Cybersecurity developers have released a new tool called “defendnot,” a successor to the previously DMCA-takedown-affected “no-defender” project.
This innovative utility leverages undocumented Windows Security Center APIs to disable Windows Defender by registering itself as a third-party antivirus solution.
The developer recently shared their journey implementing this technical workaround while traveling abroad with limited development resources.
Defendnot works by utilizing the Windows Security Center (WSC) service-a component designed to coordinate security software on Windows systems.
When a legitimate antivirus registers through WSC’s COM API, Windows automatically disables its native Defender solution to prevent conflicts.
The technical implementation required reverse engineering WSC’s validation algorithms which verify callers through multiple security checks.
According to the developer, WSC performs signature verification and examines DLL characteristics flags-specifically checking for the ForceIntegrity fla.
After testing numerous system binaries, the developer discovered that Taskmgr.exe could serve as a suitable “victim process” to host the code that makes the WSC API calls.
“There’s a WSC service in Windows which is used by antiviruses to let Windows know that there’s some other antivirus in the hood and it should disable Windows Defender,” explains the documentation, noting that these APIs remain undocumented and typically require signing an NDA with Microsoft to access.
Defendnot – Disabling Windows Defender
The developer created defendnot under unusual circumstances, working from an Airbnb in Seoul with only an M4Pro MacBook-unsuitable for x86 Windows development.
This forced them to employ creative workarounds, including borrowing remote access to a friend’s PC in the United States, resulting in debugging sessions with over 210ms latency.
“My setup looked like this: build the module in Windows ARM64 running in Parallels using MSVC, share the build artifacts with my host using shared folders, copy build artifacts using AnyDesk to the virtual machine running on my friend’s PC, debug the service using Parsec with 210ms latency,” the developer recalled.
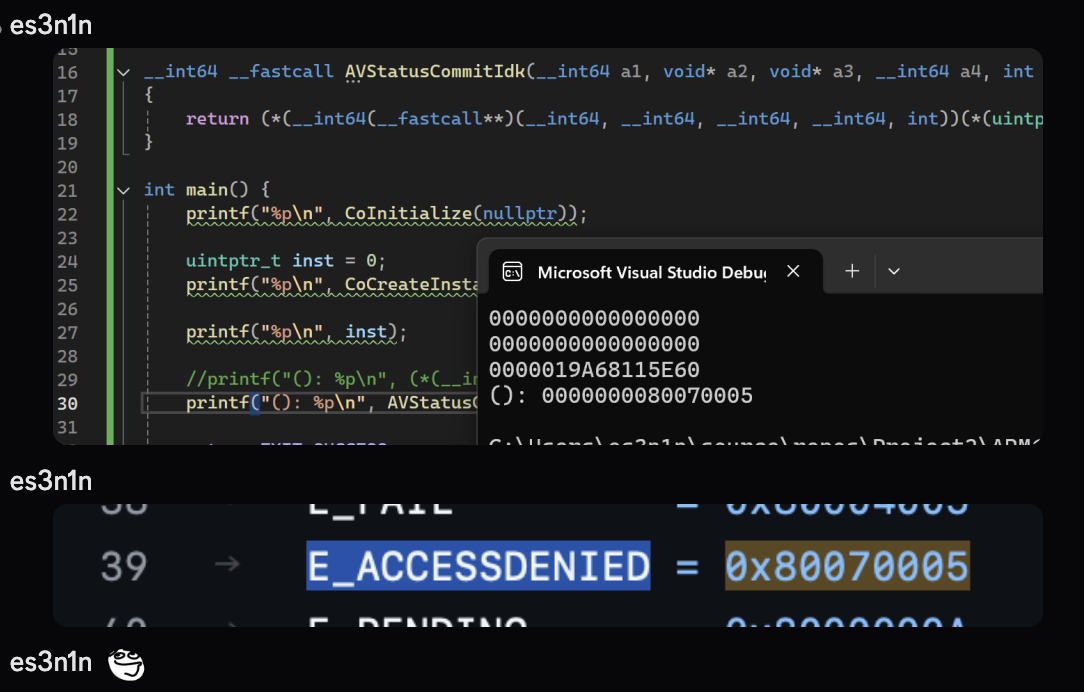
After looking into what happened after cmd.exe requested to register an antivirus in WSC, I traced down that the function.
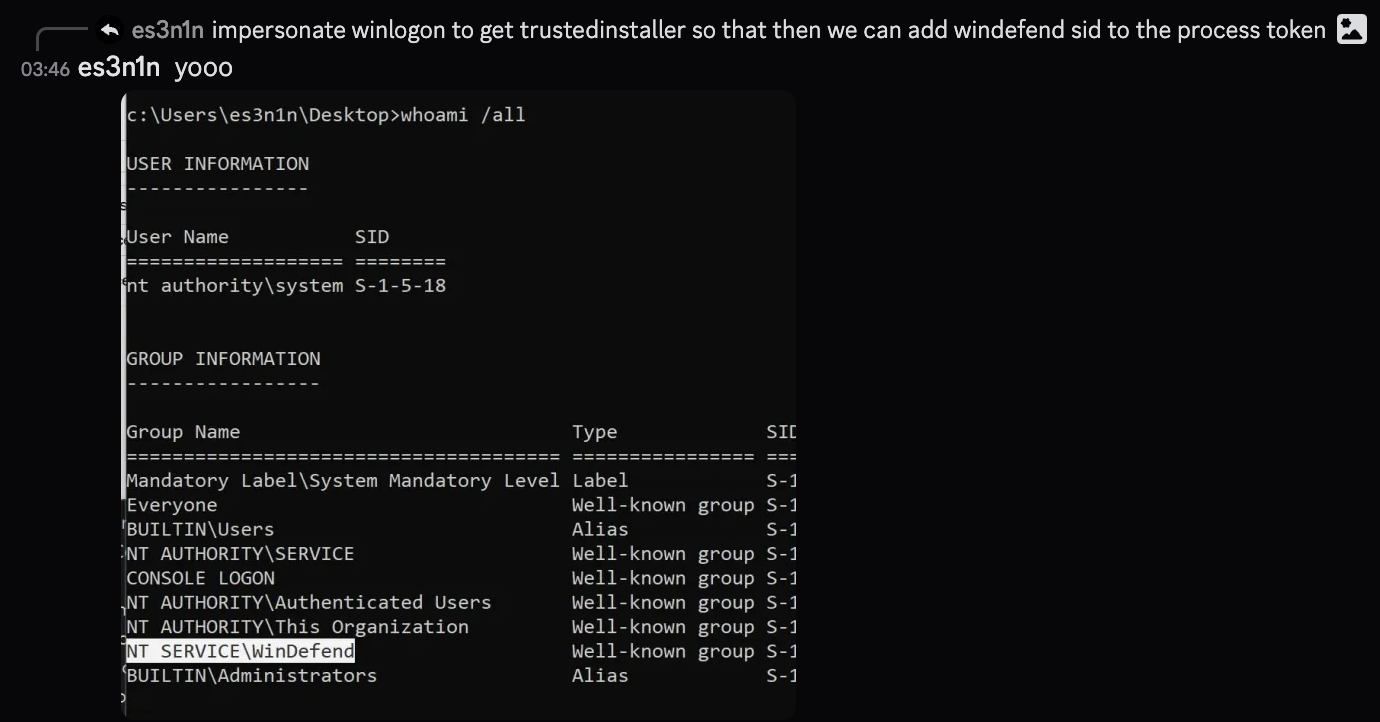
So what it’s doing is checking whether the process that is calling the RPC methods has a WinDefend SID on a token.
Eventually, the developer spent $30 on a Shadow.tech subscription to gain bare-metal access to a compatible development environment, allowing them to identify and fix critical implementation issues.
Protection Bypass and Usage Guidelines
Unlike temporary disabling methods, defendnot maintains its effect across system reboots by adding itself to Windows autorun.
“Sadly, to keep this WSC stuff even after reboot, [it] adds itself to the autorun. Thus, you would need to keep the binaries on your disk,” explains the documentation.
Users can control the tool through a command-line interface that supports various options including disabling both Windows Defender and Windows Firewall.
Available flags include –disable to revert changes, –firewall to disable the firewall, –av to disable Defender, and –name to customize the registered antivirus name.
While the original no-defender project was removed via DMCA takedown by an antivirus company whose code was being utilized, defendnot represents a “clean” implementation without using third-party antivirus code.
The developer indicates that a more detailed technical explanation of WSC’s internals will be published separately by a collaborator.
Security experts warn that while such tools demonstrate interesting technical workarounds, disabling protection mechanisms should only be done in controlled environments by users who fully understand the security implications.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
