SSHAmble is a powerful open-source reconnaissance tool designed to identify and exploit vulnerabilities in SSH implementations across internet-facing systems.
Presented at DEFCON 33, this research tool has already uncovered significant security flaws in major networking equipment and exposed widespread SSH misconfigurations affecting millions of systems worldwide.
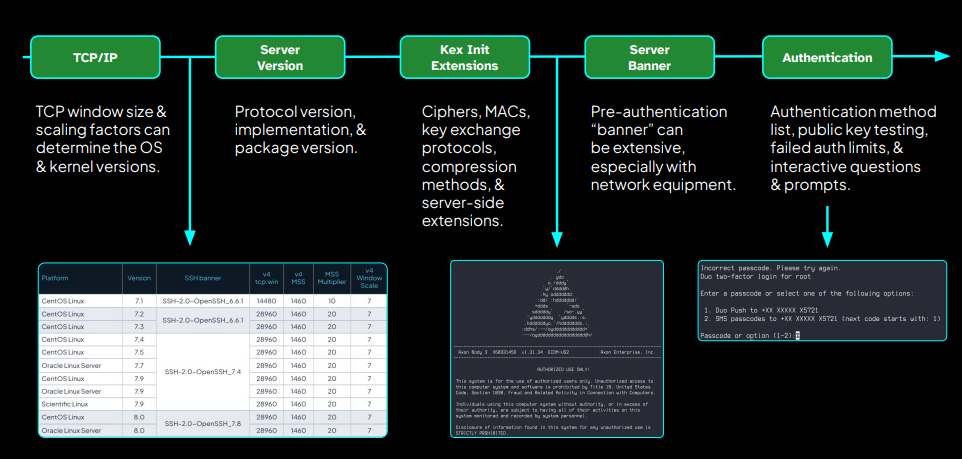
SSHamble operates by conducting comprehensive pre-authentication analysis of SSH servers, examining protocol negotiations, authentication mechanisms, and implementation-specific behaviors.
Key Takeaways
1. SSHamble is an open-source reconnaissance tool that identifies SSH protocol vulnerabilities.
2. Found zero-day flaws in networking equipment.
3. Version 2.0 offers 30+ vulnerability checks to help organizations identify SSH risks.
The tool leverages techniques including kex init parsing, authentication bypass testing, and timing analysis to identify vulnerable configurations without requiring valid credentials.
Critical Enterprise Vulnerabilities
Researcher HDMoore’s research using SSHamble has identified critical zero-day vulnerabilities in numerous enterprise-grade systems.
Notable discoveries include unauthenticated root command execution in Ruckus Wireless access points, unauthenticated remote CLI access in Digi TransPort gateways and Panasonic Ethernet switches, and authenticated remote code execution in popular Git hosting platforms like GOGS and Soft Serve.
The tool’s scanning capabilities revealed alarming statistics from internet-wide reconnaissance: approximately 22 million IPv4 addresses expose SSH on port 22, with 15.4 million successfully negotiating SSH authentication protocols.
Critically, SSHamble achieved session establishment on 48,000 systems, indicating successful authentication bypass or credential compromise.
SSHamble implements over 30 built-in vulnerability checks, including auth-none, skip-auth, pubkey-any, and vuln-tcp-forward methods. The tool can execute commands like:
Enhanced Version 2.0 Capabilities
The latest SSHamble v2.0 introduces advanced features including automatic BadKeys.info blocklist lookups, experimental blind execution vulnerability checks, and integration with Nuclei for broader security testing workflows.
The tool now supports wider algorithm negotiation testing and enhanced host key verification bypass techniques.
Moore’s findings highlight critical gaps in SSH security implementations, particularly in embedded systems and network infrastructure devices.
Many affected systems utilize hardcoded credentials, reused host keys, or suffer from pre-authentication port forwarding vulnerabilities that allow complete system compromise.
The research emphasizes the urgent need for organizations to audit their SSH configurations, implement PerSourcePenalties rate limiting (introduced in OpenSSH 9.8), and transition away from password-based authentication toward public key cryptography with proper key management practices.
SSHamble is available at the official website and has been integrated into popular security testing frameworks, enabling security professionals to identify SSH vulnerabilities before malicious actors exploit them in production environments.
Equip your SOC with full access to the latest threat data from ANY.RUN TI Lookup that can Improve incident response -> Get 14-day Free Trial
