A sophisticated supply chain attack has compromised several widely-used npm packages, including eslint-config-prettier and eslint-plugin-prettier, after threat actors successfully stole maintainer authentication tokens through a targeted phishing campaign.
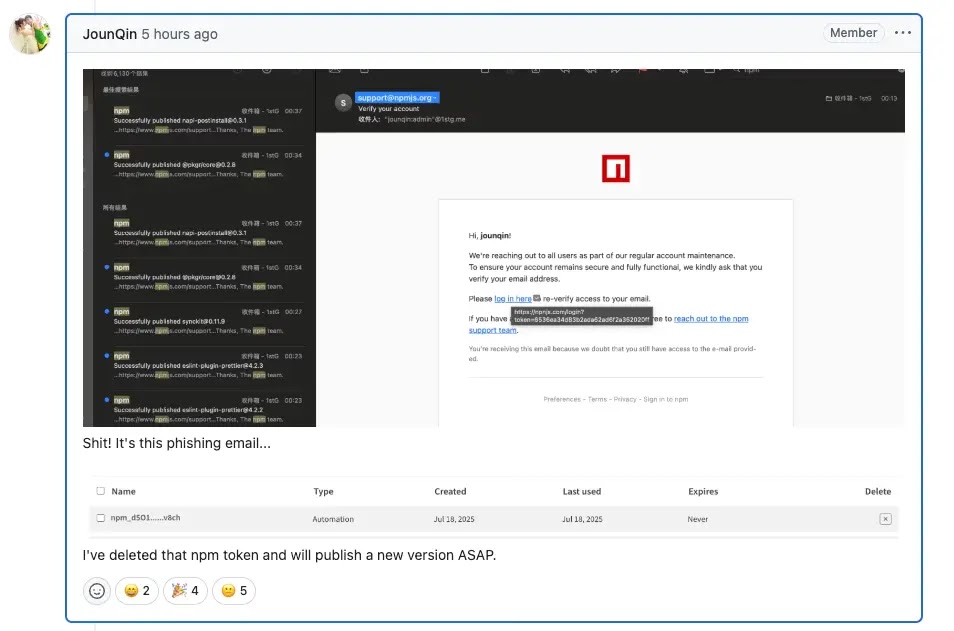
The attack leveraged a typosquatted domain, npnjs.com, designed to mimic the legitimate npmjs.org site and harvest developer credentials through convincing phishing emails.
The malicious campaign represents a multi-stage supply chain compromise that exploited the trust inherent in the npm ecosystem.
Attackers first harvested maintainer credentials through sophisticated phishing emails, then used these stolen tokens to publish malicious package versions directly to npm repositories without making any corresponding changes to GitHub repositories, making the attack significantly harder to detect through traditional monitoring methods.
.webp)
Socket.dev researchers identified the compromise after suspicious activity reports revealed that multiple versions of popular packages were published without corresponding commits or pull requests on GitHub.
The affected packages included eslint-config-prettier versions 8.10.1, 9.1.1, 10.1.6, and 10.1.7, along with eslint-plugin-prettier versions 4.2.2 and 4.2.3, synckit 0.11.9, @pkgr/core 0.2.8, and napi-postinstall 0.3.1.
The malicious code specifically targeted Windows systems with a dangerous payload designed to execute remote commands.
Analysis revealed that the injected code attempted to load and execute a DLL file named node-gyp.dll using the Windows rundll32 utility, potentially providing attackers with complete system access and the ability to execute arbitrary code on compromised machines.
Infection Mechanism
The attack’s sophistication lies in its exploitation of npm’s metadata accessibility, where registration emails and maintainer information are easily scraped by threat actors to build comprehensive target lists.
The malicious payload employed Windows-specific execution techniques, utilizing the following code pattern:-
// Simplified representation of malicious code injection
process.platform === 'win32' && require('child_process').exec('rundll32 node-gyp.dll,entrypoint');This approach enabled the malware to achieve persistence and remote code execution capabilities while remaining dormant on non-Windows systems, demonstrating the attackers’ understanding of cross-platform development environments and their ability to craft targeted payloads that maximize impact while minimizing detection across diverse development ecosystems.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
