A comprehensive security investigation has revealed widespread vulnerabilities in GitHub Actions workflows across major open source repositories, including those maintained by prestigious organizations such as MITRE and Splunk.
The discovery highlights a concerning pattern of insecure continuous integration and continuous delivery (CI/CD) configurations that expose these projects to potential supply chain attacks and unauthorized access to sensitive credentials.
The vulnerabilities center around the misuse of GitHub Actions’ pull_request_target trigger, which grants workflows access to repository secrets and elevated permissions when processing pull requests from external contributors.
.png
)
Unlike the standard pull_request event that operates in a sandboxed environment, pull_request_target executes in the context of the target repository’s base branch, providing attackers with a pathway to compromise the entire project infrastructure.
This fundamental design difference has created a security blind spot that malicious actors can exploit to gain unauthorized access to API keys, deployment credentials, and administrative tokens.
The scope of this security issue extends far beyond isolated incidents, representing a systemic problem affecting numerous high-profile open source projects.
Sysdig analysts identified that these vulnerabilities stem from a fundamental misunderstanding of GitHub Actions security models among repository maintainers, leading to configurations that inadvertently expose critical infrastructure to external threats.
The research team discovered that despite years of public documentation about these risks, many projects continue to implement dangerous workflow patterns that provide attackers with direct access to production environments and sensitive organizational data.
The attack methodology involves submitting malicious pull requests that contain crafted code designed to execute during the automated workflow process.
.webp)
When repositories utilize pull_request_target events while simultaneously checking out untrusted code from contributor forks, they create an execution environment where malicious payloads can access repository secrets and high-privilege GitHub tokens.
This combination proves particularly devastating because it allows attackers to escalate privileges, modify repository contents, and potentially propagate malicious code to downstream dependencies that rely on these compromised projects.
The impact of these vulnerabilities extends beyond individual repositories, threatening the broader open source ecosystem’s integrity and trustworthiness.
Organizations that depend on these projects for critical infrastructure components face potential exposure to supply chain attacks, where compromised repositories could serve as entry points for more extensive organizational breaches.
Pull Request Target Exploitation Mechanism
The technical foundation of these attacks lies in GitHub Actions’ pull_request_target trigger mechanism, which creates a dangerous execution context when combined with code checkout operations.
This trigger was originally designed to enable workflows to process pull requests with access to repository secrets, but its implementation creates significant security risks when improperly configured.
The vulnerability manifests when workflows explicitly check out untrusted code using parameters like github.event.pull_request.head.ref and github.event.pull_request.head.repo.full_name, effectively allowing external contributors to inject arbitrary code into privileged execution environments.
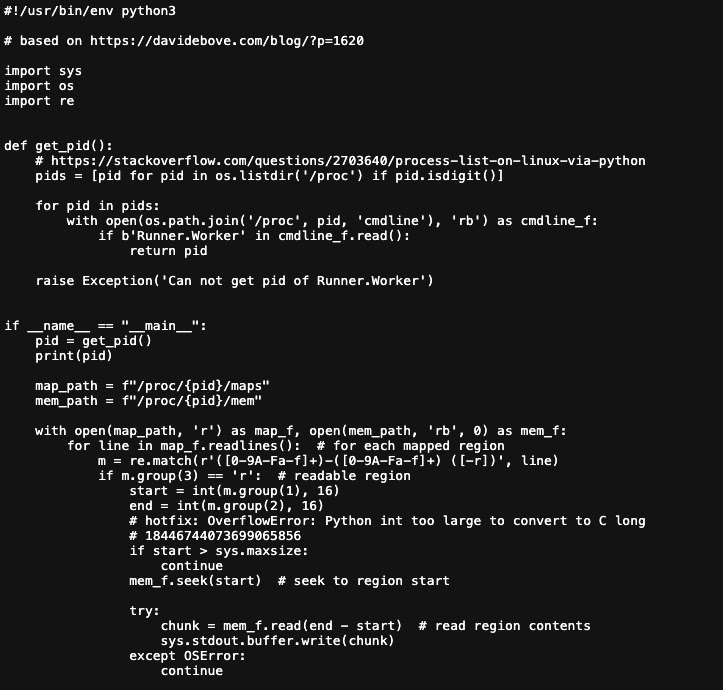
In the case of the spotipy-dev/spotipy repository, researchers demonstrated this vulnerability by modifying the project’s setup.py file to include malicious installation commands.
The exploit leveraged Python’s setuptools functionality to execute arbitrary code during the package installation process, as shown in this code snippet that extracts secrets from memory and exfiltrates them to external servers.
The malicious setup configuration included custom installation commands that downloaded and executed a memory dumping script, effectively harvesting all available secrets and GitHub tokens from the workflow environment.
The exploitation process proved remarkably straightforward across multiple repositories, with researchers successfully compromising projects from MITRE’s Cyber Analytics Repository and Splunk’s security content repository using nearly identical techniques.
Each successful attack resulted in the extraction of high-privilege GitHub tokens with comprehensive write permissions, including access to repository contents, deployments, packages, and security events.
This level of access enables attackers to completely compromise target repositories, modify source code, manipulate releases, and potentially inject malicious content into software distribution channels.
Power up early threat detection, escalation, and mitigation with ANY.RUN’s Threat Intelligence Lookup. Get 50 trial searches.
