A new ransomware threat has emerged as one of the most formidable adversaries in the cybersecurity landscape, demonstrating unprecedented growth and sophistication in its attack methodology.
SafePay ransomware, which first appeared in 2024, has rapidly evolved from a relatively unknown entity to one of the most active ransomware groups globally, claiming over 200 victims worldwide in just the first quarter of 2025.
The malware primarily targets managed service providers (MSPs) and small-to-midsize businesses (SMBs) across various industries, utilizing a combination of Remote Desktop Protocol (RDP) and Virtual Private Network (VPN) intrusion techniques to penetrate organizational networks.
The ransomware group operates with a centralized control structure, distinguishing itself from the typical ransomware-as-a-service (RaaS) model employed by many contemporary threat actors.
This operational approach allows SafePay to maintain direct oversight of its infrastructure, victim negotiations, and attack execution, resulting in more coordinated and effective campaigns.
The group’s rapid ascension to prominence was highlighted by its involvement in the high-profile attack against Ingram Micro, a global distributor serving thousands of partners and MSPs, demonstrating the malware’s capability to disrupt critical supply chain infrastructure.
Acronis analysts identified significant similarities between SafePay and the infamous LockBit ransomware family, particularly the LockBit 3.0 builder whose source code was leaked in 2022.
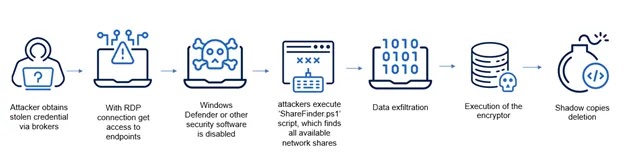
The technical analysis reveals that SafePay employs classic yet highly effective tactics, including the disabling of endpoint protection systems, deletion of shadow copies, and systematic clearing of system logs to suppress detection and incident response capabilities.
The malware’s persistence mechanisms and evasion techniques showcase a sophisticated understanding of enterprise security architectures and defensive measures.
The ransomware manifests as a PE32 DLL file with a deliberately falsified compilation timestamp, requiring specific execution parameters to function properly. SafePay implements a double extortion model, combining data exfiltration with file encryption to maximize pressure on victims.
The malware’s technical sophistication is evident in its use of living-off-the-land binaries, which allows it to blend seamlessly with legitimate system processes and evade traditional signature-based detection methods.
Infection Mechanism and Data Exfiltration
SafePay’s infection mechanism relies heavily on compromised RDP connections and VPN credentials, though the exact methods of credential acquisition remain unclear.
.webp)
Once inside the target network, the malware executes a carefully orchestrated sequence of operations designed to maximize data collection while minimizing detection.
The ransomware employs the ShareFinder.ps1 script, sourced from an open-source PowerView project, to enumerate all available network shares within the local domain.
This reconnaissance phase enables the malware to identify high-value targets and map the network infrastructure comprehensively.
The data collection process utilizes WinRAR with specific command-line parameters to archive sensitive files while excluding certain file types to optimize storage and transmission efficiency.
The archiving command systematically excludes multimedia files, executables, and other non-critical data formats, focusing instead on documents, databases, and configuration files that typically contain valuable business information.
Following the archiving process, SafePay deploys FileZilla client software to exfiltrate the compressed archives to command-and-control servers, after which both WinRAR and FileZilla are systematically removed from the compromised systems to eliminate forensic evidence.
The ransomware’s encryption routine employs a robust combination of AES and RSA algorithms, generating unique 32-byte AES keys for each file before encrypting those keys with RSA public key cryptography.
This dual-layer encryption approach ensures that even if one component is compromised, the overall security of the encrypted data remains intact.
SafePay appends the .safepay extension to encrypted files and requires a 32-byte password for full execution, implementing multiple safeguards against analysis and reverse engineering attempts.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
