Emerging in mid-2023 as an apparent successor to Meiya Pico’s notorious MFSocket, the newly identified Android application Massistant has begun surfacing on confiscated handsets at Chinese border checkpoints and police stations.
Unlike conventional spyware that relies on covert remote delivery, Massistant is installed physically when a device is in official custody, then pairs with a Meiya Pico “Mobile Master” workstation to conduct a high-speed forensic dump.
Travellers report finding the unfamiliar icon only after their phones are returned, while forensic analysts have traced every variant to a signing certificate belonging to Xiamen Meiya Pico Information Co., Ltd.—a firm now re-branded as SDIC Intelligence yet still controlling roughly 40% of China’s digital-forensics market.
Lookout analysts noted the malware’s deliberate restriction to side-loading channels rather than Google Play, ensuring it evades automated marketplace vetting. Once launched, it immediately requests fine-grained permissions for GPS, SMS, camera roll, microphone, contacts and telephony—permissions that a uniformed officer can readily grant during the brief inspection window.
Massistant then opens a local service on TCP/10102 and waits for the desktop client to forward Android Debug Bridge (ADB) commands across the USB link, harvesting data partitions within minutes.
%20and%20MFSocket%20icon%20(bottom)%20look%20identical%20(Source%20-%20Lookout).webp)
This illustrates the identical launcher icons reused from MFSocket, underscoring the code-base lineage confirmed by shared package names and an internal XML file literally titled “mfsocket.xml.”
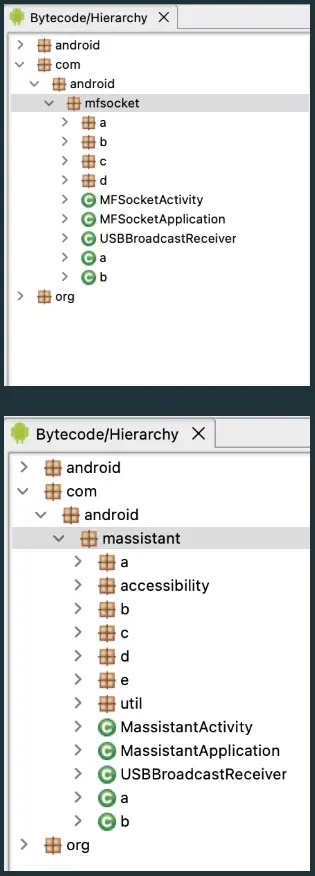%20and%20Massistant%20(bottom)%20package%20structures%20are%20similar,%20with%20additional%20packages%20added%20for%20Massistant%E2%80%99s%20more%20robust%20featureset%20(Source%20-%20Lookout).webp)
While this captures packet traces of the localhost handshake that binds handset and workstation.
Unlike commodity malware that stays resident for continued espionage, Massistant attempts to erase its footprint the moment the USB cable is removed.
A purpose-built USBBroadcastReceiver listens for the disconnect event and silently uninstalls the APK; however, anecdotal failures of this self-wipe reveal the tool to end-users and gave researchers a trove of samples to reverse-engineer.
// Auto-removal routine extracted from Massistant v8.5.7
public class USBBroadcastReceiver extends BroadcastReceiver {
public void onReceive(Context ctx, Intent i) {
if (Intent.ACTION_USB_DEVICE_DETACHED.equals(i.getAction())) {
ctx.getPackageManager()
.setComponentEnabledSetting(
new ComponentName(ctx, getClass()),
PackageManager.COMPONENT_ENABLED_STATE_DISABLED,
PackageManager.DONT_KILL_APP);
Runtime.getRuntime().exec("pm uninstall com.meyapico.massistant");
}
}
}Infection Mechanism and ADB Automation
Massistant’s most striking evolution is an “AutoClick” AccessibilityService that dismisses security dialogs automatically, guaranteeing permission grants even on hardened ROMs such as MIUI.
The native library libNativeUtil.so further exposes an ADB-over-Wi-Fi backdoor: once the forensic laptop authenticates over USB, it can switch to the device’s WLAN interface, copy auxiliary binaries and continue extraction untethered.
During laboratory testing, Lookout researchers identified hard-coded shell commands (setprop service.adb.tcp.port 5555 followed by stop adbd && start adbd) that reopen ADB in TCP mode, a feature quietly advertised on Meiya Pico’s commercial site as a 2024 “Mobile Master Series” upgrade.
The combination of USB installation, Accessibility bypass, and transient ADB-over-Wi-Fi sessions enables investigators to dump messages from Signal, Telegram and Letstalk—even when those apps encrypt local storage—before scrubbing the forensic implant.
For corporate security teams, the finding underscores the importance of “travel mode” policies that disable USB debugging, enforce strong device encryption, and perform post-trip integrity scans capable of detecting residual artifacts such as the stray mfsocket.xml or cached SQLite extracts that Massistant occasionally leaves behind.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
