Cybercriminals are increasingly exploiting legitimate Windows driver signing processes to deploy sophisticated kernel-level malware, with new research revealing a concerning trend that has compromised over 620 drivers since 2020.
A comprehensive investigation by cybersecurity researchers has uncovered how threat actors are systematically abusing Microsoft’s Windows Hardware Compatibility Program (WHCP) and Extended Validation (EV) certificates to legitimize malicious kernel drivers, effectively bypassing traditional security defenses and gaining unprecedented system control.
Since 2020, security researchers have identified more than 620 malicious drivers, 80+ compromised certificates, and 60+ WHCP accounts associated with threat actor campaigns.
The scale represents a significant escalation in kernel-level attacks, with Group-IB’s threat intelligence investigation revealing that approximately 32% of analyzed malicious drivers functioned as loaders, capable of retrieving secondary payloads from command-and-control servers.
The abuse peaked in 2022, when over 250 drivers and approximately 34 certificates and WHCP accounts were identified as potentially compromised by security researchers.
This surge was followed by a subsequent decrease, likely due to increased industry reporting and Microsoft’s response measures.
The research has exposed a thriving underground economy for code-signing certificates, with EV certificates selling for prices ranging from $2,000 to $6,500 on criminal forums.
These certificates, which require thorough validation of a company’s legal status, are being obtained through fraudulent business registrations rather than traditional certificate theft.
Multiple vendors operate through online marketplaces, with some capable of delivering certificates in as little as 2-5 days.
The underground market has shifted from primarily selling stolen certificates to providing freshly issued ones using fake company identities, making detection significantly more challenging.
Technical Attack Sophistication
Modern kernel loaders represent a new layer of obfuscation in these attacks. These first-stage drivers are designed to load secondary components, including both unsigned drivers using reflective techniques and officially installed signed drivers.
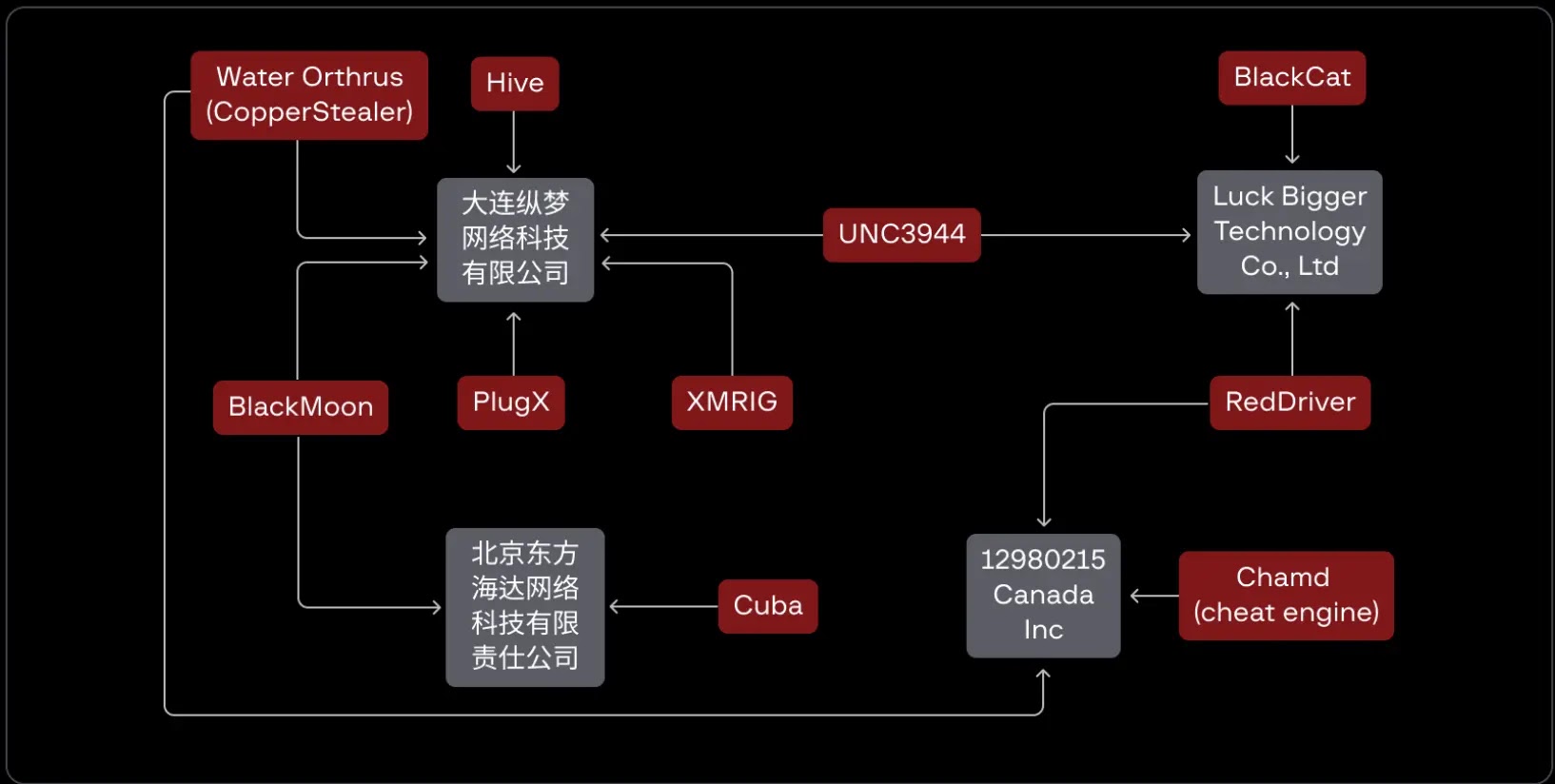
Notable examples include the Blackmoon banking trojan, which evolved to use the Hugo driver, a signed kernel loader that decrypts and loads unsigned drivers from hardcoded file paths.
The POORTRY malware family has demonstrated this evolution, transitioning from a simple EDR deactivator to a full-featured EDR wiper capable of deleting critical security software files.
Used by ransomware groups including BlackCat, Cuba, and LockBit, POORTRY represents the increasing aggression of kernel-level attacks.
Analysis reveals a significant concentration of malicious activity originating from Chinese threat actors, with most certificates and WHCP accounts tied to Chinese companies based on metadata analysis.

The FiveSys rootkit family has been particularly active, targeting China’s gaming sector while maintaining Microsoft-issued digital signatures.
Security researchers have identified overlapping infrastructure between seemingly unrelated campaigns, suggesting coordinated efforts among multiple threat actor groups using shared signing capabilities.
Microsoft has implemented several defensive measures, including the Microsoft Vulnerable Driver Blocklist, enabled by default on Windows 11 systems.
The company has also revoked numerous certificates and suspended developer accounts used in malicious campaigns.
However, the research indicates that stronger validation mechanisms are essential, particularly requiring more rigorous verification procedures for EV certificate issuance, including potential physical presence checks to ensure legitimacy.
The emergence of underground driver certificate providers highlights the resourcefulness of threat actors and reveals critical vulnerabilities in current driver-signing processes, emphasizing the urgent need for enhanced security measures in the digital certificate ecosystem.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
