These days, hackers don’t break in — they log in. Using valid credentials, cybercriminals bypass security systems while appearing legitimate to monitoring tools.
And the problem is widespread; Google Cloud reports that weak or nonexistent credential protection facilitates 47% of cloud breaches, while IBM X-Force attributes nearly one-third of global cyberattacks to account compromises.
So what does this mean for your organization’s defenses?
Here’s what you need to know about how to protect your systems from credential-based attacks, what to do when prevention fails, and why scanning your Active Directory for compromised passwords should be a part of your security strategy.
Why credential-based attacks are hackers’ preferred method
Cybercriminals favor credential-based attacks for several reasons:
- They’re easy to execute: Credential-based attacks are relatively simple to deploy compared to more complex zero-day exploits.
- They’re highly successful: With users recycling the same password across multiple accounts, it’s easier for attackers to gain widespread access; one set of keys can unlock many doors.
- They have a low detection risk: Because they use valid credentials for their exploits, hackers can blend in with normal traffic, allowing them to avoid security alerts.
- They’re cheap: Credential-based attacks require minimal resources but can yield substantial rewards. Hackers can easily (and inexpensively) buy a set of stolen credentials on the dark web, then use free automated tools to test the credentials across multiple systems.
- They’re versatile: Credential-based attacks can be used anywhere credentials are needed, meaning hackers have multiple potential entry points — from web applications to cloud services.
Why organizations become targets
Could your organization be an attractive target for credential-based hackers? If you have any of these security gaps, your systems may be more vulnerable than you think. Here’s what makes organizations prime targets:
- Weak password policies create an open invitation for attackers to easily guess or crack credentials through automated tools and common password lists
- Failure to implement multi-factor authentication leaves even the strongest passwords vulnerable to theft
- Inadequate security training makes employees more vulnerable to phishing emails, social engineering tactics, and other attacks
- Poor network segmentation gives hackers open access once they breach a single endpoint
- Insufficient monitoring lets attackers operate undetected for days, weeks, or even months inside your critical systems
- Employee password reuse amplifies the impact of any breach, as a single stolen credential can unlock multiple systems across personal and corporate environments.
Verizon’s Data Breach Investigation Report found stolen credentials are involved in 44.7% of breaches.
Effortlessly secure Active Directory with compliant password policies, blocking 4+ billion compromised passwords, boosting security, and slashing support hassles!
Try it for free
When credentials are compromised: A response scenario
If your organization has been the target of a credential-based attack, you know how devastating the aftermath can be. But if you’re one of the lucky few that has so far escaped the sights of hackers, here’s what it’s like:
It’s 2:37 AM when your phone rings. Your security team has detected unusual login patterns from IP addresses in Eastern Europe — during your company’s off-hours. By the time you’ve logged in remotely, the attacker has accessed multiple sensitive customer files and moved laterally through your network, compromising additional systems.
The sinking feeling hits: your organization is experiencing a credential-based attack in real-time. What do you do now?
Immediate response steps
When credentials fall into the wrong hands and hackers breach your systems, every minute counts — but having a well-rehearsed incident response plan will allow you to minimize damage and recovery time.
Here are the typical steps organizations follow when responding to an attack:
- Initial detection and alerting. The clock starts ticking as soon as your monitoring tools detect the anomaly and alert your security team — you must move quickly to limit damage.
- Assessment and triage. Verify that the alert is legitimate. Then, identify which systems and accounts are impacted, assessing the potential impact on your organization.
- Isolation and containment. Cut off the hackers’ access points by disconnecting compromised devices from the network. Revoke access to compromised accounts, and segment the network to contain the threat.
- Detailed investigation. Trace the attacker’s activities by analyzing logs and forensic data. Identify how hackers compromised credentials, and assess what hackers did while they had access.
- Communication and notification. Remember, transparency breeds trust, while secrecy breeds suspicion. With this in mind, give all relevant stakeholders clear, factual updates, including senior management, legal teams, and affected users.
- Eradication and recovery. Start rebuilding your security systems, making them stronger. Reset passwords for all compromised accounts, patch exploited vulnerabilities, restore systems from clean backups, and implement multi-factor authentication.
- Post-incident review. The best defense against a future attack is learning from a current breach. After a breach, analyze your incident response process, update your response plan, and implement additional security measures based on lessons learned.
Scan your Active Directory to prevent future attacks
While it’s important to quickly respond to credential-based attacks, it’s even more important (and cost-effective) to prevent them altogether. By implementing multi-factor authentication, enforcing strong password policies, training your staff regularly, auditing you Active Directory frequently and properly segmenting your network, you’ll reduce your organization’s vulnerability.
But these measures aren’t enough if credentials have been compromised in previous breaches. That’s why it’s important to include scanning your Active Directory for compromised passwords in your prevention strategy.
Specops Password Policy continuously scans your Active Directory against a database of over four billion unique compromised passwords. When it identifies employees with breached passwords, the platform immediately prompts them to create new, secure credentials — eliminating a major vulnerability before attackers can exploit it.
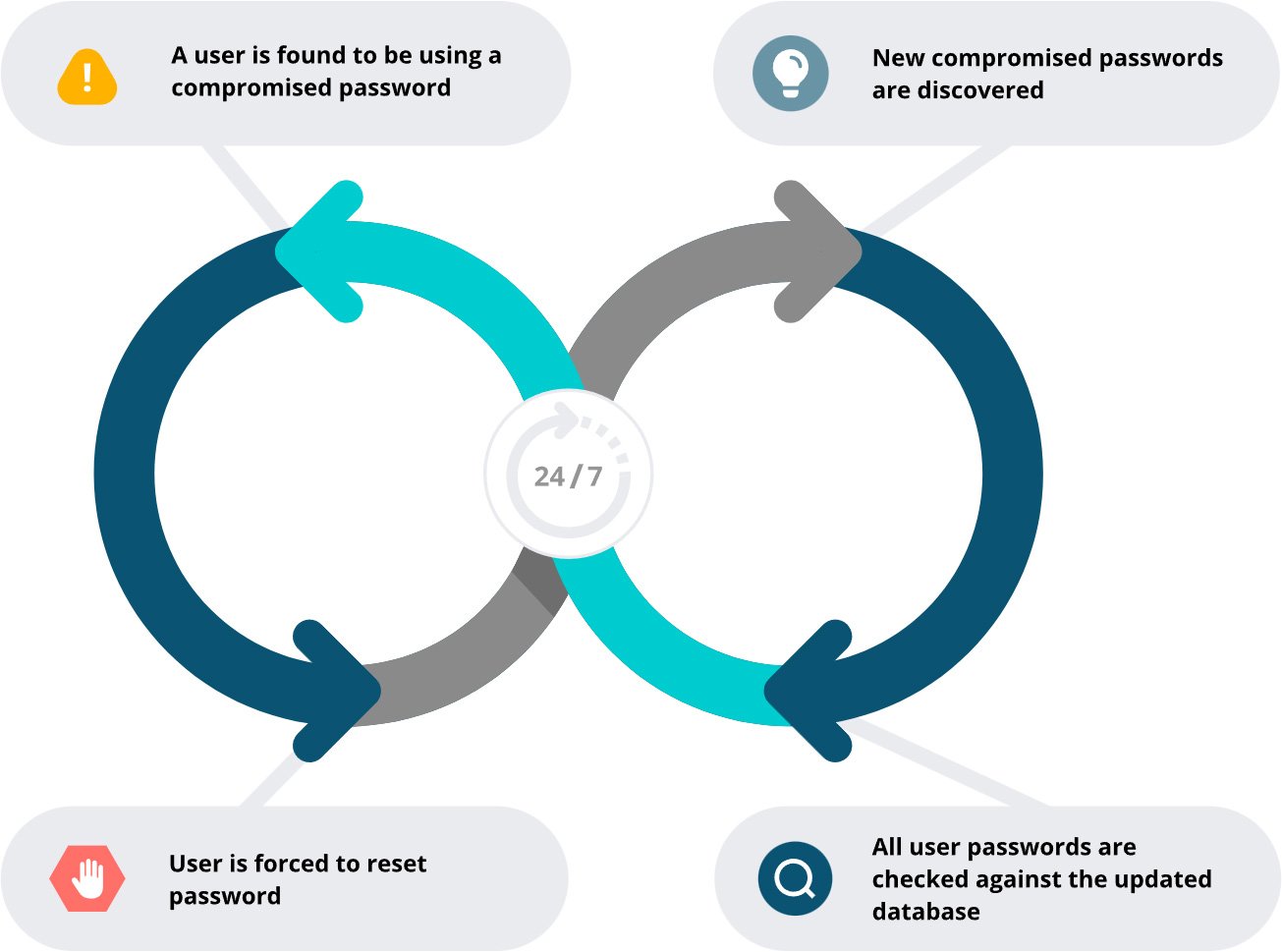
By combining traditional security measures with active credential monitoring, your organization can shield itself from credential-based attacks. Don’t wait until after a breach to secure your systems — identify and remediate password vulnerabilities before attackers exploit them.
Try Specops Password Policy for free.
Sponsored and written by Specops Software.
