Security Operations Centers (SOCs) face a fundamental challenge: distinguishing genuine threats from false positives while maintaining rapid response times.
The key to meeting this challenge lies in enriching threat data with actionable context that enables faster, more informed decision-making.
Core SOC Performance Metrics
SOC teams juggle multiple competing priorities while working under constant time pressure.
This volume creates a cascading effect where critical threats may be overlooked or deprioritized, leading to delayed response times and potentially catastrophic breaches.
Two metrics stand out as fundamental indicators of SOC effectiveness: Mean Time to Detection (MTTD) and Mean Time to Response (MTTR).
- MTTD measures how quickly security teams identify a genuine threat after it enters the environment
- MTTR tracks the time from threat identification to containment and remediation.
These metrics directly correlate with business impact shorter detection and response times mean less damage, reduced downtime, and lower recovery costs.
Industry benchmarks reveal concerning trends. The average MTTD for data breaches is approximately 207 days, while MTTR averages 70 days.
A single missed threat or delayed response can result in millions in damages, regulatory penalties, and irreparable reputation damage.
Beyond MTTD and MTTR, SOC teams track alert-to-incident ratios, false positive rates, and analyst productivity metrics.
However, MTTD and MTTR remain the most critical because they directly measure the two most important capabilities: finding threats quickly and stopping them before they cause damage.
Organizations with optimized MTTD and MTTR demonstrate superior security posture and operational efficiency.
Barriers To Optimal MTTD And MTTR
Several obstacles hinder SOCs from achieving optimal MTTD and MTTR:
- High alert volumes overwhelm analysts, leading to delays in triaging and investigating threats.
- False positives consume valuable time, diverting resources from critical incidents.
- Fragmented tools and isolated teams can create inefficiencies, as critical threat data may not flow seamlessly between groups.
- Lack of context around alerts often forces analysts to conduct time-consuming manual investigations, slowing detection and response.
- Limited visibility into attack behaviors and outdated or incomplete threat intelligence further complicate timely decision-making.
Threat Intelligence As The Source Of Game Changing Context
Threat intelligence is the cornerstone of effective threat context enrichment, transforming raw security alerts into actionable insights.
Rather than treating each alert as an isolated event, threat intelligence provides the broader context needed to understand attack patterns, attribution, and likely next steps.
The timeliness of threat intelligence directly impacts its utility for SOC operations. Contextual relevance is another critical factor. SOC teams need intelligence that relates directly to their environment.
Understanding which threats specifically target their sector, geography, or technology stack enables more focused and effective security operations.
Threat Intelligence Lookup: Comprehensive Context Enrichment
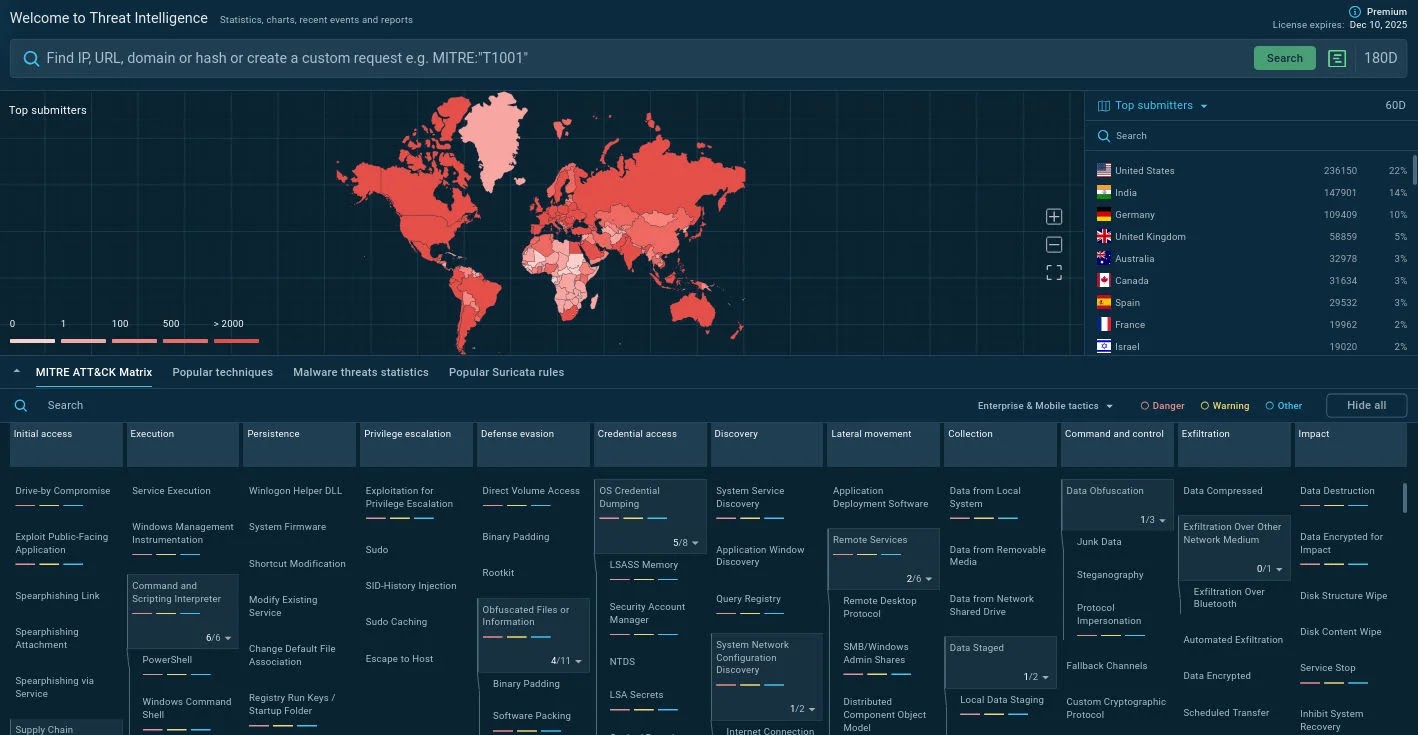
ANY.RUN’s Threat Intelligence Lookup addresses the context gap that endangers SOC efficiency by providing immediate access to data derived from real-world security investigations of 15,000 organizations worldwide.
As the teams analyze suspicious files, URLs, and other artifacts in the sandbox environment, the resulting intelligence captures real-time threat developments.
This approach ensures that SOC teams have access to the most current threat intelligence available, often identifying new threats before they appear in other sources.
See how TI Lookup speeds up triage for your team. Start using it now with free access.
Query capabilities extend beyond simple indicator lookup to include complex relationship analysis. Users can instantly access sandbox sessions that show exactly how the threat operates.
This behavioral context includes network communications, file system modifications, registry changes, and process behaviors.
Understanding these behavioral patterns enables teams to develop more effective detection rules and response strategies.
The service integrates seamlessly into existing SOC workflows, allowing analysts to query threat indicators directly within their investigation process.
SIEM systems, security orchestration platforms, and other security tools can automatically query the Threat Intelligence Lookup database to enrich alerts with relevant context.
How To Use TI Lookup For Detection And Response
Example 1: IP Instant Checkup
Complex threat investigations are intriguing, but it’s fundamental basic SOC tasks that define its efficiency and effectiveness.
The daily routine of checking network artifacts for being potential threat indicators is taken to the next level with TI Lookup. Spotted a suspicious IP connection? Just look the IP up:
destinationIP:”195.177.94.58″
.webp)
The instant “malicious” verdict is augmented by the information that it is a part of Quasar RAT inventory. It has been detected in recent malware samples and signals an actual threat.
Linked indicators like mutexes and ports are available for deeper research.
Links to sandbox sessions allow to see this exact malware strain in action and gather more indicators for security systems and detection rules.
Example 2: Suspicious Command Exposure
More ambiguous signs of possibly malicious activity can be investigated equally fast. Suppose a legitimate utility like certutil.exe is observed to retrieve content from an external URL.
An analyst queries a snippet of command line contents in TI Lookup with the CommandLine search parameter:
commandLine:”certutil.exe -urlcache -split -f http”
.webp)
The Analyses tab of the search results makes it clear that this behavior is typical for Glupteba trojan acting as a loader. Each sample analysis can be researched in depth and used for collecting IOCs.
Example 3: Registry Editing Pattern
A more complex query can contain logical operators like AND, OR, NOT.
For example, one can see what happens when an app changes Windows registry key \CurrentVersion\Run responsible for default autoruns at system startup, by adding a command that initiates a script execution chain via mshta.exe using built-in VBScript:
Query TI Lookup using RegistryKey and RegistryValue search parameters:
registryKey:”SOFTWAREMicrosoftWindowsCurrentVersionRun” AND registryValue:”mshtavbscript”
.webp)
As we can see, such registry modifications are often associated with malware evasion and persistence techniques and typical for XWorm RAT.
Key SOC Workflows Enhanced By TI Lookup
Threat Intelligence Lookup benefits SOC teams by boosting a number of key processes. Namely, it:
- Speeds up threat investigations by letting analysts quickly pivot from suspicious behaviors to related malware samples and campaigns.
- Shortens response times by providing contextual threat insights essential for fast, informed security decisions.
- Reveals hidden attack patterns by correlating small artifacts like commands or registry changes with broader malicious activity.
- Advances alert triage by helping SOC teams prioritize detections based on real-world behavior and threat prevalence.
- Supports proactive threat hunting through flexible search queries that uncover evolving obfuscation and delivery techniques.
- Improves detection coverage by uncovering trends in scripting abuse.
Start your first threat investigation with TI Lookup right away. Conclusion
Threat context enrichment fuels the shift from reactive alert processing to proactive threat intelligence-driven security.
Organizations that successfully implement comprehensive context enrichment achieve measurable improvements in MTTD and MTTR while reducing analyst workload and improving response consistency.
The key to success lies in choosing threat intelligence sources that provide current, relevant, and actionable context.
ANY.RUN’s Threat Intelligence Lookup, with its foundation in real-world security investigations and seamless sandbox integration, offers SOC teams the comprehensive context needed to excel in today’s threat environment.
