A new cyber-espionage threat group has been using a new backdoor malware that provides persistent access through a seemingly inactive scheduled task.
The threat actor’s operations appear to support Russian interests by targeting government and judicial bodies in Georgia, and energy firms in Moldova.
The attacker is currently tracked as Curly COMrades and has been active since mid-2024 and is using a custom three-stage mallware component that researchers call MucorAgent.
Curly COMrades attack chain
In a report today, cybersecurity company Bitdefender describes MucorAgent as a “complex” piece of malware “engineered as a .NET stealthy tool capable of executing an AES-encrypted PowerShell script and uploading the resulting output to a designated server.”
The researchers named the threat actor Curly COMrades due to the heavy use of the curl.exe tool for data exfiltration and communicating with the command-and-control (C2) server, and because of hijacking Component Object Model (COM) objects during the attack.
While no strong overlaps with known Russian APT groups have been found, the researchers say that the threat “group’s operations align with the geopolitical goals of the Russian Federation.”
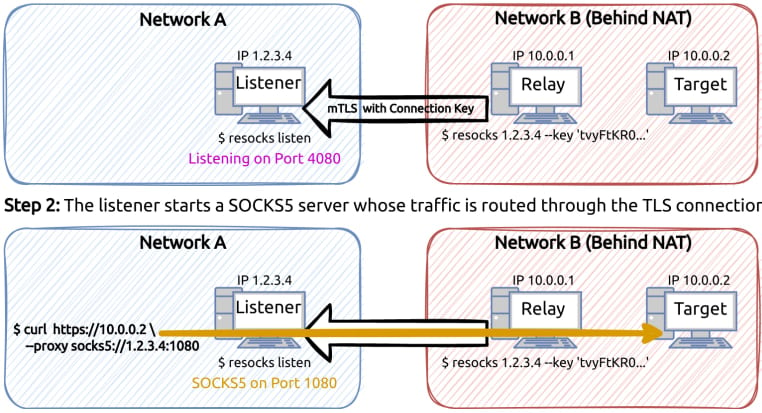
The researchers couldn’t determine the initial access vector but observed the installation of multiple proxy agents, including the Go-based Resocks, across internal systems.
Resocks is retrieved via curl.exe and registered as scheduled tasks or Windows services for persistence, communicating with the C2 via TCP 443 or 8443.
For redundancy, the hackers also deploy custom SOCKS5 servers and SSH + Stunnel for remote port forwarding.
Some SSH connections are routed through a custom tool, CurlCat, which uses the libcurl library and a custom Base64 alphabet to obfuscate traffic by relaying it through compromised legitimate websites.
Source: Bitdefender
Inconsistent persitence mechanism
Bitdefender notes that the persistence mechanism they discovered was an erratic one as it was achieved by hijacking CLSIDs to target NGEN (Native Image Generator).
NGEN is a default Windows .NET Framework component for pre-compiling assemblies, and can offer persistence through a disabled scheduled task.
However, even if the task appears inactive, the operating system enables and executes it at random intervals (e.g. idle times, when deploying a new app), the researchers explain.
“Given this unpredictability, it is probable that a secondary, more predictable mechanism for executing this specific task also existed” – Bitdefender
In some cases, the attackers also installed the legitimate Remote Utilities (RuRat) remote monitoring software to maintain interactive control.
Additionally, they used the Remote Monitoring and Management (RMM) tool, a legitimate utility widely used by IT professionals to monitor, manage, and maintain client IT assets, such as servers, desktops, and mobile devices.
Stealthy MucorAgent .NET backdoor
The MucorAgent backdoor consists of three components, that can hijack a legitimate COM handler and load a second .NET stage that executes a component for bypassing the Antimalware Scan Interface (AMSI) in Windows.
The third payload looks in specific locations for index.png and icon.png files, which are encrypted data blobs (likely scripts) downloaded from compromised websites.
Acording to Bitdefender, the attacker collected valid credentials, likely in an attempt to move around the network, steal and exfiltrate data.
They note that the threat actor “repeatedly tried to extract the NTDS database from domain controllers” and “attempted to dump LSASS memory from specific systems to recover active user credentials.”
Bitdefender also observed the execution of living-off-the-land commands like netstat, tasklist, systeminfo, wmic, and ipconfig, along with PowerShell Active Directory enumeration cmdlets, and batch scripts used for automation.
Although Curly COMrades’ operations were part of a larger espionage campaign, the researchers underline that the threat actor put in extensive effort to maintain their access to the target.
Nevertheless, despite using LOLbins and open-source tools that blend well with regular traffic, and the smart persistence mechanism, the group’s malicious moves still generated sufficient noise to be picked up by modern EDR/XDR sensors.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
