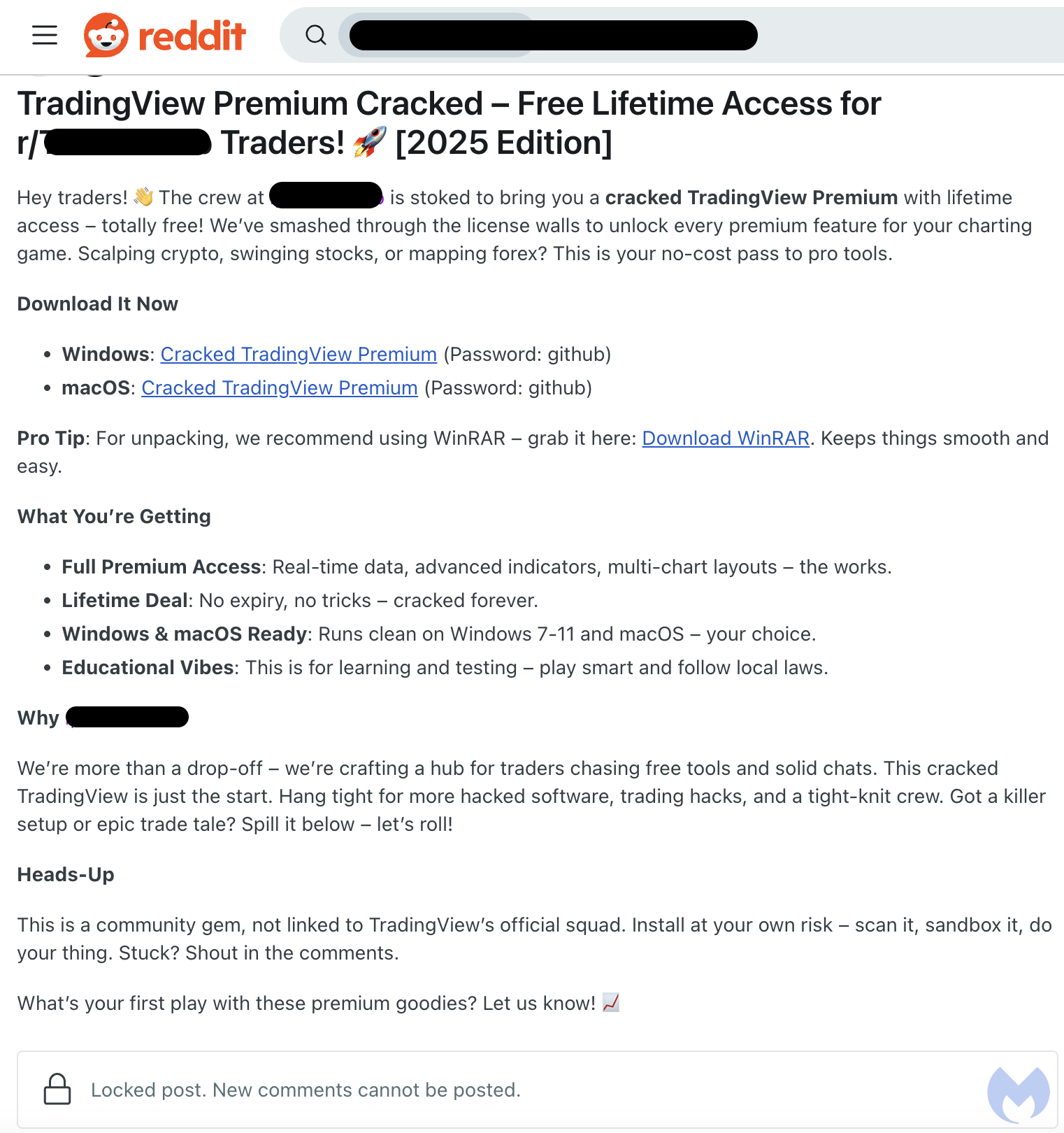
The attackers engage actively with potential victims on Reddit, reassuring them about the safety of the downloads and downplaying security concerns.
Distribution Tactics
The distribution of these malware variants involves sophisticated tactics.
On Reddit, attackers post links to compromised software installers, which are hosted on unusual servers, such as a website belonging to a Dubai-based cleaning company.
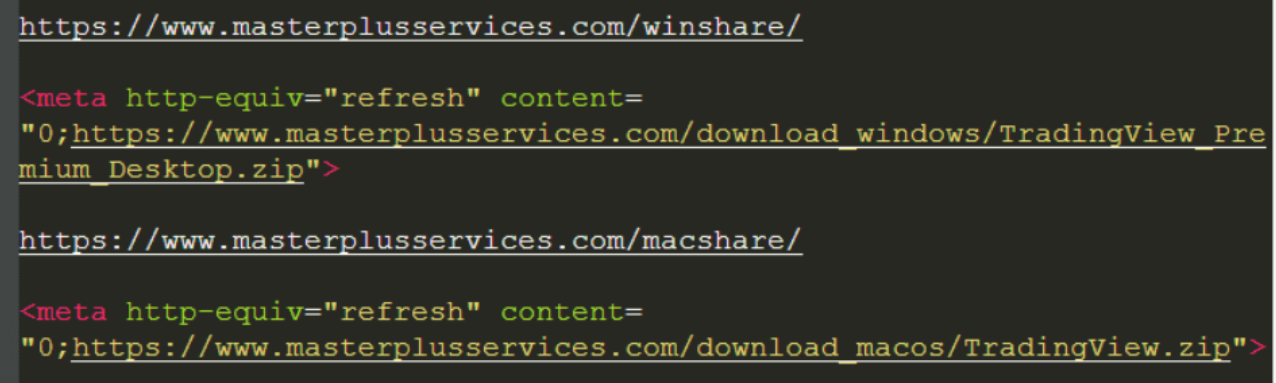

This choice suggests that the attackers have direct control over the server, allowing them to update and modify the malware payloads as needed.
The files are often double-zipped and password-protected, a common evasion tactic to bypass security scans.
According to MalwareBytes Report, for macOS users, the malware is a variant of AMOS, while Windows users are targeted with Lumma Stealer.
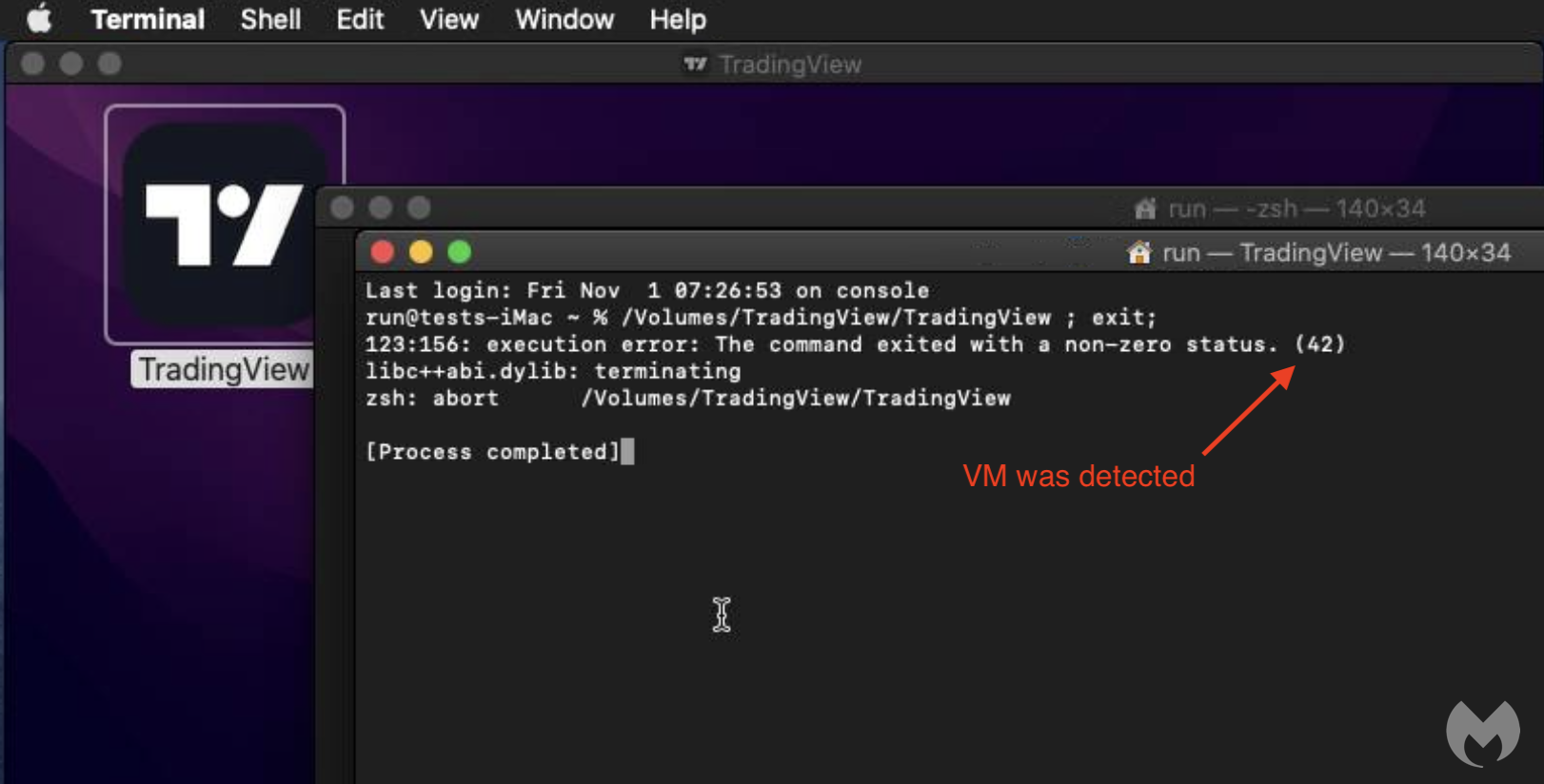

AMOS, or Atomic Stealer, is a macOS-specific malware that has been gaining traction since early 2023.
It is sold as a Malware-as-a-Service (MaaS) on Telegram and is known for its ability to extract sensitive information, including keychain passwords, browser data, and cryptocurrency wallet contents.
AMOS employs anti-debugging techniques and checks for virtual machines to avoid detection.
On the other hand, Lumma Stealer is a versatile malware available on both Telegram and dedicated websites, targeting a wide range of data, including web browser information, email credentials, and cryptocurrency wallets.
It uses advanced techniques like event-controlled write operations and encryption to evade detection.
Impact and Defense Strategies
The impact of these malware variants has been significant, with reports of stolen cryptocurrency wallets and subsequent impersonation attempts by attackers.
To mitigate these threats, users should be cautious of suspicious links and downloads, especially those promising cracked software.
Ensuring that software is downloaded from official sources and maintaining up-to-date security software are crucial defense strategies.
Additionally, cybersecurity professionals should focus on developing effective countermeasures against these evolving malware threats, including monitoring for unusual network activity and implementing robust data encryption practices.
As these malware variants continue to evolve, staying informed about their tactics and adapting defense strategies accordingly is essential to protect sensitive data.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup – Try for Free
