ClickFix has emerged as one of the most dangerous and rapidly growing cybersecurity threats of 2025, representing a sophisticated evolution in social engineering attacks.
This deceptive technique has surged by an unprecedented 517% in the first half of 2025, becoming the second most common attack vector after phishing and accounting for nearly 8% of all blocked attacks.
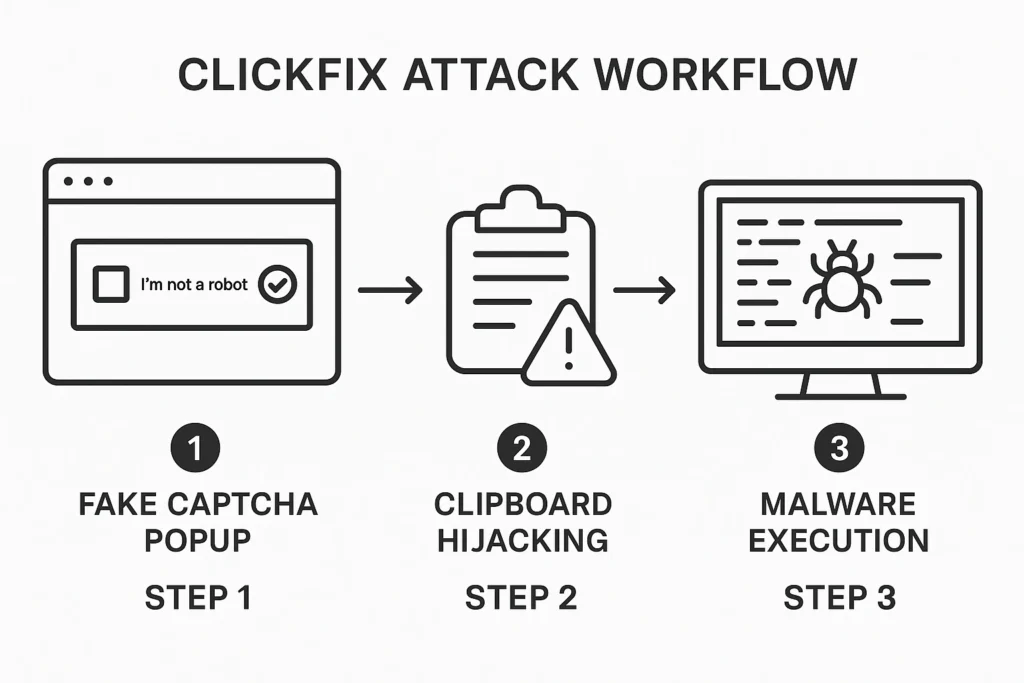
Unlike traditional malware delivery methods that rely on technical vulnerabilities, ClickFix exploits human psychology and trust, tricking users into executing malicious commands on their own devices through carefully crafted fake error messages and verification prompts.
The attack’s effectiveness lies in its ability to bypass traditional security controls by leveraging trusted system tools like PowerShell and Windows Run dialog, making detection extremely challenging.
Threat actors ranging from cybercriminals to nation-state groups including Russia’s APT28, North Korea’s Kimsuky, and Iran’s MuddyWater have adopted this technique to deploy various malware families including Lumma Stealer, DarkGate, NetSupport RAT, and AsyncRAT.
The Clickfix Social Engineering Tactic
ClickFix represents a masterclass in psychological manipulation, exploiting users’ natural desire to solve problems independently rather than alerting IT teams.
The attack typically begins when users encounter what appears to be a legitimate error message or verification prompt while browsing websites, opening email attachments, or clicking on malicious advertisements.
Here’s a comprehensive table for The ClickFix Social Engineering Tactic section:
| Tactic Element | Implementation Method | Psychological Manipulation | Target Vulnerability | Success Indicators |
|---|---|---|---|---|
| Fake Error Messages | Creates convincing error dialogs claiming browser updates, document access failures, or system problems requiring immediate attention | Exploits user desire to resolve technical problems quickly and independently | Users who prefer self-service solutions over IT support requests | High click-through rates on fake error messages across diverse user populations |
| CAPTCHA Impersonation | Presents fake reCAPTCHA verification screens with “Verify You Are Human” or “I’m not a robot” messages | Leverages familiarity with legitimate verification systems to reduce suspicion | Users conditioned to complete CAPTCHA verifications for website access | Effective bypass of user skepticism through familiar verification interface design |
| Urgency and Authority | Creates artificial time pressure suggesting immediate action required to prevent data loss, security breaches, or system failures | Reduces critical thinking through psychological pressure and artificial deadlines | Users prone to anxiety about system security and data protection | Increased compliance rates when time-sensitive language is incorporated |
| Trust Exploitation | Mimics interfaces and messages from well-known technology companies like Microsoft, Google, and legitimate software applications | Exploits established trust relationships with familiar technology brands and services | Users with high trust levels in established technology companies | Higher success rates when impersonating widely-used and trusted platforms |
| Interface Mimicry | Incorporates official-looking logos, color schemes, and language patterns that mirror legitimate communications | Creates cognitive bias through visual similarity to authentic interfaces | Users who rely on visual cues for authenticity verification | Reduced detection rates due to authentic visual appearance |
| Problem-Solution Framework | Positions users as problem-solvers who can independently fix issues without alerting IT teams | Appeals to user autonomy and technical competence while avoiding organizational oversight | Users who want to demonstrate technical capability and avoid dependency on IT teams | Enhanced user engagement through empowerment messaging and technical autonomy |
This table demonstrates how ClickFix social engineering tactics systematically exploit fundamental human psychological traits and behavioral patterns, making it one of the most effective cybersecurity threats in the current landscape. Each tactic element works synergistically to overcome user skepticism and security awareness training.
Clipboard Injection and Command Execution
The technical sophistication of ClickFix lies in its clipboard manipulation mechanism, a process known as “pastejacking”. When users interact with the malicious prompt, JavaScript code silently executes in the background to populate their clipboard with malicious commands.
| Phase | Technical Process | Technical Details | Security Bypass Method |
|---|---|---|---|
| JavaScript Payload Deployment | Malicious websites inject JavaScript code that monitors user interactions with fake error messages or CAPTCHA prompts | Hidden JavaScript monitors DOM events, remains undetected until trigger activation | Operates within browser security context without exploiting vulnerabilities |
| Automatic Clipboard Population | Upon clicking “Fix” button, JavaScript executes copyToClipboard function replacing clipboard content with malicious PowerShell command | Base64-encoded PowerShell commands silently replace clipboard contents using browser APIs | No file downloads or suspicious network activity until user executes command |
| Command Obfuscation | PowerShell scripts use Base64 encoding and obfuscation techniques like atob() method to decode strings | Multiple encoding layers include legitimate commands like “ipconfig /flushdns” to mask malicious activities | Legitimate-looking commands mixed with malicious code evade static analysis |
| User Instruction Sequence | Interface guides users: Press Win+R → Press Ctrl+V → Press Enter to execute the pasted command | Step-by-step visual instructions exploit user trust and create sense of technical legitimacy | Social engineering bypasses technical controls by relying on user compliance |
| Silent Execution | Command leverages trusted Windows utilities (mshta.exe, PowerShell) to download and execute payloads from remote servers | Uses Microsoft HTML Application Host and trusted system tools to bypass security controls | Trusted Windows utilities execute malicious code without triggering security alerts |
This table illustrates how each phase of the ClickFix clipboard injection process operates at a technical level while simultaneously explaining the security bypass mechanisms that make this attack vector so effective against traditional cybersecurity defenses.
The clipboard injection technique is particularly insidious because it operates entirely within the browser security context until the final execution step. Modern browsers’ security features cannot detect this social engineering approach since no actual vulnerability exploitation occurs.
ClickFix Malware Attacks
Real-world ClickFix campaigns have demonstrated the technique’s versatility in delivering diverse malware payloads across multiple infection vectors.
The attack methodology has been adopted by both cybercriminal organizations and state-sponsored threat groups, resulting in significant security incidents worldwide.
Major Campaign Examples:
Lumma Stealer Distribution Network: Microsoft Threat Intelligence documented a sophisticated campaign in April 2025 that combined EtherHiding (blockchain payload storage) with ClickFix social engineering.
The operation compromised numerous websites and used Binance Smart Chain contracts to host malicious code, making traditional blocking methods ineffective.
.webp)
Healthcare Sector Targeting: The U.S. Department of Health and Human Services reported multiple ClickFix campaigns specifically targeting healthcare organizations. These attacks impersonated medical software updates and electronic health record system notifications, leading to the deployment of DarkGate malware and Vidar Stealer. The campaigns successfully compromised over 300 healthcare facilities globally.
Swiss Ricardo Marketplace Campaign: Security researchers identified a German-language ClickFix operation targeting Swiss organizations by impersonating the Ricardo e-commerce platform. Victims received legitimate-looking emails about marketplace activities, which led them to fake CAPTCHA pages. The campaign deployed AsyncRAT and PureLog Stealer through ZIP files hosted on Dropbox.

- Russian APT28: Utilized ClickFix in campaigns targeting Ukrainian government entities, distributing Lucky Volunteer information stealer through fake document sharing notifications.
- North Korean Kimsuky: Posed as Japanese diplomats in conversation-based social engineering, eventually directing targets to ClickFix-enabled sites deploying Quasar RAT.
- Iranian MuddyWater: Incorporated ClickFix into broader espionage campaigns targeting critical infrastructure.
Malware Payload Diversity: ClickFix campaigns have successfully delivered:
- Information Stealers: Lumma Stealer, SnakeStealer, RedLine Stealer, and Vidar Stealer for credential harvesting.
- Remote Access Trojans: NetSupport RAT, AsyncRAT, DarkGate, and SectopRAT for persistent system control.
- Banking Malware: DanaBot for financial fraud operations.
- Ransomware: Interlock ransomware group adopted ClickFix for initial access in corporate environments.
- Post-Exploitation Tools: Havoc C2 framework for advanced persistent threat activities.
Attack Statistics and Impact:
ESET telemetry data reveals that ClickFix attacks are concentrated in specific geographic regions, with the highest detection volumes in Japan, Peru, Poland, Spain, and Slovakia.
The technique’s effectiveness has led to the development of commercial ClickFix builders sold on underground forums, enabling less technically skilled cybercriminals to launch sophisticated social engineering campaigns.
ReliaQuest research indicates that ClickFix has become so prevalent that it now drives the success of emerging malware families like SectopRAT, which experienced significant growth in 2025 primarily due to ClickFix delivery campaigns.
The technique’s ability to bypass email filters, endpoint protection systems, and network security controls has made it a preferred method for initial access across the cybercriminal ecosystem.
The rapid adoption and success rate of ClickFix attacks underscore a fundamental shift in the threat landscape, where social engineering sophistication has surpassed technical exploitation as the primary means of system compromise.
Organizations must adapt their security strategies to address this human-centric attack vector that exploits trust and familiarity rather than software vulnerabilities.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.
