The AhnLab Security Intelligence Center (ASEC) recently made the concerning revelation that the infamous Kimsuky hacking organization was connected to a crafty phishing email campaign that targeted unwary people.
Disguised as a seemingly legitimate request for a paper review from a professor, these emails lure recipients into opening a password-protected HWP document embedded with a malicious OLE object.
Sophisticated Phishing Tactics
The document, themed around the Russo-Ukraine War, prompts the user to enter a provided password to access its contents.
.png
)
Once opened, the document covertly generates six files in the user’s temporary folder (%TEMP%), setting the stage for a deeper infection.
A deceptive “More…” hyperlink within the document body triggers the execution of a batch file named “peice.bat,” which orchestrates a series of malicious actions, including renaming files, registering scheduled tasks, and copying executables to hidden system paths like C:UsersPublicMusic.
According to ASEC Report, this initial payload is just the beginning of a sophisticated attack chain designed to evade detection and establish persistent access.
Advanced Malware Deployment
Diving deeper into the attack mechanics, the execution of “peice.bat” facilitates the deployment of additional components, including an executable renamed as “cool.exe” and a PowerShell script named “template.ps1.”
The latter collects sensitive system data, such as process lists and antivirus information, which are then exfiltrated to the attacker’s Dropbox in a formatted file.
Furthermore, a scheduled task runs “cool.exe” every 12 minutes, decoding and executing Base64-encoded data from a configuration file to launch further scripts.
In a parallel variant of the attack, another script downloads additional files from a command-and-control (C2) server, including a legitimate AnyDesk executable.
These files are strategically placed in paths like %APPDATA%MicrosoftWindows and %APPDATA%AnyDesk, with custom configuration files replacing the defaults to enable remote access.
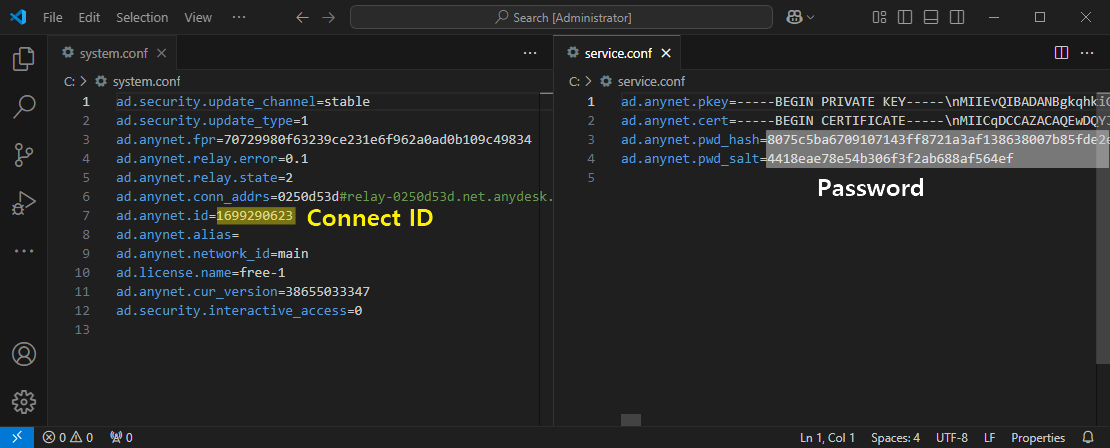
A PowerShell script hides the AnyDesk interface and tray icon, rendering the remote control invisible to the user unless they scrutinize the process list.
This exploitation of legitimate software underscores a growing trend among threat actors like Kimsuky, who leverage trusted tools and cloud storage services as C2 infrastructure to blend into normal system activity.
The attack’s tailoring to victims’ professional interests evident in the war-themed bait document amplifies the risk of infection, making it imperative for users to exercise caution with unsolicited attachments and verify file extensions before opening them.
Indicators of Compromise (IOCs)
| Type | Value |
|---|---|
| MD5 | 50d4e3470232d90718d61e760a7a62fb, 6a84a14dd79396f85abd0e7a536d97fc, 7183295e6311ebaaea7794d8123a715e, 79573759208d78816316546a9c1f0aec, 873579b92d618bf2ed3f67b7a01d7f7a |
| URL | http://103.149.98.230/pprb/0220_pprb_man_1/an/d.php?newpa=myapp, http://103.149.98.230/pprb/0220_pprb_man_1/an/d.php?newpa=myappfest, https://niva.serverpit.com/anlab/d.php?newpa=attach, https://niva.serverpit.com/anlab/d.php?newpa=bimage, https://niva.serverpit.com/anlab/d.php?newpa=mnfst |
| FQDN | niva.serverpit.com |
| IP | 103.130.212.116, 103.149.98.230 |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
