A sophisticated malware campaign targeting Ivanti Connect Secure VPN devices has been actively exploiting critical vulnerabilities CVE-2025-0282 and CVE-2025-22457 since December 2024.
The ongoing attacks demonstrate advanced persistent threat techniques, deploying multiple malware families including MDifyLoader, Cobalt Strike Beacon, vshell, and Fscan to establish long-term access to compromised networks.
The attack begins with threat actors gaining initial access through vulnerable Ivanti Connect Secure devices, subsequently deploying a complex infection chain designed to evade detection and maintain persistence.
The primary payload, Cobalt Strike Beacon version 4.5, represents a customized variant that deviates from standard implementations by incorporating RC4 encryption with a hardcoded key “google” instead of the typical one-byte XOR encryption scheme.
JPCERT/CC Eyes analysts identified the malware campaign’s sophisticated execution methodology, which leverages legitimate system files and DLL side-loading techniques to mask malicious activities.
The attackers demonstrate particular attention to operational security, employing multiple layers of obfuscation and encryption to complicate analysis and detection efforts.
Advanced Loader Mechanisms and Evasion Tactics
The campaign’s technical sophistication is exemplified by MDifyLoader, a custom loader built upon the open-source libPeConv project.
.webp)
This loader implements a three-component architecture requiring an executable file, the loader itself, and an encrypted data file for successful execution.
The encryption key derives from the MD5 hash value of the executable file, creating a dependency that complicates isolated analysis.
MDifyLoader incorporates extensive code obfuscation through strategically placed junk code containing meaningless function calls and variable references.
These obfuscation techniques include relative address values and function return value references, making automated deobfuscation challenging.
The loader targets legitimate files such as Java RMI compiler (rmic.exe) and push_detect.exe to establish initial execution, demonstrating the attackers’ preference for living-off-the-land techniques.
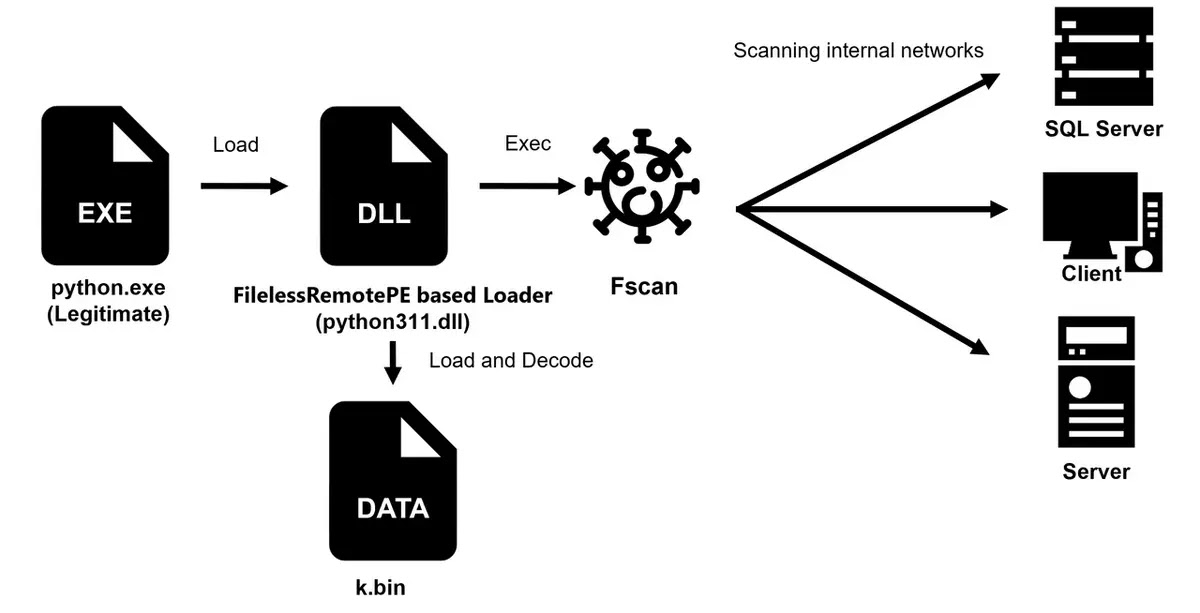
The Fscan component exemplifies the campaign’s multi-stage approach, utilizing a python.exe loader to execute the malicious python311.dll through DLL side-loading.
.webp)
This implementation, based on the FilelessRemotePE tool, includes an ETW bypass mechanism targeting ntdll.dll, specifically designed to evade endpoint detection and response solutions.
The final payload decrypts using RC4 encryption with the hardcoded key “99999999” before executing in memory.
Following initial compromise, the threat actors establish persistence through multiple mechanisms including creating new domain accounts, registering malware as Windows services, and leveraging task scheduler for periodic execution.
The campaign demonstrates sustained activity with attackers conducting brute-force attacks against Active Directory servers, FTP, MSSQL, and SSH services while exploiting the MS17-010 SMB vulnerability for lateral movement across unpatched systems.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
