Security researcher Bobby Gould has published a blog post demonstrating a complete exploit chain for CVE-2025-20281, an unauthenticated remote code execution vulnerability in Cisco Identity Services Engine (ISE).
The critical vulnerability was first disclosed on June 25, 2025, with Cisco warning that it impacts ISE and ISE-PIC versions 3.3 and 3.4, allowing unauthenticated, remote attackers to upload arbitrary files to the target system and execute them with root privileges.
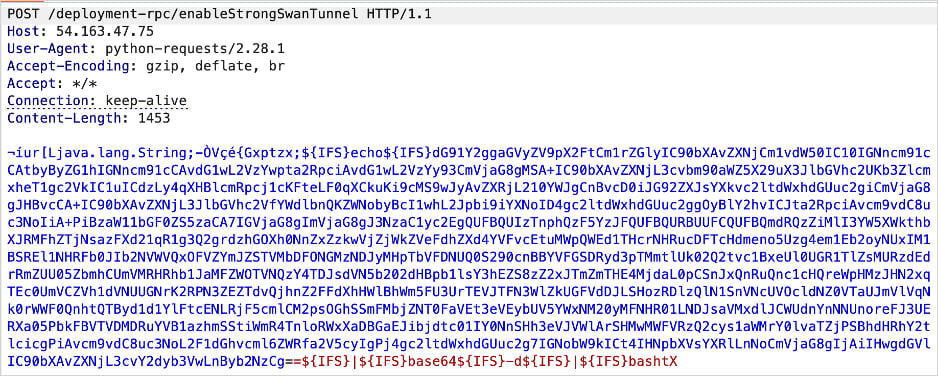
The issue stems from unsafe deserialization and command injection in the enableStrongSwanTunnel() method.
Three weeks later, the vendor added one more flaw to the same bulletin, CVE-2025-20337, which relates to the same flaw but is now broken down into two parts, CVE-2025-20281 (command injection) and CVE-2025-20337 (deserialization).
Although hotfixes were previously made available, Cisco urged users to update to 3.3 Patch 7 and 3.4 Patch 2 to address both vulnerabilities.
On July 22, 2025, Cisco marked both CVE-2025-20281 and CVE-2025-20337 as actively exploited in attacks, urging admins to apply the security updates as soon as possible.
With sufficient time having passed, allowing administrators to apply the updates, Gould has now published his write-up, where he demonstrates triggering the command injection flaw in Cisco ISE via a serialized Java String[] payload.
The researcher achieves arbitrary command execution as root inside a Docker container by exploiting the behavior of Java’s Runtime.exec() and using ${IFS} to bypass argument tokenization issues.
Finally, Gould demonstrates how to escape from the privileged Docker container and gain root access on the host system using a well-known Linux container escape technique based on cgroups and release_agent.
Source: zerodayinitiative.com
Although Gould’s write-up isn’t a weaponized exploit script hackers can directly plug into their attack chain, it provides all the technical details and payload structure necessary for skilled hackers to recreate the whole exploit.
Even if active exploitation in the wild is already underway, the release of this exploit is bound to increase malicious activity.
There are no workarounds for this vulnerability, so applying the patches as directed in the vendor’s bulletin is the recommended course of action.

CISOs know that getting board buy-in starts with a clear, strategic view of how cloud security drives business value.
This free, editable board report deck helps security leaders present risk, impact, and priorities in clear business terms. Turn security updates into meaningful conversations and faster decision-making in the boardroom.
