A sophisticated malware campaign dubbed “Efimer” has emerged as a significant threat to cryptocurrency users worldwide, employing a multi-vector approach that combines compromised WordPress websites, malicious torrents, and deceptive email campaigns.
First detected in October 2024, this ClipBanker-type Trojan has evolved from a simple cryptocurrency stealer into a comprehensive malicious infrastructure capable of self-propagation and widespread distribution.
The malware’s name derives from a comment found within its decrypted script, and its primary objective centers on cryptocurrency theft through clipboard manipulation.
When users copy cryptocurrency wallet addresses, Efimer silently replaces them with attacker-controlled addresses, effectively hijacking transactions.
Beyond its core functionality, the malware demonstrates remarkable versatility by incorporating additional modules for WordPress site compromise, email address harvesting, and spam distribution.
.webp)
Securelist analysts identified that Efimer has impacted over 5,000 users across multiple countries, with Brazil experiencing the highest concentration of attacks affecting 1,476 users.
The malware’s reach extends across India, Spain, Russia, Italy, and Germany, indicating a global threat landscape.
What distinguishes Efimer from conventional malware is its ability to establish complete malicious infrastructure, enabling sustained attacks and continuous expansion of its victim base.
The attack vectors demonstrate sophisticated social engineering techniques. Email campaigns impersonate lawyers from major companies, falsely claiming domain name trademark infringement and threatening legal action unless recipients change their domain names.
These emails contain password-protected ZIP archives with names like “Demand_984175.zip” containing malicious WSF files.
.webp)
Simultaneously, attackers compromise WordPress sites to post fake movie torrents, particularly targeting popular releases like “Sinners 2025,” which contain executable files masquerading as media players.
Technical Infection Mechanism and Persistence
The infection process begins when victims execute the malicious WSF or EXE files, triggering a complex multi-stage deployment.
.webp)
Upon execution, Efimer first checks for administrator privileges by attempting to write to a temporary file at C:WindowsSystem32wsf_admin_test.tmp.
If successful, the malware adds exclusions to Windows Defender for the C:UsersPubliccontroller folder and system processes including cmd.exe and the WSF script itself.
The malware establishes persistence through different methods depending on user privileges. For privileged users, it creates a scheduled task using a controller.xml configuration file, while limited users receive registry entries in HKCUSoftwareMicrosoftWindowsCurrentVersionRuncontroller.
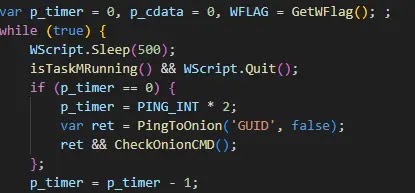
The core payload, controller.js, operates as the primary Trojan component, continuously monitoring clipboard contents every 500 milliseconds while implementing sophisticated evasion techniques, including immediate termination if Task Manager is detected running.
Efimer’s communication infrastructure relies on the Tor network, downloading the Tor proxy service from multiple hardcoded URLs hosted on compromised WordPress sites.
The malware generates unique GUIDs following the format “vs1a-” for victim identification and maintains communication with command-and-control servers at intervals of 30 minutes to avoid detection while ensuring persistent connectivity.
Equip your SOC with full access to the latest threat data from ANY.RUN TI Lookup that can Improve incident response -> Get 14-day Free Trial
