Trustwave SpiderLabs researchers have uncovered a sophisticated EncryptHub campaign that ingeniously abuses the Brave Support platform to deliver malicious payloads, leveraging the recently disclosed CVE-2025-26633 vulnerability in Microsoft Management Console (MMC).
Dubbed MSC EvilTwin, this flaw enables attackers to execute arbitrary code via manipulated .msc files, allowing EncryptHub also known as LARVA-208 or Water Gamayun to infiltrate systems through a blend of social engineering and technical exploitation.
The group, which has compromised over 618 organizations worldwide since February 2025, targets sectors including Web3 developers and gaming platforms like Steam, deploying infostealers and ransomware.
Threat Group Exploits Social Engineering
In this latest operation, attackers impersonate IT support via Microsoft Teams requests, establishing remote sessions to execute PowerShell commands that fetch and run scripts from domains like cjhsbam[.]com.
These scripts drop benign and malicious .msc files, exploiting MMC’s path resolution to load payloads from deceptive directories such as en-US folders, ultimately retrieving encrypted commands from C2 servers for persistence and data exfiltration.
The attack chain begins with a PowerShell invocation bypassing execution policies to download runner.ps1, which plants dual .msc files one legitimate and one altered to replace placeholders like “htmlLoaderUrl” with C2 URLs pointing to build.ps1.
This secondary script harvests system details, decrypts AES-encrypted instructions, and deploys tools like Fickle Stealer, a PowerShell-based infostealer targeting sensitive files, cryptocurrency wallets, and browser data.
SpiderLabs’ analysis reveals EncryptHub’s evolution from script-based loaders to Golang-compiled binaries, including SilentCrystal, which creates mock directories mimicking “C:Windows System32” (note the trailing space) to evade detection.
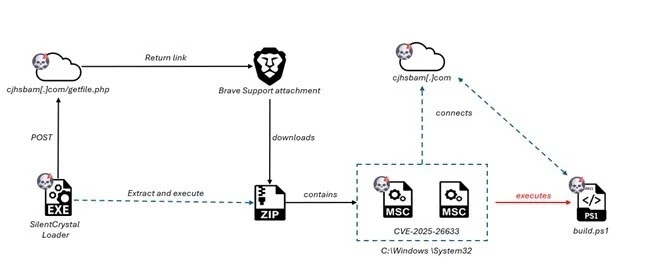
SilentCrystal abuses Brave Support by uploading ZIP archives containing payloads, using hardcoded API keys to fetch download links and execute them via the MMC vulnerability.
This tactic circumvents restrictions on new user uploads, indicating the actors maintain privileged accounts on the platform for stealthy distribution.
Backdoors Enhance Persistence
Further pivoting from C2 infrastructure uncovered additional Golang tools, such as a SOCKS5 proxy backdoor operating in client or server modes.
In client mode, it connects to hardcoded C2 endpoints, relaying machine info including username, domain, admin rights, public IP, geolocation, and ISP via Telegram notifications formatted for rapid attacker assessment.
Server mode establishes a SOCKS5 tunneling setup with self-signed TLS certificates using “Reverse Socks” as the common name, facilitating concurrent connections through goroutines for scalable command-and-control.
Associated domains like safesurf.fastdomain-uoemathhvq.workers.dev host payloads such as pay.ps1, which generate fake browser traffic to mask C2 activity while displaying decoy pop-ups like “System Configuration” installations.
SpiderLabs also identified rivatalk.net, a fake video conferencing site registered in July 2025, impersonating legitimate platforms to deliver MSI installers requiring access codes.
These installers sideload malicious DLLs via Symantec’s ELAM binary, spawning PowerShell to fetch and execute encrypted payloads that maintain persistent C2 connections.
This multi-layered approach underscores EncryptHub’s adaptability, combining social lures with zero-day exploits to bypass defenses.
As campaigns intensify, organizations must prioritize patching CVE-2025-26633, enhancing user training against impersonation, and deploying behavioral analytics to detect anomalous PowerShell and MMC executions.
Trustwave emphasizes proactive threat hunting aligned with MITRE frameworks to counter such evolving adversaries.
Indicators of Compromise (IOCs)
| Type | Indicator |
|---|---|
| Domain | rivatalk.net |
| Domain | 0daydreams.net |
| Domain | cjhsbam.com |
| Domain | safesurf.fastdomain-uoemathhvq.workers.dev |
| IP | 185.33.86.220 |
AWS Security Services: 10-Point Executive Checklist - Download for Free
