The team at ANY.RUN recently reviewed a powerful Android packer called Ducex, which is linked to the infamous Triada malware, and criticized it for its sophisticated obfuscation methods.
First identified within a fake Telegram app, Ducex serves as a protective shell for Triada, one of the most sophisticated Android trojans since its debut in 2016.
Unpacking the Sophistication of Ducex
Unlike typical malware containers, Ducex is not inherently malicious but is designed to thwart detection and complicate reverse engineering efforts.
This analysis, performed using ANY.RUN’s Interactive Sandbox, reveals how Ducex employs a multi-layered approach to protect its payload, making it a significant challenge for cybersecurity professionals.
Ducex’s architecture is a masterclass in evasion, utilizing a blend of encryption, obfuscation, and anti-debugging techniques to shield the Triada payload.
The packer encrypts critical functions with a modified RC4 algorithm, supplemented by custom shuffling, rendering standard decryption tools ineffective.
Additionally, all strings within Ducex are encrypted using a sequential XOR algorithm with a dynamically changing 16-byte key, further obscuring its operations.
A Deep Dive into Ducex’s Evasion Arsenal
The payload itself is uniquely embedded within Ducex’s own classes.dex file in a large, additional section, avoiding detection as a separate entity.
This strategic storage method, combined with partial encryption of dex modules (specifically the initial 2048 bytes), ensures that key components remain hidden from static analysis.
Beyond encryption, Ducex implements control flow obfuscation with convoluted loops and conditional structures, bloating otherwise simple functions to deter manual code review.
The packer also poses significant hurdles to dynamic analysis. It performs APK signature verification to detect tampering, crashing if the app is re-signed, and employs self-debugging via fork and ptrace to prevent external tracing.
Moreover, Ducex actively scans for popular analysis tools like Frida, Xposed, and Substrate in memory, terminating execution if detected.
These anti-analysis mechanisms, paired with encrypted configurations and dual decryption processes using both modified RC4 and the lesser-known Chinese SM4 block cipher, illustrate the lengths to which its developers have gone to protect Triada.
The decryption process involves multiple stages, orchestrated through native methods like init() and dl(), before the fake Telegram app launches and Triada begins its malicious activities.
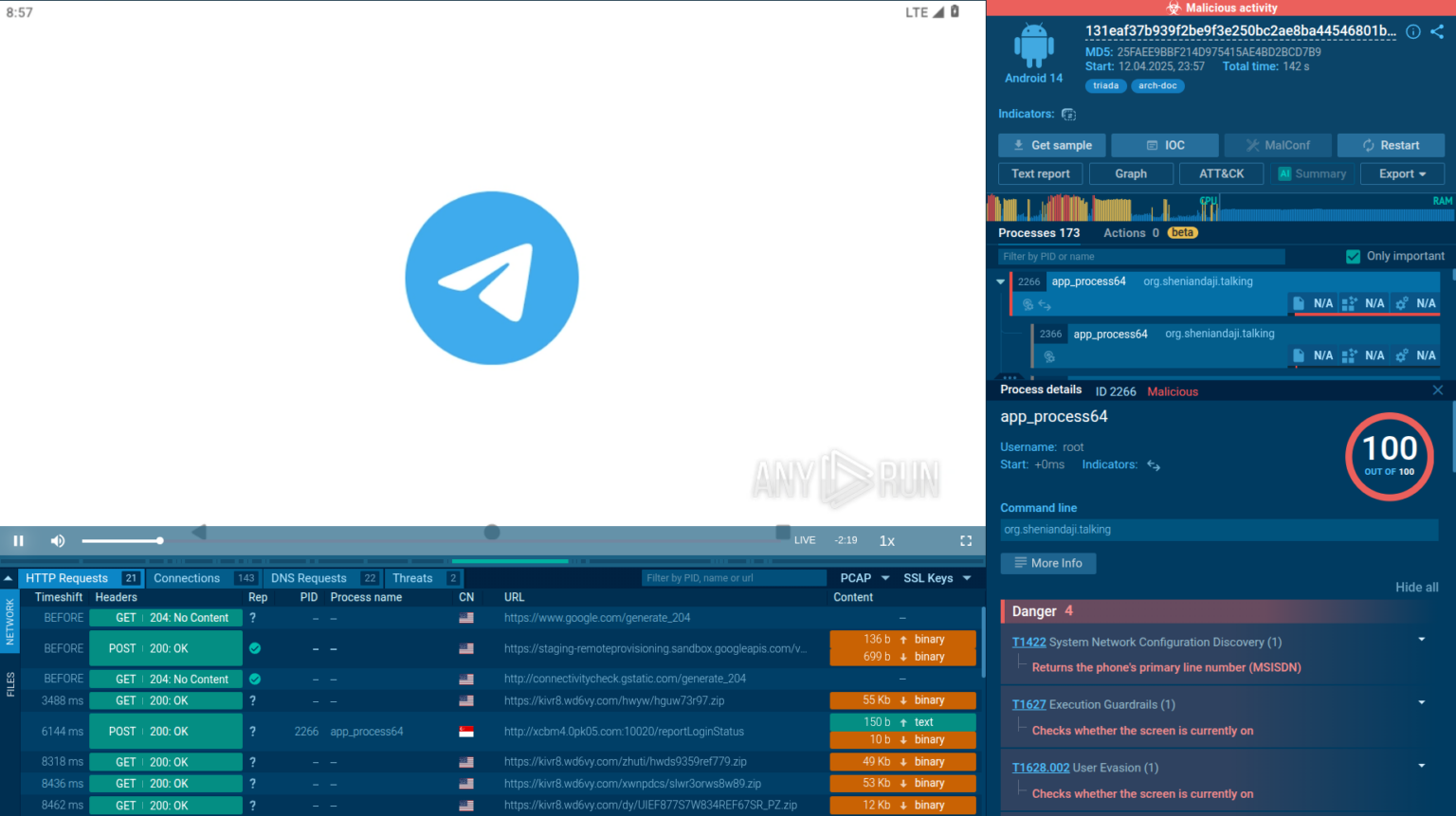
This intricate interplay of techniques underscores Ducex’s role as a formidable gatekeeper, designed to frustrate even the most seasoned researchers.
In summary, Ducex represents a highly sophisticated tool in the Android malware ecosystem, meticulously crafted to obscure Triada’s presence.
Its use of advanced encryption, anti-debugging tactics, and payload concealment highlights the evolving complexity of mobile threats, urging the cybersecurity community to adapt and innovate in response.
Indicators of Compromise (IOCs)
| Title | Description | Value |
|---|---|---|
| File Name | APK File | 131eaf37b939f2be9f3e250bc2ae8ba44546801b5ca6268f3a2514e6a9cb8b5c.apk |
| MD5 | Hash | 25faee9bbf214d975415ae4bd2bcd7b9 |
| SHA1 | Hash | 06f8ca016b2bf006702501263818b7606851f106 |
| SHA256 | Hash | 131eaf37b939f2be9f3e250bc2ae8ba44546801b5ca6268f3a2514e6a9cb8b5c |
Stay Updated on Daily Cybersecurity News. Follow us on Google News, LinkedIn, and X.
