Cisco Talos, in collaboration with The Vertex Project, has introduced an innovative approach to tackle the rising complexity of compartmentalized cyber threats.
As modern cyberattacks increasingly involve multiple threat actors executing distinct stages of an attack kill chain-such as initial access, exploitation, and ransomware deployment-traditional threat modeling frameworks like the Diamond Model have struggled to provide accurate profiling and attribution.
To address this, researchers have extended the Diamond Model by integrating a “Relationship Layer,” a novel mechanism designed to contextualize interactions between adversaries, capabilities, infrastructure, and victims.
This enhancement, detailed in a recent blog post, offers a nuanced understanding of the intricate relationships driving these sophisticated, multi-actor campaigns.
Revolutionizing Threat Modeling
The evolving cyberthreat landscape has seen a shift towards compartmentalized attack structures where financially motivated initial access (FIA) groups, malware developers, traffic distribution services (TDS), and ransomware operators collaborate through transactions like access handoffs or tooling procurement.
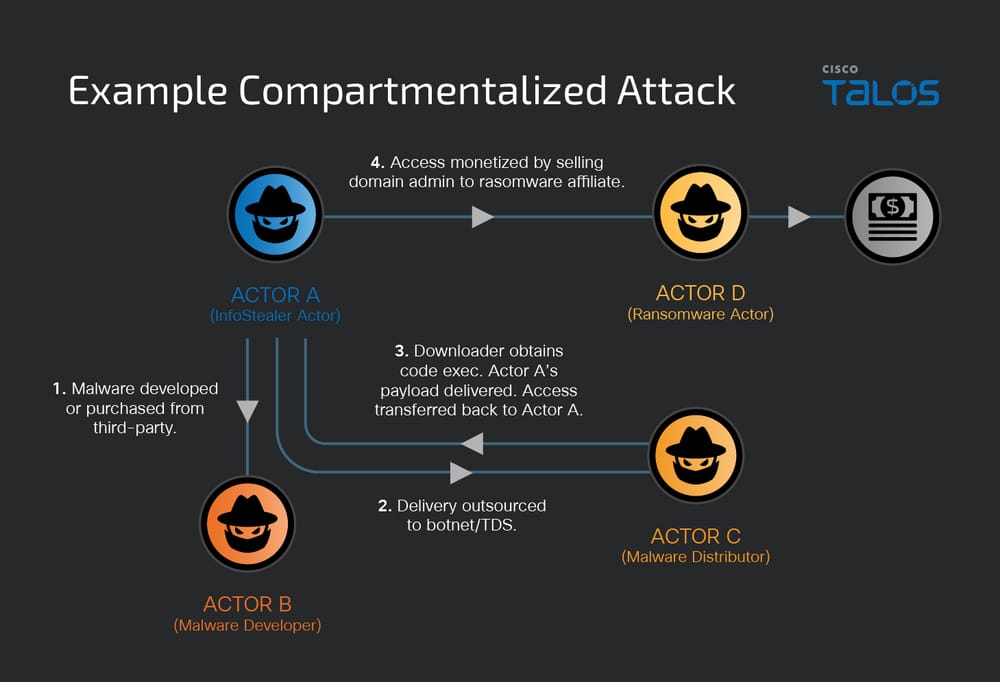
Such dynamics complicate intrusion analysis, as pivoting through traditional models often leads to misattribution of tactics, techniques, and procedures (TTPs).
For instance, infrastructure used by a TDS provider may distribute unrelated malware payloads, misleading analysts into associating them with a single actor’s capabilities.
The extended Diamond Model counters this by mapping relational dynamics-such as “purchased from” or “handover from”-between entities, ensuring accurate attribution and preventing erroneous clustering of threat activities.
This is further enriched by integrating the model with the Cyber Kill Chain framework, enabling analysts to trace each actor’s role across attack stages and anticipate potential escalations, such as a ransomware deployment following initial compromise.
The Challenges of Multi-Actor Attack Chains
According to the Report, A compelling case study highlighted by Cisco Talos is the ToyMaker campaign, investigated in 2023, which exemplified these challenges.
Initially, the deployment of the proprietary LAGTOY backdoor suggested an advanced persistent threat (APT), but subsequent ransomware activity by the Cactus group, observed three weeks later, revealed a handoff.
Notable discrepancies in TTPs, a significant time gap, and shared stolen credentials between the two waves of activity led Talos to classify ToyMaker as an FIA group, providing access to Cactus.
By applying the extended Diamond Model, researchers delineated these relationships, identifying ToyMaker’s victims as potential ransomware targets and enhancing defensive strategies through targeted threat hunting for LAGTOY infections.
This approach not only refines actor profiling but also aids defenders in prioritizing detection efforts to mitigate risks before they evolve into severe incidents.
This extended model represents a pivotal advancement for cybersecurity professionals, offering a structured method to dissect compartmentalized threats amid an era of heightened collaboration among adversaries.
By incorporating contextual relationships into threat modeling, it bridges critical gaps in understanding multi-actor intrusions, ensuring that security teams can adapt to evolving tactics.
As cyber threats grow in sophistication, such innovations are essential for maintaining robust defenses against the intricate, interconnected webs of modern cyberattacks, empowering organizations to stay one step ahead of adversaries in an increasingly fragmented threat landscape.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
