A sophisticated cyberattack campaign targeting Microsoft SharePoint servers has been discovered exploiting a newly weaponized vulnerability chain dubbed “ToolShell,” enabling attackers to gain complete remote control over vulnerable systems without authentication.
Eye Security, a Dutch cybersecurity firm, identified the active exploitation on July 18, 2025, revealing what security researchers describe as one of the most rapid transitions from proof-of-concept to mass exploitation in recent memory.
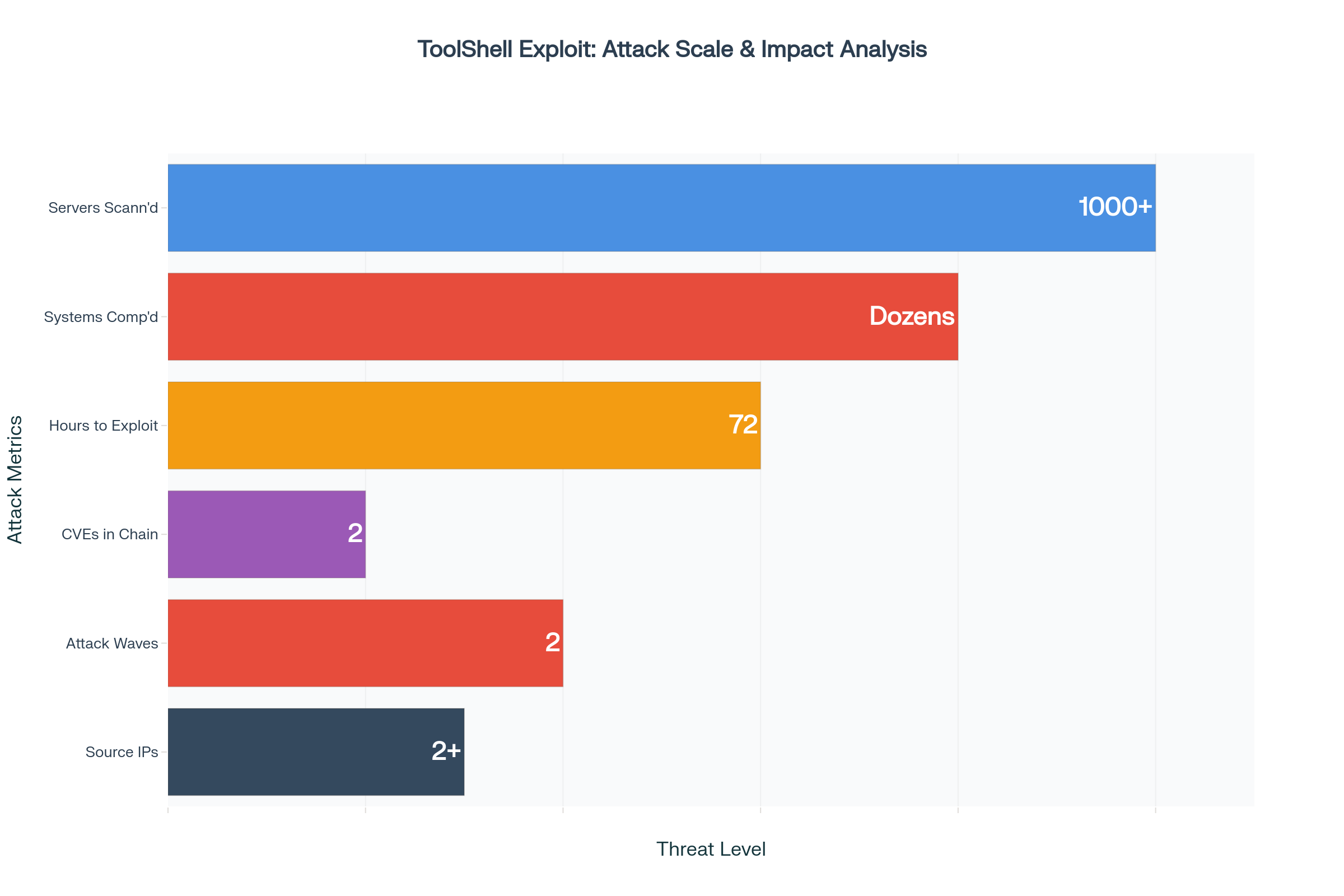
From Research to Weaponization in 72 Hours
The vulnerability chain combines two critical security flaws, CVE-2025-49706 and CVE-2025-49704, originally demonstrated at Pwn2Own Berlin 2025 in May by security researchers from CODE WHITE GmbH, a German offensive security firm.
The exploit remained dormant until July 15, 2025, when CODE WHITE publicly shared their detailed findings on social media platforms after Microsoft’s official patch release.
Within just 72 hours of public disclosure, threat actors had successfully operationalized the exploit for large-scale coordinated attacks.
Eye Security’s comprehensive investigation revealed that attackers began systematic mass exploitation on July 18, 2025, around 18:00 Central European Time, initially using IP address 107.191.58.76.
A second distinct wave of attacks emerged from 104.238.159.149 on July 19, 2025, at 07:28 CET, clearly indicating a well-coordinated international campaign.
The ToolShell exploit bypasses traditional authentication mechanisms by targeting SharePoint’s vulnerable /_layouts/15/ToolPane.aspx endpoint.
Unlike conventional web shells designed primarily for command execution, the malicious payload specifically extracts sensitive cryptographic keys from SharePoint servers, including critical ValidationKey and DecryptionKey materials.
“This wasn’t your typical webshell,” explained Eye Security researchers in their detailed technical analysis. “The attacker turns SharePoint’s inherent trust in its own configuration into a powerful weapon”.
Once these cryptographic secrets are successfully obtained, attackers can craft completely valid __VIEWSTATE payloads to achieve complete remote code execution without requiring any user credentials whatsoever.
The sophisticated attack leverages techniques similar to CVE-2021-28474, exploiting SharePoint’s deserialization and control rendering processes.
By obtaining the server’s ValidationKey, attackers can digitally sign malicious payloads that SharePoint automatically accepts as legitimate trusted input, effectively bypassing all existing security controls and defensive measures.
Eye Security’s comprehensive scan of over 1,000 SharePoint servers deployed worldwide revealed dozens of actively compromised systems across multiple organizations.
The cybersecurity firm immediately initiated responsible disclosure procedures, directly contacting all affected organizations and national Computer Emergency Response Teams (CERTs) across Europe and internationally.
Microsoft has officially acknowledged the active exploitation threat, assigning a new CVE identifier (CVE-2025-53770) to track the specific variant being used in live attacks.
The company released comprehensive security patches for all affected versions, including SharePoint Server 2016, 2019, and Subscription Edition, as part of their July 2025 security update cycle.
Organizations running vulnerable SharePoint versions must immediately apply Microsoft’s July 2025 security updates without delay. The affected builds include SharePoint 2016 versions prior to 16.0.5508.1000 (KB5002744), SharePoint 2019 versions prior to 16.0.10417.20027 (KB5002741), and Subscription Edition versions prior to 16.0.18526.20424.
Microsoft explicitly states that no alternative workarounds exist; only complete, immediate patching eliminates this critical vulnerability completely today.
Organizations must also conduct thorough, comprehensive compromise assessments immediately, as these sophisticated attacks enable persistent access that survives patching, system reboots, and standard security scans.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
