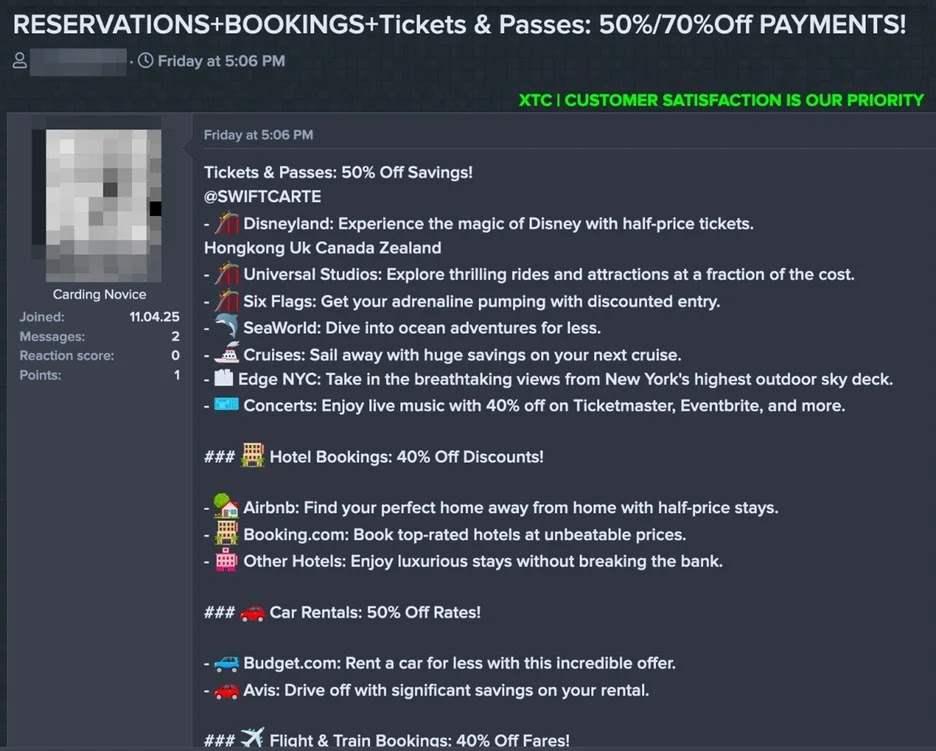
The rise of clandestine “travel agencies” on darknet forums has reshaped the cyber-crime landscape, morphing traditional card-skimming into a full-fledged service economy that sells half-priced flights, five-star hotels, and even yacht charters.
What unsuspecting buyers see as a bargain is merely the last hop of a criminal supply chain that begins with credential theft and ends with fraudulent bookings registered in legitimate airline and hotel systems.
.webp)
Early campaigns surfaced in late 2023, but activity spiked across 2024-2025 as automation frameworks let operators abuse mainstream aggregators such as Booking.com and Rentalcars.com without ever touching a public booking engine.
Attack vectors range from mass-phishing that siphons loyalty credentials to infostealer trojans that harvest stored payment tokens from browsers.
Because transactions are processed on genuine merchant APIs, conventional anti-fraud filters often clear the booking—only to charge back weeks later when the rightful cardholder disputes the bill.
The financial fallout is multilayered: airlines lose seat inventory, hotels absorb charge-backs, and travelers face drained reward balances.
SITA’s 2024 industry survey shows 66% of carriers now rank cybersecurity as their top IT spending priority, driven largely by loyalty-fraud losses rather than ransomware or DDoS concerns.
Trustwave researchers noted that one Telegram-based agency processed more than 2,000 bookings in Q1 2025 alone, netting roughly $1.4 million in illicit revenue—proof that volume, not luxury, underpins the business model.
.webp)
Trustwave’s report highlights vendors openly advertising “budget hostel” deals beside business-class seats, underscoring that any merchant with a payment page is fair game.
As soon as an aggregator patches a vulnerability or tightens 3-D Secure requirements, operators pivot to fresh card dumps or compromised reward accounts, showcasing an agile fraud-as-a-service ecosystem that regulators struggle to track.
Detection Evasion Through Proxy-Chaining Bots
At the heart of each fraudulent itinerary is a headless browser swarm that emulates legitimate customers while rotating residential proxies every few requests.
The bot first probes a booking form with fake passenger names to test stolen card numbers. If the payment gateway returns “00” (approved), the malware finalizes the ticket within the same TCP session to avoid velocity triggers.
Trustwave analysts identified that the bot randomizes user-agent strings and time-zones, then seeds browser-fingerprint entropy by injecting subtle WebGL noise—preventing device-profiling scripts used by major global distribution systems.
import requests, random, time
def book(card, trip):
session = requests. Session()
session. Headers['User-Agent'] = random.choice(UA_LIST)
session.proxies.update(next(proxy_pool))
payload = build_payload(card, trip)
r = session. Post('https://api.booking-agg.com/checkout', json=payload)
if r.json().get('code')=='00':
confirm = session.post('https://api.booking-agg.com/confirm', json={'id':r.json()['tx_id']})
return confirm.json()
time.sleep(random.uniform(0.8,1.7)) # evade rate limitsBecause the bot completes both authorization and ticketing in under eight seconds, human reviewers rarely see the transaction before the customer checks in.
Only layered counter measures—geo-fenced MFA on loyalty portals, velocity limits tied to device-ID, and dark-web telemetry that flags brand mentions—have proven effective at disrupting this high-speed fraud loop.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now



