The cyber threat group APT-C-36, widely known as Blind Eagle, has been orchestrating sophisticated cyberattacks targeting a range of sectors across Latin America, with a pronounced focus on Colombian organizations.
This group has consistently zeroed in on government institutions, financial organizations, and critical infrastructure, exploiting vulnerabilities with a blend of technical prowess and social engineering.
Their primary modus operandi involves phishing emails as an initial attack vector, often deploying various Remote Access Trojans (RATs) equipped with mechanisms to obfuscate command-and-control (C2) traffic, making detection a significant challenge for traditional security systems.

Blind Eagle’s Persistent Threat to Latin America
A notable escalation in Blind Eagle’s activities has been observed since November 2024, with a targeted campaign against Colombian entities.
In this operation, threat actors have leveraged phishing emails to distribute malicious URLs that, upon minimal user interaction, trigger the download of harmful files.
Although Microsoft patched a related vulnerability (CVE-2024-43451) in November 2024, which previously allowed the harvesting of NTLMv2 password hashes, Blind Eagle adapted swiftly.
Their updated tactics now focus on delivering malware through WebDAV requests over HTTP port 80, using the user agent ‘Microsoft-WebDAV-MiniRedir/10.0.19044’.
This protocol facilitates the transmission of malicious payloads, enabling the execution of malware on the target device.
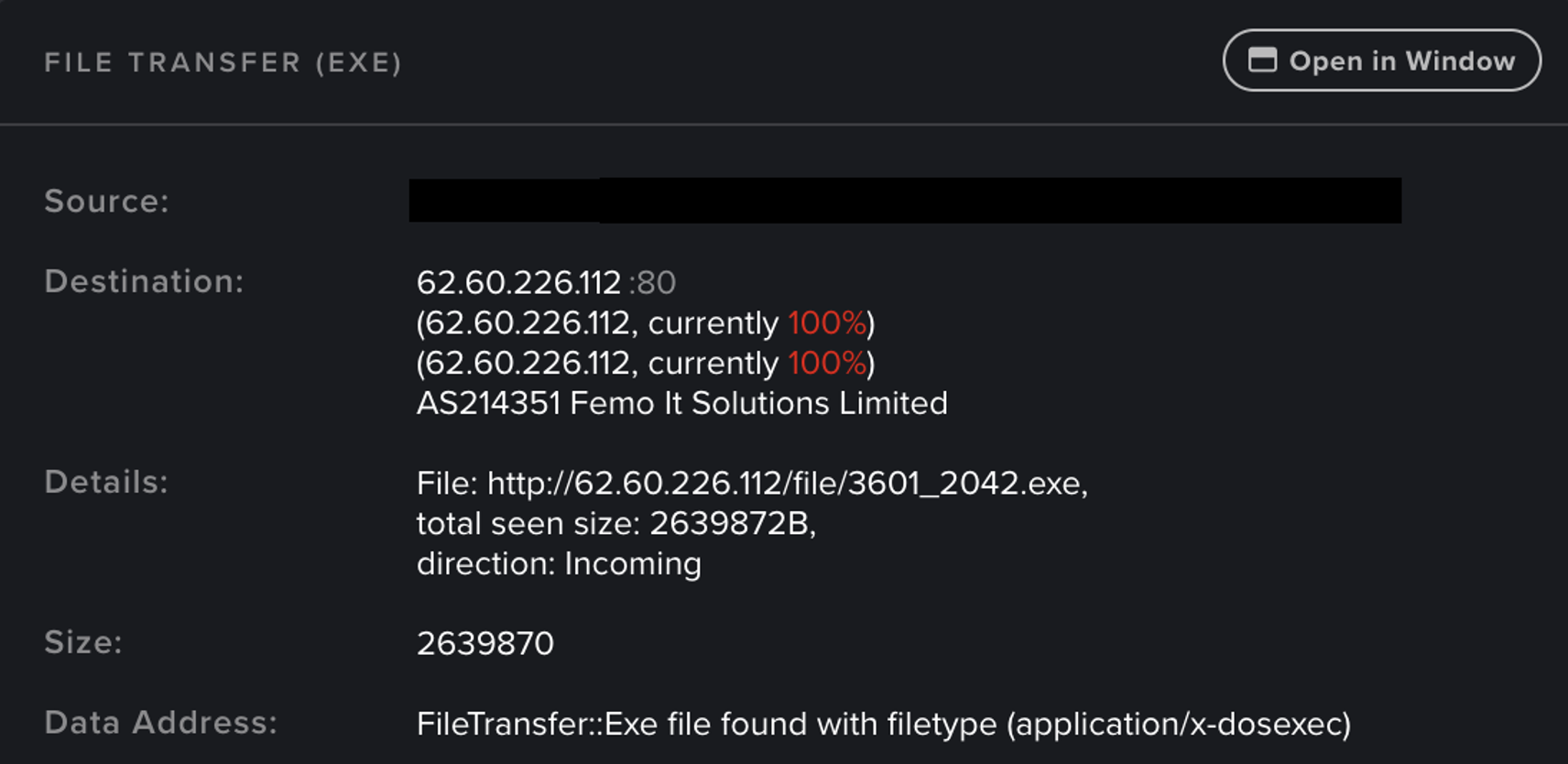
Recent Campaign Exploits Minimal Interaction Tactics
Attackers also gain visibility into their targets by receiving notifications when malicious files are downloaded, allowing them to refine their approach for subsequent attacks.
In late February 2025, Darktrace detected such activity on a Colombian customer’s network, observing suspicious redirections to a rare IP (62.60.226.112) geolocated in Germany, followed by the download of an executable file and connections to dynamic DNS endpoints like 21ene.ip-ddns.com, which are often linked to C2 infrastructure and Remcos malware.
Darktrace’s analysis further revealed a rapid escalation within a five-hour window, where the compromised device engaged in data exfiltration to endpoints such as diciembrenotasenclub.longmusic.com, transferring significant data volumes.
Without autonomous response capabilities enabled, the attack progressed until manual intervention by the customer’s security team.
This incident underscores Blind Eagle’s ability to adapt post-patch and the critical need for anomaly-based detection systems that identify behavioral deviations indicative of compromise.
Had autonomous response been active, Darktrace could have blocked suspicious external connections and halted the attack’s progression.
The persistence of Blind Eagle highlights that while timely vulnerability management is vital, it must be complemented by advanced security solutions capable of detecting and containing evolving threats in real-time, ensuring robust defense against sophisticated actors who continuously refine their tactics, techniques, and procedures (TTPs) to bypass conventional safeguards.
Indicators of Compromise (IoCs)
| IoC | Type | Confidence |
|---|---|---|
| Microsoft-WebDAV-MiniRedir/10.0.19045 | User Agent | – |
| 62.60.226.112 | IP | Medium Confidence |
| hxxp://62.60.226.112/file/3601_2042.exe | Payload Download | Medium Confidence |
| 21ene.ip-ddns.com | Dynamic DNS Endpoint | Medium Confidence |
| diciembrenotasenclub.longmusic.com | Hostname | Medium Confidence |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
